diff --git a/README.md b/README.md
index bfc7f96bb8..4edd01bb51 100644
--- a/README.md
+++ b/README.md
@@ -41,7 +41,21 @@
# Description
-`Prowler` is an Open Source security tool to perform AWS, GCP and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
+**Prowler** is an Open Source security tool to perform AWS, Azure, Google Cloud and Kubernetes security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness, and also remediations! We have Prowler CLI (Command Line Interface) that we call Prowler Open Source and a service on top of it that we call Prowler SaaS.
+
+## Prowler CLI
+
+```console
+prowler
+```
+
+
+## Prowler Dashboard
+
+```console
+prowler dashboard
+```
+
It contains hundreds of controls covering CIS, NIST 800, NIST CSF, CISA, RBI, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, GXP, AWS Well-Architected Framework Security Pillar, AWS Foundational Technical Review (FTR), ENS (Spanish National Security Scheme) and your custom security frameworks.
@@ -52,14 +66,7 @@ It contains hundreds of controls covering CIS, NIST 800, NIST CSF, CISA, RBI, Fe
| Azure | 127 | 16 -> `prowler azure --list-services` | 2 -> `prowler azure --list-compliance` | 2 -> `prowler azure --list-categories` |
| Kubernetes | 83 | 7 -> `prowler kubernetes --list-services` | 1 -> `prowler kubernetes --list-compliance` | 7 -> `prowler kubernetes --list-categories` |
-# 📖 Documentation
-
-The full documentation can now be found at [https://docs.prowler.com](https://docs.prowler.com/projects/prowler-open-source/en/latest/)
-
-## Looking for Prowler v2 documentation?
-For Prowler v2 Documentation, please go to https://github.com/prowler-cloud/prowler/tree/2.12.1.
-
-# ⚙️ Install
+# 💻 Installation
## Pip package
Prowler is available as a project in [PyPI](https://pypi.org/project/prowler-cloud/), thus can be installed using pip with Python >= 3.9, < 3.13:
@@ -74,9 +81,11 @@ More details at [https://docs.prowler.com](https://docs.prowler.com/projects/pro
The available versions of Prowler are the following:
-- `latest`: in sync with master branch (bear in mind that it is not a stable version)
+- `latest`: in sync with `master` branch (bear in mind that it is not a stable version)
+- `v3-latest`: in sync with `v3` branch (bear in mind that it is not a stable version)
- `` (release): you can find the releases [here](https://github.com/prowler-cloud/prowler/releases), those are stable releases.
- `stable`: this tag always point to the latest release.
+- `v3-stable`: this tag always point to the latest release for v3.
The container images are available here:
@@ -97,200 +106,30 @@ python prowler.py -v
# 📐✏️ High level architecture
-You can run Prowler from your workstation, an EC2 instance, Fargate or any other container, Codebuild, CloudShell and Cloud9.
+You can run Prowler from your workstation, a Kubernetes Job, a Google Compute Engine, an Azure VM, an EC2 instance, Fargate or any other container, CloudShell and many more.
-
+
-# 📝 Requirements
+# Deprecations from v3
-Prowler has been written in Python using the [AWS SDK (Boto3)](https://boto3.amazonaws.com/v1/documentation/api/latest/index.html#), [Azure SDK](https://azure.github.io/azure-sdk-for-python/) and [GCP API Python Client](https://github.com/googleapis/google-api-python-client/).
-## AWS
+## General
+- `Allowlist` now is called `Mutelist`.
+- The `--quiet` option has been deprecated, now use the `--status` flag to select the finding's status you want to get from PASS, FAIL or MANUAL.
+- All `INFO` finding's status has changed to `MANUAL`.
+- The CSV output format is common for all the providers.
-Since Prowler uses AWS Credentials under the hood, you can follow any authentication method as described [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-precedence).
-Make sure you have properly configured your AWS-CLI with a valid Access Key and Region or declare AWS variables properly (or instance profile/role):
-
- ```console
- aws configure
- ```
-
- or
-
- ```console
- export AWS_ACCESS_KEY_ID="ASXXXXXXX"
- export AWS_SECRET_ACCESS_KEY="XXXXXXXXX"
- export AWS_SESSION_TOKEN="XXXXXXXXX"
- ```
-
-Those credentials must be associated to a user or role with proper permissions to do all checks. To make sure, add the following AWS managed policies to the user or role being used:
-
- - `arn:aws:iam::aws:policy/SecurityAudit`
- - `arn:aws:iam::aws:policy/job-function/ViewOnlyAccess`
-
- > Moreover, some read-only additional permissions are needed for several checks, make sure you attach also the custom policy [prowler-additions-policy.json](https://github.com/prowler-cloud/prowler/blob/master/permissions/prowler-additions-policy.json) to the role you are using.
-
- > If you want Prowler to send findings to [AWS Security Hub](https://aws.amazon.com/security-hub), make sure you also attach the custom policy [prowler-security-hub.json](https://github.com/prowler-cloud/prowler/blob/master/permissions/prowler-security-hub.json).
-
- ## Azure
-
- Prowler for Azure supports the following authentication types:
-
-- Service principal authentication by environment variables (Enterprise Application)
-- Current az cli credentials stored
-- Interactive browser authentication
-- Managed identity authentication
-
-### Service Principal authentication
-
-To allow Prowler assume the service principal identity to start the scan, it is needed to configure the following environment variables:
-
-```console
-export AZURE_CLIENT_ID="XXXXXXXXX"
-export AZURE_TENANT_ID="XXXXXXXXX"
-export AZURE_CLIENT_SECRET="XXXXXXX"
-```
-
-If you try to execute Prowler with the `--sp-env-auth` flag and those variables are empty or not exported, the execution is going to fail.
-### AZ CLI / Browser / Managed Identity authentication
-
-The other three cases do not need additional configuration, `--az-cli-auth` and `--managed-identity-auth` are automated options, `--browser-auth` needs the user to authenticate using the default browser to start the scan. Also `--browser-auth` needs the tenant id to be specified with `--tenant-id`.
-
-### Permissions
-
-To use each one, you need to pass the proper flag to the execution. Prowler for Azure handles two types of permission scopes, which are:
-
-- **Azure Active Directory permissions**: Used to retrieve metadata from the identity assumed by Prowler and future AAD checks (not mandatory to have access to execute the tool)
-- **Subscription scope permissions**: Required to launch the checks against your resources, mandatory to launch the tool.
-
-
-#### Azure Active Directory scope
-
-Azure Active Directory (AAD) permissions required by the tool are the following:
-
-- `Directory.Read.All`
-- `Policy.Read.All`
-
-
-#### Subscriptions scope
-
-Regarding the subscription scope, Prowler by default scans all the subscriptions that is able to list, so it is required to add the following RBAC builtin roles per subscription to the entity that is going to be assumed by the tool:
-
-- `Security Reader`
-- `Reader`
-
-
-## Google Cloud Platform
-
-Prowler will follow the same credentials search as [Google authentication libraries](https://cloud.google.com/docs/authentication/application-default-credentials#search_order):
-
-1. [GOOGLE_APPLICATION_CREDENTIALS environment variable](https://cloud.google.com/docs/authentication/application-default-credentials#GAC)
-2. [User credentials set up by using the Google Cloud CLI](https://cloud.google.com/docs/authentication/application-default-credentials#personal)
-3. [The attached service account, returned by the metadata server](https://cloud.google.com/docs/authentication/application-default-credentials#attached-sa)
-
-Those credentials must be associated to a user or service account with proper permissions to do all checks. To make sure, add the `Viewer` role to the member associated with the credentials.
-
-> By default, `prowler` will scan all accessible GCP Projects, use flag `--project-ids` to specify the projects to be scanned.
-
-# 💻 Basic Usage
-
-To run prowler, you will need to specify the provider (e.g aws or azure):
-
-```console
-prowler
-```
-
-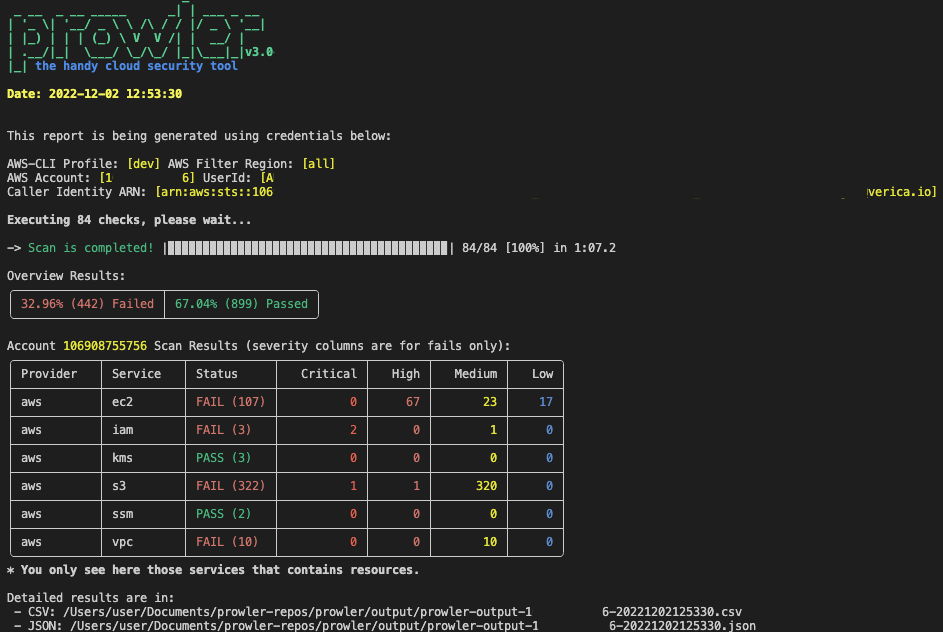
-
-> Running the `prowler` command without options will use your environment variable credentials.
-
-By default, prowler will generate a CSV, a JSON and a HTML report, however you can generate JSON-ASFF (only for AWS Security Hub) report with `-M` or `--output-modes`:
-
-```console
-prowler -M csv json json-asff html
-```
-
-The html report will be located in the `output` directory as the other files and it will look like:
-
-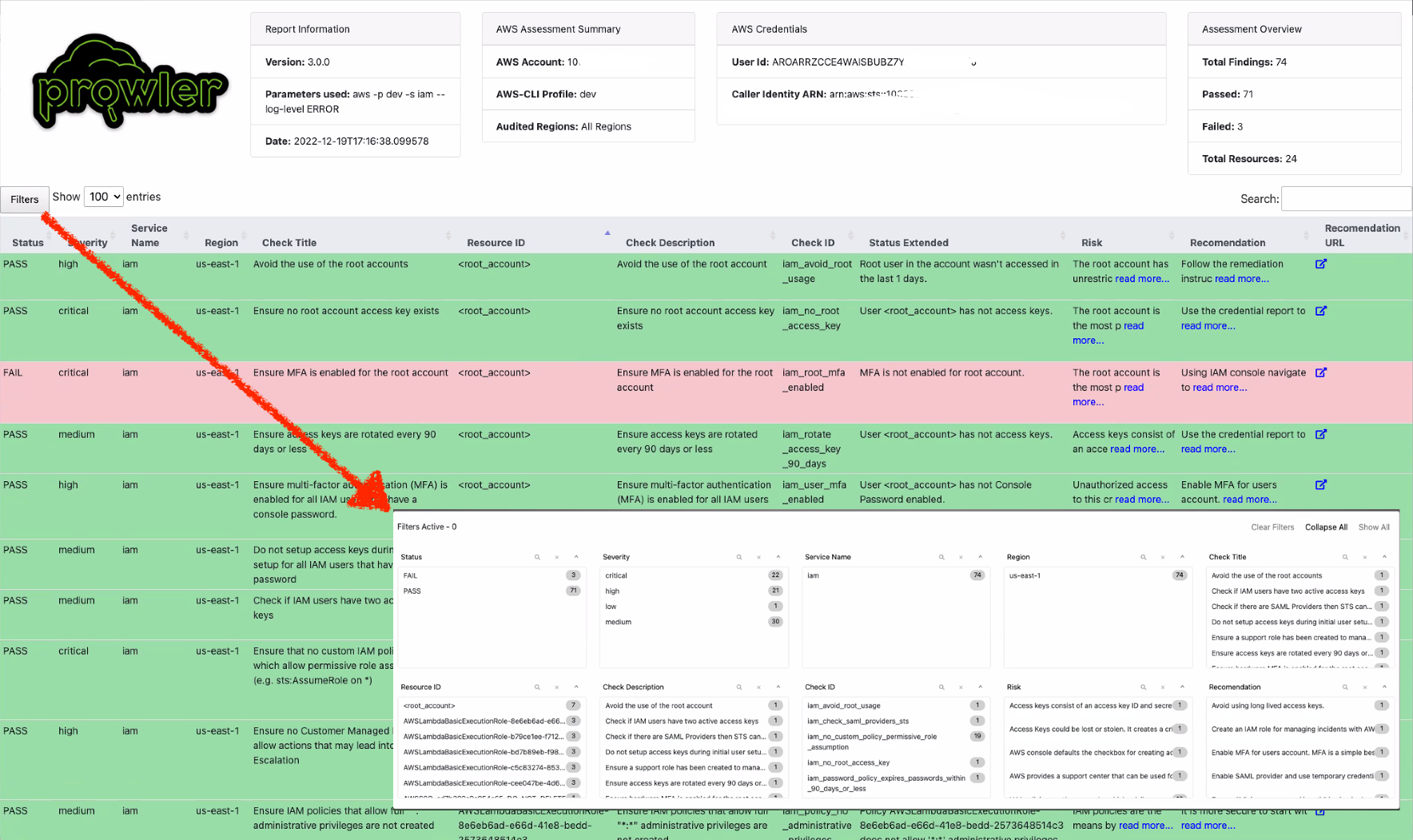
-
-You can use `-l`/`--list-checks` or `--list-services` to list all available checks or services within the provider.
-
-```console
-prowler --list-checks
-prowler --list-services
-```
-
-For executing specific checks or services you can use options `-c`/`--checks` or `-s`/`--services`:
-
-```console
-prowler aws --checks s3_bucket_public_access
-prowler aws --services s3 ec2
-```
-
-Also, checks and services can be excluded with options `-e`/`--excluded-checks` or `--excluded-services`:
-
-```console
-prowler aws --excluded-checks s3_bucket_public_access
-prowler aws --excluded-services s3 ec2
-```
-
-You can always use `-h`/`--help` to access to the usage information and all the possible options:
-
-```console
-prowler -h
-```
-
-## Checks Configurations
-Several Prowler's checks have user configurable variables that can be modified in a common **configuration file**.
-This file can be found in the following path:
-```
-prowler/config/config.yaml
-```
+We have deprecated some of our outputs formats:
+- The HTML is replaced for the new Prowler Dashboard, run `prowler dashboard`.
+- The native JSON is replaced for the JSON [OCSF](https://schema.ocsf.io/) v1.1.0, common for all the providers.
## AWS
+- Deprecate the AWS flag --sts-endpoint-region since we use AWS STS regional tokens.
+- To send only FAILS to AWS Security Hub, now use either `--send-sh-only-fails` or `--security-hub --status FAIL`.
-Use a custom AWS profile with `-p`/`--profile` and/or AWS regions which you want to audit with `-f`/`--filter-region`:
-```console
-prowler aws --profile custom-profile -f us-east-1 eu-south-2
-```
-> By default, `prowler` will scan all AWS regions.
+# 📖 Documentation
-## Azure
-
-With Azure you need to specify which auth method is going to be used:
-
-```console
-prowler azure [--sp-env-auth, --az-cli-auth, --browser-auth, --managed-identity-auth]
-```
-> By default, `prowler` will scan all Azure subscriptions.
-
-## Google Cloud Platform
-
-Optionally, you can provide the location of an application credential JSON file with the following argument:
-
-```console
-prowler gcp --credentials-file path
-```
-> By default, `prowler` will scan all accessible GCP Projects, use flag `--project-ids` to specify the projects to be scanned.
-
-## Kubernetes
-
-For non in-cluster execution, you can provide the location of the KubeConfig file with the following argument:
-
-```console
-prowler kubernetes --kubeconfig-file path
-```
-
-For in-cluster execution, you can use the supplied yaml to run Prowler as a job:
-```console
-kubectl apply -f job.yaml
-kubectl apply -f prowler-role.yaml
-kubectl apply -f prowler-rolebinding.yaml
-kubectl get pods --> prowler-XXXXX
-kubectl logs prowler-XXXXX
-```
-
-> By default, `prowler` will scan all namespaces in your active Kubernetes context, use flag `--context` to specify the context to be scanned and `--namespaces` to specify the namespaces to be scanned.
+Install, Usage, Tutorials and Developer Guide is at https://docs.prowler.com/
# 📃 License
diff --git a/contrib/cloudshell/cloudshell-installation.sh b/contrib/cloudshell/cloudshell-installation.sh
index b853419b0f..4672a75d64 100644
--- a/contrib/cloudshell/cloudshell-installation.sh
+++ b/contrib/cloudshell/cloudshell-installation.sh
@@ -4,5 +4,5 @@ sudo bash
adduser prowler
su prowler
pip install prowler
-cd /tmp || exit
+cd /tmp
prowler aws
diff --git a/docs/img/architecture.png b/docs/img/architecture.png
index 43b764cde8..53b9b60156 100644
Binary files a/docs/img/architecture.png and b/docs/img/architecture.png differ
diff --git a/docs/img/dashboard.png b/docs/img/dashboard.png
new file mode 100644
index 0000000000..f6f129e2b1
Binary files /dev/null and b/docs/img/dashboard.png differ
diff --git a/docs/img/short-display.png b/docs/img/short-display.png
index ebd3c51f7a..a36364acc0 100644
Binary files a/docs/img/short-display.png and b/docs/img/short-display.png differ
diff --git a/docs/index.md b/docs/index.md
index 28fc033cac..61935ad5cb 100644
--- a/docs/index.md
+++ b/docs/index.md
@@ -1,8 +1,20 @@
-**Prowler** is an Open Source security tool to perform AWS, Azure and Google Cloud security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. We have Prowler CLI (Command Line Interface) that we call Prowler Open Source and a service on top of it that we call Prowler SaaS.
+**Prowler** is an Open Source security tool to perform AWS, Azure, Google Cloud and Kubernetes security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness, and also remediations! We have Prowler CLI (Command Line Interface) that we call Prowler Open Source and a service on top of it that we call Prowler SaaS.
-
+## Prowler CLI
-Prowler offers hundreds of controls covering more than 25 standards and compliance frameworks like CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.
+```console
+prowler
+```
+
+
+## Prowler Dashboard
+
+```console
+prowler dashboard
+```
+
+
+It contains hundreds of controls covering CIS, NIST 800, NIST CSF, CISA, RBI, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, GXP, AWS Well-Architected Framework Security Pillar, AWS Foundational Technical Review (FTR), ENS (Spanish National Security Scheme) and your custom security frameworks.
## Quick Start
### Installation
@@ -124,12 +136,12 @@ Prowler is available as a project in [PyPI](https://pypi.org/project/prowler/),
adduser prowler
su prowler
pip install prowler
- cd /tmp || exit
+ cd /tmp
prowler aws
```
???+ note
- To download the results from AWS CloudShell, select Actions -> Download File and add the full path of each file. For the CSV file it will be something like `/home/cloudshell-user/output/prowler-output-123456789012-20221220191331.csv`
+ To download the results from AWS CloudShell, select Actions -> Download File and add the full path of each file. For the CSV file it will be something like `/tmp/output/prowler-output-123456789012-20221220191331.csv`
=== "Azure CloudShell"
@@ -148,9 +160,11 @@ Prowler is available as a project in [PyPI](https://pypi.org/project/prowler/),
The available versions of Prowler are the following:
-- `latest`: in sync with master branch (bear in mind that it is not a stable version)
+- `latest`: in sync with `master` branch (bear in mind that it is not a stable version)
+- `v3-latest`: in sync with `v3` branch (bear in mind that it is not a stable version)
- `` (release): you can find the releases [here](https://github.com/prowler-cloud/prowler/releases), those are stable releases.
- `stable`: this tag always point to the latest release.
+- `v3-stable`: this tag always point to the latest release for v3.
The container images are available here:
@@ -159,9 +173,27 @@ The container images are available here:
## High level architecture
-You can run Prowler from your workstation, an EC2 instance, Fargate or any other container, Codebuild, CloudShell, Cloud9 and many more.
+You can run Prowler from your workstation, a Kubernetes Job, a Google Compute Engine, an Azure VM, an EC2 instance, Fargate or any other container, CloudShell and many more.

+
+## Deprecations from v3
+
+### General
+- `Allowlist` now is called `Mutelist`.
+- The `--quiet` option has been deprecated, now use the `--status` flag to select the finding's status you want to get from PASS, FAIL or MANUAL.
+- All `INFO` finding's status has changed to `MANUAL`.
+- The CSV output format is common for all the providers.
+
+We have deprecated some of our outputs formats:
+
+- The HTML is replaced for the new Prowler Dashboard, run `prowler dashboard`.
+- The native JSON is replaced for the JSON [OCSF](https://schema.ocsf.io/) v1.1.0, common for all the providers.
+
+### AWS
+- Deprecate the AWS flag --sts-endpoint-region since we use AWS STS regional tokens.
+- To send only FAILS to AWS Security Hub, now use either `--send-sh-only-fails` or `--security-hub --status FAIL`.
+
## Basic Usage
To run Prowler, you will need to specify the provider (e.g `aws`, `gcp`, `azure` or `kubernetes`):
@@ -293,9 +325,9 @@ prowler kubernetes --kubeconfig-file path
For in-cluster execution, you can use the supplied yaml to run Prowler as a job:
```console
-kubectl apply -f job.yaml
-kubectl apply -f prowler-role.yaml
-kubectl apply -f prowler-rolebinding.yaml
+kubectl apply -f kubernetes/job.yaml
+kubectl apply -f kubernetes/prowler-role.yaml
+kubectl apply -f kubernetes/prowler-rolebinding.yaml
kubectl get pods --> prowler-XXXXX
kubectl logs prowler-XXXXX
```
diff --git a/docs/tutorials/aws/cloudshell.md b/docs/tutorials/aws/cloudshell.md
index 975cc50b20..78d47bfb08 100644
--- a/docs/tutorials/aws/cloudshell.md
+++ b/docs/tutorials/aws/cloudshell.md
@@ -7,7 +7,7 @@ sudo bash
adduser prowler
su prowler
pip install prowler
-cd /tmp || exit
+cd /tmp
prowler aws
```
diff --git a/docs/tutorials/aws/v2_to_v3_checks_mapping.md b/docs/tutorials/aws/v2_to_v3_checks_mapping.md
index b616c3bff6..92335c225c 100644
--- a/docs/tutorials/aws/v2_to_v3_checks_mapping.md
+++ b/docs/tutorials/aws/v2_to_v3_checks_mapping.md
@@ -1,11 +1,11 @@
-# Check mapping between Prowler v3 and v2
+# Check mapping between Prowler v4/v3 and v2
-Prowler v3 comes with different identifiers but we maintained the same checks that were implemented in v2. The reason for this change is because in previous versions of Prowler, check names were mostly based on CIS Benchmark for AWS. In v3 all checks are independent from any security framework and they have its own name and ID.
+Prowler v3 comes with different identifiers but we maintained the same checks that were implemented in v2. The reason for this change is because in previous versions of Prowler, check names were mostly based on CIS Benchmark for AWS. In v4 and v3 all checks are independent from any security framework and they have its own name and ID.
-If you need more information about how new compliance implementation works in Prowler v3 see [Compliance](../compliance.md) section.
+If you need more information about how new compliance implementation works in Prowler v4 and v3 see [Compliance](../compliance.md) section.
```
-checks_v3_to_v2_mapping = {
+checks_v4_v3_to_v2_mapping = {
"accessanalyzer_enabled_without_findings": "extra769",
"account_maintain_current_contact_details": "check117",
"account_security_contact_information_is_registered": "check118",
diff --git a/mkdocs.yml b/mkdocs.yml
index 7bc8c28f68..6609a1a9a8 100644
--- a/mkdocs.yml
+++ b/mkdocs.yml
@@ -58,7 +58,7 @@ nav:
- Scan Multiple AWS Accounts: tutorials/aws/multiaccount.md
- Send reports to AWS S3: tutorials/aws/s3.md
- AWS CloudShell: tutorials/aws/cloudshell.md
- - Checks v2 to v3 Mapping: tutorials/aws/v2_to_v3_checks_mapping.md
+ - Checks v2 to v3 and v4 Mapping: tutorials/aws/v2_to_v3_checks_mapping.md
- Tag-based Scan: tutorials/aws/tag-based-scan.md
- Resource ARNs based Scan: tutorials/aws/resource-arn-based-scan.md
- Boto3 Configuration: tutorials/aws/boto3-configuration.md