feat(docs): add new docs and readme (#1529)
Co-authored-by: sergargar <sergio@verica.io> Co-authored-by: n4ch04 <nachor1992@gmail.com>
3
.gitignore
vendored
@@ -41,8 +41,5 @@ junit-reports/
|
||||
.terraform*
|
||||
*.tfstate
|
||||
|
||||
# Text
|
||||
*.txt
|
||||
|
||||
# .env
|
||||
.env*
|
||||
|
||||
@@ -1,5 +0,0 @@
|
||||
```
|
||||
./prowler -l # to see all available checks and their groups.
|
||||
./prowler -L # to see all available groups only.
|
||||
./prowler -l -g groupname # to see checks in a particular group
|
||||
```
|
||||
811
README.md
@@ -1,22 +1,25 @@
|
||||
<p align="center">
|
||||
<img align="center" src="docs/images/prowler-pro-dark.png#gh-dark-mode-only" width="150" height="36">
|
||||
<img align="center" src="docs/images/prowler-pro-light.png#gh-light-mode-only" width="15%" height="15%">
|
||||
<img align="center" src="docs/img/prowler-pro-dark.png#gh-dark-mode-only" width="150" height="36">
|
||||
<img align="center" src="docs/img/prowler-pro-light.png#gh-light-mode-only" width="15%" height="15%">
|
||||
</p>
|
||||
<p align="center">
|
||||
<b><i>   Explore the Pro version of Prowler at <a href="https://prowler.pro">prowler.pro</a></i></b>
|
||||
<b><i>    See all the things you and your team can do with ProwlerPro at <a href="https://prowler.pro">prowler.pro</a></i></b>
|
||||
</p>
|
||||
<hr>
|
||||
<p align="center">
|
||||
<img src="https://user-images.githubusercontent.com/3985464/113734260-7ba06900-96fb-11eb-82bc-d4f68a1e2710.png" />
|
||||
</p>
|
||||
<p align="center">
|
||||
<a href="https://discord.gg/UjSMCVnxSB"><img alt="Discord Shield" src="https://img.shields.io/discord/807208614288818196"></a>
|
||||
<a href="https://join.slack.com/t/prowler-workspace/shared_invite/zt-1hix76xsl-2uq222JIXrC7Q8It~9ZNog"><img alt="Slack Shield" src="https://img.shields.io/badge/slack-prowler-brightgreen.svg?logo=slack"></a>
|
||||
<a href="https://pypi.org/project/prowler-cloud/"><img alt="Python Version" src="https://img.shields.io/pypi/v/prowler-cloud.svg"></a>
|
||||
<a href="https://pypi.python.org/pypi/prowler-cloud/"><img alt="Python Version" src="https://img.shields.io/pypi/pyversions/prowler-cloud.svg"></a>
|
||||
<a href="https://hub.docker.com/r/toniblyx/prowler"><img alt="Docker Pulls" src="https://img.shields.io/docker/pulls/toniblyx/prowler"></a>
|
||||
<a href="https://hub.docker.com/r/toniblyx/prowler"><img alt="Docker" src="https://img.shields.io/docker/cloud/build/toniblyx/prowler"></a>
|
||||
<a href="https://hub.docker.com/r/toniblyx/prowler"><img alt="Docker" src="https://img.shields.io/docker/image-size/toniblyx/prowler"></a>
|
||||
<a href="https://gallery.ecr.aws/o4g1s5r6/prowler"><img width="120" height=19" alt="AWS ECR Gallery" src="https://user-images.githubusercontent.com/3985464/151531396-b6535a68-c907-44eb-95a1-a09508178616.png"></a>
|
||||
</p>
|
||||
<p align="center">
|
||||
<a href="https://github.com/prowler-cloud/prowler"><img alt="Repo size" src="https://img.shields.io/github/repo-size/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler"><img alt="Lines" src="https://img.shields.io/tokei/lines/github/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler/issues"><img alt="Issues" src="https://img.shields.io/github/issues/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler/releases"><img alt="Version" src="https://img.shields.io/github/v/release/prowler-cloud/prowler?include_prereleases"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler/releases"><img alt="Version" src="https://img.shields.io/github/release-date/prowler-cloud/prowler"></a>
|
||||
@@ -25,778 +28,132 @@
|
||||
<a href="https://twitter.com/ToniBlyx"><img alt="Twitter" src="https://img.shields.io/twitter/follow/toniblyx?style=social"></a>
|
||||
</p>
|
||||
|
||||
<p align="center">
|
||||
<i>Prowler</i> is an Open Source security tool to perform AWS security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It contains more than 200 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custome security frameworks.
|
||||
</p>
|
||||
# Description
|
||||
|
||||
## Table of Contents
|
||||
`Prowler` is an Open Source security tool to perform AWS and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
|
||||
|
||||
- [Description](#description)
|
||||
- [Features](#features)
|
||||
- [High level architecture](#high-level-architecture)
|
||||
- [Requirements and Installation](#requirements-and-installation)
|
||||
- [Usage](#usage)
|
||||
- [Screenshots](#screenshots)
|
||||
- [Advanced Usage](#advanced-usage)
|
||||
- [Security Hub integration](#security-hub-integration)
|
||||
- [CodeBuild deployment](#codebuild-deployment)
|
||||
- [Allowlist](#allowlist-or-remove-a-fail-from-resources)
|
||||
- [Fix](#how-to-fix-every-fail)
|
||||
- [Troubleshooting](#troubleshooting)
|
||||
- [Extras](#extras)
|
||||
- [Forensics Ready Checks](#forensics-ready-checks)
|
||||
- [GDPR Checks](#gdpr-checks)
|
||||
- [HIPAA Checks](#hipaa-checks)
|
||||
- [Trust Boundaries Checks](#trust-boundaries-checks)
|
||||
- [Multi Account and Continuous Monitoring](util/org-multi-account/README.md)
|
||||
- [Custom Checks](#custom-checks)
|
||||
- [Third Party Integrations](#third-party-integrations)
|
||||
- [Full list of checks and groups](/LIST_OF_CHECKS_AND_GROUPS.md)
|
||||
- [License](#license)
|
||||
It contains hundreds of controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.
|
||||
|
||||
## Description
|
||||
# ⚙️ Install
|
||||
|
||||
Prowler is a command line tool that helps you with AWS security assessment, auditing, hardening and incident response.
|
||||
```console
|
||||
pip install prowler-cloud
|
||||
prowler -v
|
||||
```
|
||||
|
||||
It follows guidelines of the CIS Amazon Web Services Foundations Benchmark (49 checks) and has more than 100 additional checks including related to GDPR, HIPAA, PCI-DSS, ISO-27001, FFIEC, SOC2 and others.
|
||||
## Prowler container versions
|
||||
|
||||
Read more about [CIS Amazon Web Services Foundations Benchmark v1.2.0 - 05-23-2018](https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf)
|
||||
The available versions of Prowler are the following:
|
||||
|
||||
## Features
|
||||
- latest: in sync with master branch (bear in mind that it is not a stable version)
|
||||
- <x.y.z> (release): you can find the releases [here](https://github.com/prowler-cloud/prowler/releases), those are stable releases.
|
||||
- stable: this tag always point to the latest release.
|
||||
|
||||
+200 checks covering security best practices across all AWS regions and most of AWS services and related to the next groups:
|
||||
The container images are available here:
|
||||
|
||||
- Identity and Access Management [group1]
|
||||
- Logging [group2]
|
||||
- Monitoring [group3]
|
||||
- Networking [group4]
|
||||
- CIS Level 1 [cislevel1]
|
||||
- CIS Level 2 [cislevel2]
|
||||
- Extras *see Extras section* [extras]
|
||||
- Forensics related group of checks [forensics-ready]
|
||||
- GDPR [gdpr] Read more [here](#gdpr-checks)
|
||||
- HIPAA [hipaa] Read more [here](#hipaa-checks)
|
||||
- Trust Boundaries [trustboundaries] Read more [here](#trust-boundaries-checks)
|
||||
- Secrets
|
||||
- Internet exposed resources
|
||||
- EKS-CIS
|
||||
- Also includes PCI-DSS, ISO-27001, FFIEC, SOC2, ENS (Esquema Nacional de Seguridad of Spain).
|
||||
- AWS FTR [FTR] Read more [here](#aws-ftr-checks)
|
||||
- [DockerHub](https://hub.docker.com/r/toniblyx/prowler/tags)
|
||||
- [AWS Public ECR](https://gallery.ecr.aws/o4g1s5r6/prowler)
|
||||
|
||||
With Prowler you can:
|
||||
|
||||
- Get a direct colorful or monochrome report
|
||||
- A HTML, CSV, JUNIT, JSON or JSON ASFF (Security Hub) format report
|
||||
- Send findings directly to Security Hub
|
||||
- Run specific checks and groups or create your own
|
||||
- Check multiple AWS accounts in parallel or sequentially
|
||||
- And more! Read examples below
|
||||
|
||||
## High level architecture
|
||||
# 📐✏️ High level architecture
|
||||
|
||||
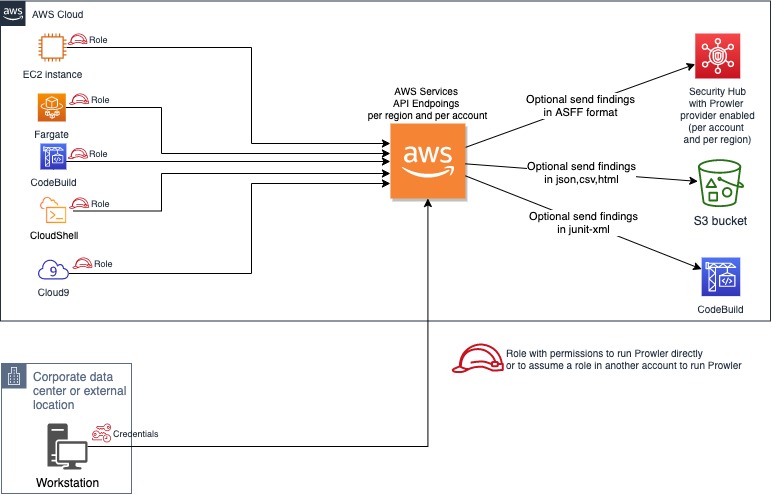
You can run Prowler from your workstation, an EC2 instance, Fargate or any other container, Codebuild, CloudShell and Cloud9.
|
||||
|
||||
|
||||
## Requirements and Installation
|
||||

|
||||
|
||||
Prowler has been written in bash using AWS-CLI underneath and it works in Linux, Mac OS or Windows with cygwin or virtualization. Also requires `jq` and `detect-secrets` to work properly.
|
||||
# 📝 Requirements
|
||||
|
||||
- Make sure the latest version of AWS-CLI is installed. It works with either v1 or v2, however _latest v2 is recommended if using new regions since they require STS v2 token_, and other components needed, with Python pip already installed.
|
||||
Prowler has been written in Python using the [AWS SDK (Boto3)](https://boto3.amazonaws.com/v1/documentation/api/latest/index.html#) and [Azure SDK](https://azure.github.io/azure-sdk-for-python/).
|
||||
## AWS
|
||||
|
||||
- For Amazon Linux (`yum` based Linux distributions and AWS CLI v2):
|
||||
```
|
||||
sudo yum update -y
|
||||
sudo yum remove -y awscli
|
||||
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
|
||||
unzip awscliv2.zip
|
||||
sudo ./aws/install
|
||||
sudo yum install -y python3 jq git
|
||||
sudo pip3 install detect-secrets==1.0.3
|
||||
git clone https://github.com/prowler-cloud/prowler
|
||||
```
|
||||
- For Ubuntu Linux (`apt` based Linux distributions and AWS CLI v2):
|
||||
```
|
||||
sudo apt update
|
||||
sudo apt install python3 python3-pip jq git zip
|
||||
pip install detect-secrets==1.0.3
|
||||
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
|
||||
unzip awscliv2.zip
|
||||
sudo ./aws/install
|
||||
git clone https://github.com/prowler-cloud/prowler
|
||||
```
|
||||
Since Prowler uses AWS Credentials under the hood, you can follow any authentication method as described [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-precedence).
|
||||
Make sure you have properly configured your AWS-CLI with a valid Access Key and Region or declare AWS variables properly (or instance profile/role):
|
||||
|
||||
> NOTE: detect-secrets Yelp version is no longer supported, the one from IBM is mantained now. Use the one mentioned below or the specific Yelp version 1.0.3 to make sure it works as expected (`pip install detect-secrets==1.0.3`):
|
||||
```sh
|
||||
pip install "git+https://github.com/ibm/detect-secrets.git@master#egg=detect-secrets"
|
||||
```
|
||||
```console
|
||||
aws configure
|
||||
```
|
||||
|
||||
AWS-CLI can be also installed it using other methods, refer to official documentation for more details: <https://aws.amazon.com/cli/>, but `detect-secrets` has to be installed using `pip` or `pip3`.
|
||||
or
|
||||
|
||||
- Once Prowler repository is cloned, get into the folder and you can run it:
|
||||
```console
|
||||
export AWS_ACCESS_KEY_ID="ASXXXXXXX"
|
||||
export AWS_SECRET_ACCESS_KEY="XXXXXXXXX"
|
||||
export AWS_SESSION_TOKEN="XXXXXXXXX"
|
||||
```
|
||||
|
||||
```sh
|
||||
cd prowler
|
||||
./prowler
|
||||
```
|
||||
Those credentials must be associated to a user or role with proper permissions to do all checks. To make sure, add the following AWS managed policies to the user or role being used:
|
||||
|
||||
- Since Prowler users AWS CLI under the hood, you can follow any authentication method as described [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-precedence). Make sure you have properly configured your AWS-CLI with a valid Access Key and Region or declare AWS variables properly (or instance profile/role):
|
||||
- arn:aws:iam::aws:policy/SecurityAudit
|
||||
- arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
|
||||
```sh
|
||||
aws configure
|
||||
```
|
||||
> Moreover, some read-only additional permissions are needed for several checks, make sure you attach also the custom policy [prowler-additions-policy.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-additions-policy.json) to the role you are using.
|
||||
|
||||
or
|
||||
> If you want Prowler to send findings to [AWS Security Hub](https://aws.amazon.com/security-hub), make sure you also attach the custom policy [prowler-security-hub.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-security-hub.json).
|
||||
|
||||
```sh
|
||||
export AWS_ACCESS_KEY_ID="ASXXXXXXX"
|
||||
export AWS_SECRET_ACCESS_KEY="XXXXXXXXX"
|
||||
export AWS_SESSION_TOKEN="XXXXXXXXX"
|
||||
```
|
||||
|
||||
- Those credentials must be associated to a user or role with proper permissions to do all checks. To make sure, add the AWS managed policies, SecurityAudit and ViewOnlyAccess, to the user or role being used. Policy ARNs are:
|
||||
# 💻 Basic Usage
|
||||
|
||||
```sh
|
||||
arn:aws:iam::aws:policy/SecurityAudit
|
||||
arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
```
|
||||
To run prowler, you will need to specify the provider (e.g aws or azure):
|
||||
|
||||
> Additional permissions needed: to make sure Prowler can scan all services included in the group *Extras*, make sure you attach also the custom policy [prowler-additions-policy.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-additions-policy.json) to the role you are using. If you want Prowler to send findings to [AWS Security Hub](https://aws.amazon.com/security-hub), make sure you also attach the custom policy [prowler-security-hub.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-security-hub.json).
|
||||
|
||||
## Usage
|
||||
|
||||
1. Run the `prowler` command without options (it will use your environment variable credentials if they exist or will default to using the `~/.aws/credentials` file and run checks over all regions when needed. The default region is us-east-1):
|
||||
|
||||
```sh
|
||||
./prowler
|
||||
```
|
||||
|
||||
Use `-l` to list all available checks and the groups (sections) that reference them. To list all groups use `-L` and to list content of a group use `-l -g <groupname>`.
|
||||
|
||||
If you want to avoid installing dependencies run it using Docker:
|
||||
|
||||
```sh
|
||||
docker run -ti --rm --name prowler --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest
|
||||
```
|
||||
|
||||
In case you want to get reports created by Prowler use docker volume option like in the example below:
|
||||
```sh
|
||||
docker run -ti --rm -v /your/local/output:/prowler/output --name prowler --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest -g hipaa -M csv,json,html
|
||||
```
|
||||
|
||||
1. For custom AWS-CLI profile and region, use the following: (it will use your custom profile and run checks over all regions when needed):
|
||||
|
||||
```sh
|
||||
./prowler -p custom-profile -r us-east-1
|
||||
```
|
||||
|
||||
1. For a single check use option `-c`:
|
||||
|
||||
```sh
|
||||
./prowler -c check310
|
||||
```
|
||||
|
||||
With Docker:
|
||||
|
||||
```sh
|
||||
docker run -ti --rm --name prowler --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest "-c check310"
|
||||
```
|
||||
|
||||
or multiple checks separated by comma:
|
||||
|
||||
```sh
|
||||
./prowler -c check310,check722
|
||||
```
|
||||
|
||||
or all checks but some of them:
|
||||
|
||||
```sh
|
||||
./prowler -e check42,check43
|
||||
```
|
||||
|
||||
or for custom profile and region:
|
||||
|
||||
```sh
|
||||
./prowler -p custom-profile -r us-east-1 -c check11
|
||||
```
|
||||
|
||||
or for a group of checks use group name:
|
||||
|
||||
```sh
|
||||
./prowler -g group1 # for iam related checks
|
||||
```
|
||||
|
||||
or exclude some checks in the group:
|
||||
|
||||
```sh
|
||||
./prowler -g group4 -e check42,check43
|
||||
```
|
||||
|
||||
Valid check numbers are based on the AWS CIS Benchmark guide, so 1.1 is check11 and 3.10 is check310
|
||||
|
||||
### Regions
|
||||
|
||||
By default, Prowler scans all opt-in regions available, that might take a long execution time depending on the number of resources and regions used. Same applies for GovCloud or China regions. See below Advance usage for examples.
|
||||
|
||||
Prowler has two parameters related to regions: `-r` that is used query AWS services API endpoints (it uses `us-east-1` by default and required for GovCloud or China) and the option `-f` that is to filter those regions you only want to scan. For example if you want to scan Dublin only use `-f eu-west-1` and if you want to scan Dublin and Ohio `-f eu-west-1,us-east-1`, note the regions are separated by a comma deliminator (it can be used as before with `-f 'eu-west-1,us-east-1'`).
|
||||
|
||||
## Screenshots
|
||||
|
||||
- Sample screenshot of default console report first lines of command `./prowler`:
|
||||
|
||||
<img width="900" src="https://user-images.githubusercontent.com/3985464/141444529-84640bed-be0b-4112-80a2-2a43e3ebf53f.png">
|
||||
|
||||
- Sample screenshot of the html output `-M html`:
|
||||
|
||||
<img width="900" alt="Prowler html" src="https://user-images.githubusercontent.com/3985464/141443976-41d32cc2-533d-405a-92cb-affc3995d6ec.png">
|
||||
|
||||
- Sample screenshot of the Quicksight dashboard, see [quicksight-security-dashboard.workshop.aws](https://quicksight-security-dashboard.workshop.aws/):
|
||||
|
||||
<img width="900" alt="Prowler with Quicksight" src="https://user-images.githubusercontent.com/3985464/128932819-0156e838-286d-483c-b953-fda68a325a3d.png">
|
||||
|
||||
- Sample screenshot of the junit-xml output in CodeBuild `-M junit-xml`:
|
||||
|
||||
<img width="900" src="https://user-images.githubusercontent.com/3985464/113942824-ca382b00-9801-11eb-84e5-d7731548a7a9.png">
|
||||
|
||||
### Save your reports
|
||||
|
||||
1. If you want to save your report for later analysis thare are different ways, natively (supported text, mono, csv, json, json-asff, junit-xml and html, see note below for more info):
|
||||
|
||||
```sh
|
||||
./prowler -M csv
|
||||
```
|
||||
|
||||
or with multiple formats at the same time:
|
||||
|
||||
```sh
|
||||
./prowler -M csv,json,json-asff,html
|
||||
```
|
||||
|
||||
or just a group of checks in multiple formats:
|
||||
|
||||
```sh
|
||||
./prowler -g gdpr -M csv,json,json-asff
|
||||
```
|
||||
|
||||
or if you want a sorted and dynamic HTML report do:
|
||||
|
||||
```sh
|
||||
./prowler -M html
|
||||
```
|
||||
|
||||
Now `-M` creates a file inside the prowler `output` directory named `prowler-output-AWSACCOUNTID-YYYYMMDDHHMMSS.format`. You don't have to specify anything else, no pipes, no redirects.
|
||||
|
||||
or just saving the output to a file like below:
|
||||
|
||||
```sh
|
||||
./prowler -M mono > prowler-report.txt
|
||||
```
|
||||
|
||||
To generate JUnit report files, include the junit-xml format. This can be combined with any other format. Files are written inside a prowler root directory named `junit-reports`:
|
||||
|
||||
```sh
|
||||
./prowler -M text,junit-xml
|
||||
```
|
||||
|
||||
>Note about output formats to use with `-M`: "text" is the default one with colors, "mono" is like default one but monochrome, "csv" is comma separated values, "json" plain basic json (without comma between lines) and "json-asff" is also json with Amazon Security Finding Format that you can ship to Security Hub using `-S`.
|
||||
|
||||
To save your report in an S3 bucket, use `-B` to define a custom output bucket along with `-M` to define the output format that is going to be uploaded to S3:
|
||||
|
||||
```sh
|
||||
./prowler -M csv -B my-bucket/folder/
|
||||
```
|
||||
>In the case you do not want to use the assumed role credentials but the initial credentials to put the reports into the S3 bucket, use `-D` instead of `-B`. Make sure that the used credentials have s3:PutObject permissions in the S3 path where the reports are going to be uploaded.
|
||||
|
||||
When generating multiple formats and running using Docker, to retrieve the reports, bind a local directory to the container, e.g.:
|
||||
|
||||
```sh
|
||||
docker run -ti --rm --name prowler --volume "$(pwd)":/prowler/output --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest -M csv,json
|
||||
```
|
||||
|
||||
1. To perform an assessment based on CIS Profile Definitions you can use cislevel1 or cislevel2 with `-g` flag, more information about this [here, page 8](https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf):
|
||||
|
||||
```sh
|
||||
./prowler -g cislevel1
|
||||
```
|
||||
|
||||
1. If you want to run Prowler to check multiple AWS accounts in parallel (runs up to 4 simultaneously `-P 4`) but you may want to read below in Advanced Usage section to do so assuming a role:
|
||||
|
||||
```sh
|
||||
grep -E '^\[([0-9A-Aa-z_-]+)\]' ~/.aws/credentials | tr -d '][' | shuf | \
|
||||
xargs -n 1 -L 1 -I @ -r -P 4 ./prowler -p @ -M csv 2> /dev/null >> all-accounts.csv
|
||||
```
|
||||
|
||||
1. For help about usage run:
|
||||
|
||||
```
|
||||
./prowler -h
|
||||
```
|
||||
|
||||
## Advanced Usage
|
||||
|
||||
### Assume Role:
|
||||
|
||||
Prowler uses the AWS CLI underneath so it uses the same authentication methods. However, there are few ways to run Prowler against multiple accounts using IAM Assume Role feature depending on eachg use case. You can just set up your custom profile inside `~/.aws/config` with all needed information about the role to assume then call it with `./prowler -p your-custom-profile`. Additionally you can use `-A 123456789012` and `-R RemoteRoleToAssume` and Prowler will get those temporary credentials using `aws sts assume-role`, set them up as environment variables and run against that given account. To create a role to assume in multiple accounts easier eather as CFN Stack or StackSet, look at [this CloudFormation template](iam/create_role_to_assume_cfn.yaml) and adapt it.
|
||||
|
||||
```sh
|
||||
./prowler -A 123456789012 -R ProwlerRole
|
||||
```console
|
||||
prowler <provider>
|
||||
```
|
||||
|
||||
```sh
|
||||
./prowler -A 123456789012 -R ProwlerRole -I 123456
|
||||

|
||||
|
||||
> Running the `prowler` command without options will use your environment variable credentials.
|
||||
|
||||
By default, prowler will generate a CSV and a JSON report, however you could generate an HTML or an JSON-ASFF report with `-M` or `--output-modes`:
|
||||
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html
|
||||
```
|
||||
|
||||
> *NOTE 1 about Session Duration*: By default it gets credentials valid for 1 hour (3600 seconds). Depending on the mount of checks you run and the size of your infrastructure, Prowler may require more than 1 hour to finish. Use option `-T <seconds>` to allow up to 12h (43200 seconds). To allow more than 1h you need to modify *"Maximum CLI/API session duration"* for that particular role, read more [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use.html#id_roles_use_view-role-max-session).
|
||||
You can use `-l`/`--list-checks` or `--list-services` to list all available checks or services within the provider.
|
||||
|
||||
> *NOTE 2 about Session Duration*: Bear in mind that if you are using roles assumed by role chaining there is a hard limit of 1 hour so consider not using role chaining if possible, read more about that, in foot note 1 below the table [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use.html).
|
||||
|
||||
For example, if you want to get only the fails in CSV format from all checks regarding RDS without banner from the AWS Account 123456789012 assuming the role RemoteRoleToAssume and set a fixed session duration of 1h:
|
||||
|
||||
```sh
|
||||
./prowler -A 123456789012 -R RemoteRoleToAssume -T 3600 -b -M cvs -q -g rds
|
||||
```
|
||||
or with a given External ID:
|
||||
```sh
|
||||
./prowler -A 123456789012 -R RemoteRoleToAssume -T 3600 -I 123456 -b -M cvs -q -g rds
|
||||
```console
|
||||
prowler <provider> --list-checks
|
||||
prowler <provider> --list-services
|
||||
```
|
||||
|
||||
### Assume Role and across all accounts in AWS Organizations or just a list of accounts:
|
||||
For executing specific checks or services you can use options `-c`/`checks` or `-s`/`services`:
|
||||
|
||||
If you want to run Prowler or just a check or a group across all accounts of AWS Organizations you can do this:
|
||||
|
||||
First get a list of accounts that are not suspended:
|
||||
```
|
||||
ACCOUNTS_IN_ORGS=$(aws organizations list-accounts --query Accounts[?Status==`ACTIVE`].Id --output text)
|
||||
```
|
||||
Then run Prowler to assume a role (same in all members) per each account, in this example it is just running one particular check:
|
||||
```
|
||||
for accountId in $ACCOUNTS_IN_ORGS; do ./prowler -A $accountId -R RemoteRoleToAssume -c extra79; done
|
||||
```
|
||||
Using the same for loop it can be scanned a list of accounts with a variable like `ACCOUNTS_LIST='11111111111 2222222222 333333333'`
|
||||
|
||||
### Get AWS Account details from your AWS Organization:
|
||||
|
||||
From Prowler v2.8, you can get additional information of the scanned account in CSV and JSON outputs. When scanning a single account you get the Account ID as part of the output. Now, if you have AWS Organizations and are scanning multiple accounts using the assume role functionality, Prowler can get your account details like Account Name, Email, ARN, Organization ID and Tags and you will have them next to every finding in the CSV and JSON outputs.
|
||||
In order to do that you can use the new option `-O <management account id>`, requires `-R <role to assume>` and also needs permissions `organizations:ListAccounts*` and `organizations:ListTagsForResource`. See the following sample command:
|
||||
```
|
||||
./prowler -R ProwlerScanRole -A 111111111111 -O 222222222222 -M json,csv
|
||||
```
|
||||
In that command Prowler will scan the account `111111111111` assuming the role `ProwlerScanRole` and getting the account details from the AWS Organizatiosn management account `222222222222` assuming the same role `ProwlerScanRole` for that and creating two reports with those details in JSON and CSV.
|
||||
|
||||
In the JSON output below (redacted) you can see tags coded in base64 to prevent breaking CSV or JSON due to its format:
|
||||
|
||||
```json
|
||||
"Account Email": "my-prod-account@domain.com",
|
||||
"Account Name": "my-prod-account",
|
||||
"Account ARN": "arn:aws:organizations::222222222222:account/o-abcde1234/111111111111",
|
||||
"Account Organization": "o-abcde1234",
|
||||
"Account tags": "\"eyJUYWdzIjpasf0=\""
|
||||
```
|
||||
The additional fields in CSV header output are as follow:
|
||||
|
||||
```csv
|
||||
ACCOUNT_DETAILS_EMAIL,ACCOUNT_DETAILS_NAME,ACCOUNT_DETAILS_ARN,ACCOUNT_DETAILS_ORG,ACCOUNT_DETAILS_TAGS
|
||||
```console
|
||||
prowler aws --checks s3_bucket_public_access
|
||||
prowler aws --services s3 ec2
|
||||
```
|
||||
|
||||
### GovCloud
|
||||
Also, checks and services can be excluded with options `-e`/`--excluded-checks` or `--excluded-services`:
|
||||
|
||||
Prowler runs in GovCloud regions as well. To make sure it points to the right API endpoint use `-r` to either `us-gov-west-1` or `us-gov-east-1`. If not filter region is used it will look for resources in both GovCloud regions by default:
|
||||
```sh
|
||||
./prowler -r us-gov-west-1
|
||||
```
|
||||
> For Security Hub integration see below in Security Hub section.
|
||||
|
||||
### Custom folder for custom checks
|
||||
|
||||
Flag `-x /my/own/checks` will include any check in that particular directory (files must start by check). To see how to write checks see [Add Custom Checks](#add-custom-checks) section.
|
||||
|
||||
S3 URIs are also supported as custom folders for custom checks, e.g. `s3://bucket/prefix/checks`. Prowler will download the folder locally and run the checks as they are called with default execution,`-c` or `-g`.
|
||||
>Make sure that the used credentials have s3:GetObject permissions in the S3 path where the custom checks are located.
|
||||
|
||||
### Show or log only FAILs
|
||||
|
||||
In order to remove noise and get only FAIL findings there is a `-q` flag that makes Prowler to show and log only FAILs.
|
||||
It can be combined with any other option.
|
||||
Will show WARNINGS when a resource is excluded, just to take into consideration.
|
||||
|
||||
```sh
|
||||
# -q option combined with -M csv -b
|
||||
./prowler -q -M csv -b
|
||||
```console
|
||||
prowler aws --excluded-checks s3_bucket_public_access
|
||||
prowler aws --excluded-services s3 ec2
|
||||
```
|
||||
|
||||
### Set the entropy limit for detect-secrets
|
||||
You can always use `-h`/`--help` to access to the usage information and all the possible options:
|
||||
|
||||
Sets the entropy limit for high entropy base64 strings from environment variable `BASE64_LIMIT`. Value must be between 0.0 and 8.0, defaults is 4.5.
|
||||
Sets the entropy limit for high entropy hex strings from environment variable `HEX_LIMIT`. Value must be between 0.0 and 8.0, defaults is 3.0.
|
||||
|
||||
```sh
|
||||
export BASE64_LIMIT=4.5
|
||||
export HEX_LIMIT=3.0
|
||||
```
|
||||
### Run Prowler using AWS CloudShell
|
||||
|
||||
An easy way to run Prowler to scan your account is using AWS CloudShell. Read more and learn how to do it [here](util/cloudshell/README.md).
|
||||
|
||||
## Security Hub integration
|
||||
|
||||
Since October 30th 2020 (version v2.3RC5), Prowler supports natively and as **official integration** sending findings to [AWS Security Hub](https://aws.amazon.com/security-hub). This integration allows Prowler to import its findings to AWS Security Hub. With Security Hub, you now have a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, and AWS Firewall Manager, as well as from AWS Partner solutions and from Prowler for free.
|
||||
|
||||
Before sending findings to Prowler, you need to perform next steps:
|
||||
1. Since Security Hub is a region based service, enable it in the region or regions you require. Use the AWS Management Console or using the AWS CLI with this command if you have enough permissions:
|
||||
- `aws securityhub enable-security-hub --region <region>`.
|
||||
2. Enable Prowler as partner integration integration. Use the AWS Management Console or using the AWS CLI with this command if you have enough permissions:
|
||||
- `aws securityhub enable-import-findings-for-product --region <region> --product-arn arn:aws:securityhub:<region>::product/prowler/prowler` (change region also inside the ARN).
|
||||
- Using the AWS Management Console:
|
||||

|
||||
3. As mentioned in section "Custom IAM Policy", to allow Prowler to import its findings to AWS Security Hub you need to add the policy below to the role or user running Prowler:
|
||||
- [iam/prowler-security-hub.json](iam/prowler-security-hub.json)
|
||||
|
||||
Once it is enabled, it is as simple as running the command below (for all regions):
|
||||
|
||||
```sh
|
||||
./prowler -M json-asff -S
|
||||
```
|
||||
or for only one filtered region like eu-west-1:
|
||||
```sh
|
||||
./prowler -M json-asff -q -S -f eu-west-1
|
||||
```
|
||||
> Note 1: It is recommended to send only fails to Security Hub and that is possible adding `-q` to the command.
|
||||
|
||||
> Note 2: Since Prowler perform checks to all regions by defaults you may need to filter by region when runing Security Hub integration, as shown in the example above. Remember to enable Security Hub in the region or regions you need by calling `aws securityhub enable-security-hub --region <region>` and run Prowler with the option `-f <region>` (if no region is used it will try to push findings in all regions hubs).
|
||||
|
||||
> Note 3: to have updated findings in Security Hub you have to run Prowler periodically. Once a day or every certain amount of hours.
|
||||
|
||||
Once you run findings for first time you will be able to see Prowler findings in Findings section:
|
||||
|
||||

|
||||
|
||||
### Security Hub in GovCloud regions
|
||||
|
||||
To use Prowler and Security Hub integration in GovCloud there is an additional requirement, usage of `-r` is needed to point the API queries to the right API endpoint. Here is a sample command that sends only failed findings to Security Hub in region `us-gov-west-1`:
|
||||
```
|
||||
./prowler -r us-gov-west-1 -f us-gov-west-1 -S -M csv,json-asff -q
|
||||
```console
|
||||
prowler -h
|
||||
```
|
||||
|
||||
### Security Hub in China regions
|
||||
## AWS
|
||||
|
||||
To use Prowler and Security Hub integration in China regions there is an additional requirement, usage of `-r` is needed to point the API queries to the right API endpoint. Here is a sample command that sends only failed findings to Security Hub in region `cn-north-1`:
|
||||
```
|
||||
./prowler -r cn-north-1 -f cn-north-1 -q -S -M csv,json-asff
|
||||
Use a custom AWS profile with `-p`/`--profile` and/or AWS regions which you want to audit with `-f`/`--filter-region`:
|
||||
|
||||
```console
|
||||
prowler aws --profile custom-profile -f us-east-1 eu-south-2
|
||||
```
|
||||
> By default, `prowler` will scan all AWS regions.
|
||||
|
||||
## CodeBuild deployment
|
||||
# 🎉 New Features
|
||||
|
||||
Either to run Prowler once or based on a schedule this template makes it pretty straight forward. This template will create a CodeBuild environment and run Prowler directly leaving all reports in a bucket and creating a report also inside CodeBuild basedon the JUnit output from Prowler. Scheduling can be cron based like `cron(0 22 * * ? *)` or rate based like `rate(5 hours)` since CloudWatch Event rules (or Eventbridge) is used here.
|
||||
- Multi-cloud support!
|
||||
|
||||
The Cloud Formation template that helps you doing that is [here](https://github.com/prowler-cloud/prowler/blob/master/util/codebuild/codebuild-prowler-audit-account-cfn.yaml).
|
||||
# 📖 Documentation
|
||||
|
||||
> This is a simple solution to monitor one account. For multiples accounts see [Multi Account and Continuous Monitoring](util/org-multi-account/README.md).
|
||||
The full documentation can be found here:
|
||||
|
||||
## Allowlist or remove a fail from resources
|
||||
|
||||
Sometimes you may find resources that are intentionally configured in a certain way that may be a bad practice but it is all right with it, for example an S3 bucket open to the internet hosting a web site, or a security group with an open port needed in your use case. Now you can use `-w allowlist_sample.txt` and add your resources as `checkID:resourcename` as in this command:
|
||||
|
||||
```
|
||||
./prowler -w allowlist_sample.txt
|
||||
```
|
||||
|
||||
S3 URIs are also supported as allowlist file, e.g. `s3://bucket/prefix/allowlist_sample.txt`
|
||||
>Make sure that the used credentials have s3:GetObject permissions in the S3 path where the allowlist file is located.
|
||||
|
||||
DynamoDB table ARNs are also supported as allowlist file, e.g. `arn:aws:dynamodb:us-east-1:111111222222:table/allowlist`
|
||||
>Make sure that the table has `account_id` as partition key and `rule` as sort key, and that the used credentials have `dynamodb:PartiQLSelect` permissions in the table.
|
||||
><p align="left"><img src="https://user-images.githubusercontent.com/38561120/165769502-296f9075-7cc8-445e-8158-4b21804bfe7e.png" alt="image" width="397" height="252" /></p>
|
||||
|
||||
>The field `account_id` can contains either an account ID or an `*` (which applies to all the accounts that use this table as a whitelist). As in the traditional allowlist file, the `rule` field must contain `checkID:resourcename` pattern.
|
||||
><p><img src="https://user-images.githubusercontent.com/38561120/165770610-ed5c2764-7538-44c2-9195-bcfdecc4ef9b.png" alt="image" width="394" /></p>
|
||||
|
||||
|
||||
|
||||
Allowlist option works along with other options and adds a `WARNING` instead of `INFO`, `PASS` or `FAIL` to any output format except for `json-asff`.
|
||||
|
||||
## How to fix every FAIL
|
||||
|
||||
Check your report and fix the issues following all specific guidelines per check in <https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf>
|
||||
|
||||
## Troubleshooting
|
||||
|
||||
### STS expired token
|
||||
|
||||
If you are using an STS token for AWS-CLI and your session is expired you probably get this error:
|
||||
|
||||
```sh
|
||||
A client error (ExpiredToken) occurred when calling the GenerateCredentialReport operation: The security token included in the request is expired
|
||||
```
|
||||
|
||||
To fix it, please renew your token by authenticating again to the AWS API, see next section below if you use MFA.
|
||||
|
||||
### Run Prowler with MFA protected credentials
|
||||
|
||||
To run Prowler using a profile that requires MFA you just need to get the session token before hand. Just make sure you use this command:
|
||||
|
||||
```sh
|
||||
aws --profile <YOUR_AWS_PROFILE> sts get-session-token --duration 129600 --serial-number <ARN_OF_MFA> --token-code <MFA_TOKEN_CODE> --output text
|
||||
```
|
||||
|
||||
Once you get your token you can export it as environment variable:
|
||||
|
||||
```sh
|
||||
export AWS_PROFILE=YOUR_AWS_PROFILE
|
||||
export AWS_SESSION_TOKEN=YOUR_NEW_TOKEN
|
||||
AWS_SECRET_ACCESS_KEY=YOUR_SECRET
|
||||
export AWS_ACCESS_KEY_ID=YOUR_KEY
|
||||
```
|
||||
|
||||
or set manually up your `~/.aws/credentials` file properly.
|
||||
|
||||
There are some helpfull tools to save time in this process like [aws-mfa-script](https://github.com/asagage/aws-mfa-script) or [aws-cli-mfa](https://github.com/sweharris/aws-cli-mfa).
|
||||
|
||||
### AWS Managed IAM Policies
|
||||
|
||||
[ViewOnlyAccess](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_job-functions.html#jf_view-only-user)
|
||||
- Use case: This user can view a list of AWS resources and basic metadata in the account across all services. The user cannot read resource content or metadata that goes beyond the quota and list information for resources.
|
||||
- Policy description: This policy grants List*, Describe*, Get*, View*, and Lookup* access to resources for most AWS services. To see what actions this policy includes for each service, see [ViewOnlyAccess Permissions](https://console.aws.amazon.com/iam/home#policies/arn:aws:iam::aws:policy/job-function/ViewOnlyAccess)
|
||||
|
||||
[SecurityAudit](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_job-functions.html#jf_security-auditor)
|
||||
- Use case: This user monitors accounts for compliance with security requirements. This user can access logs and events to investigate potential security breaches or potential malicious activity.
|
||||
- Policy description: This policy grants permissions to view configuration data for many AWS services and to review their logs. To see what actions this policy includes for each service, see [SecurityAudit Permissions](https://console.aws.amazon.com/iam/home#policies/arn:aws:iam::aws:policy/SecurityAudit)
|
||||
|
||||
### Custom IAM Policy
|
||||
|
||||
[Prowler-Additions-Policy](iam/prowler-additions-policy.json)
|
||||
|
||||
Some new and specific checks require Prowler to inherit more permissions than SecurityAudit and ViewOnlyAccess to work properly. In addition to the AWS managed policies, "SecurityAudit" and "ViewOnlyAccess", the user/role you use for checks may need to be granted a custom policy with a few more read-only permissions (to support additional services mostly). Here is an example policy with the additional rights, "Prowler-Additions-Policy" (see below bootstrap script for set it up):
|
||||
|
||||
- [iam/prowler-additions-policy.json](iam/prowler-additions-policy.json)
|
||||
|
||||
[Prowler-Security-Hub Policy](iam/prowler-security-hub.json)
|
||||
|
||||
Allows Prowler to import its findings to [AWS Security Hub](https://aws.amazon.com/security-hub). More information in [Security Hub integration](#security-hub-integration):
|
||||
|
||||
- [iam/prowler-security-hub.json](iam/prowler-security-hub.json)
|
||||
|
||||
### Bootstrap Script
|
||||
|
||||
Quick bash script to set up a "prowler" IAM user with "SecurityAudit" and "ViewOnlyAccess" group with the required permissions (including "Prowler-Additions-Policy"). To run the script below, you need user with administrative permissions; set the `AWS_DEFAULT_PROFILE` to use that account:
|
||||
|
||||
```sh
|
||||
export AWS_DEFAULT_PROFILE=default
|
||||
export ACCOUNT_ID=$(aws sts get-caller-identity --query 'Account' | tr -d '"')
|
||||
aws iam create-group --group-name Prowler
|
||||
aws iam create-policy --policy-name Prowler-Additions-Policy --policy-document file://$(pwd)/iam/prowler-additions-policy.json
|
||||
aws iam attach-group-policy --group-name Prowler --policy-arn arn:aws:iam::aws:policy/SecurityAudit
|
||||
aws iam attach-group-policy --group-name Prowler --policy-arn arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
aws iam attach-group-policy --group-name Prowler --policy-arn arn:aws:iam::${ACCOUNT_ID}:policy/Prowler-Additions-Policy
|
||||
aws iam create-user --user-name prowler
|
||||
aws iam add-user-to-group --user-name prowler --group-name Prowler
|
||||
aws iam create-access-key --user-name prowler
|
||||
unset ACCOUNT_ID AWS_DEFAULT_PROFILE
|
||||
```
|
||||
|
||||
The `aws iam create-access-key` command will output the secret access key and the key id; keep these somewhere safe, and add them to `~/.aws/credentials` with an appropriate profile name to use them with Prowler. This is the only time they secret key will be shown. If you lose it, you will need to generate a replacement.
|
||||
|
||||
> [This CloudFormation template](iam/create_role_to_assume_cfn.yaml) may also help you on that task.
|
||||
|
||||
## Extras
|
||||
|
||||
We are adding additional checks to improve the information gather from each account, these checks are out of the scope of the CIS benchmark for AWS, but we consider them very helpful to get to know each AWS account set up and find issues on it.
|
||||
|
||||
Some of these checks look for publicly facing resources may not actually be fully public due to other layered controls like S3 Bucket Policies, Security Groups or Network ACLs.
|
||||
|
||||
To list all existing checks in the extras group run the command below:
|
||||
|
||||
```sh
|
||||
./prowler -l -g extras
|
||||
```
|
||||
|
||||
>There are some checks not included in that list, they are experimental or checks that takes long to run like `extra759` and `extra760` (search for secrets in Lambda function variables and code).
|
||||
|
||||
To check all extras in one command:
|
||||
|
||||
```sh
|
||||
./prowler -g extras
|
||||
```
|
||||
|
||||
or to run just one of the checks:
|
||||
|
||||
```sh
|
||||
./prowler -c extraNUMBER
|
||||
```
|
||||
|
||||
or to run multiple extras in one go:
|
||||
|
||||
```sh
|
||||
./prowler -c extraNumber,extraNumber
|
||||
```
|
||||
|
||||
|
||||
## Forensics Ready Checks
|
||||
|
||||
With this group of checks, Prowler looks if each service with logging or audit capabilities has them enabled to ensure all needed evidences are recorded and collected for an eventual digital forensic investigation in case of incident. List of checks part of this group (you can also see all groups with `./prowler -L`). The list of checks can be seen in the group file at:
|
||||
|
||||
[groups/group8_forensics](groups/group8_forensics)
|
||||
|
||||
The `forensics-ready` group of checks uses existing and extra checks. To get a forensics readiness report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g forensics-ready
|
||||
```
|
||||
|
||||
## GDPR Checks
|
||||
|
||||
With this group of checks, Prowler shows result of checks related to GDPR, more information [here](https://github.com/prowler-cloud/prowler/issues/189). The list of checks can be seen in the group file at:
|
||||
|
||||
[groups/group9_gdpr](groups/group9_gdpr)
|
||||
|
||||
The `gdpr` group of checks uses existing and extra checks. To get a GDPR report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g gdpr
|
||||
```
|
||||
|
||||
## AWS FTR Checks
|
||||
|
||||
With this group of checks, Prowler shows result of checks related to the AWS Foundational Technical Review, more information [here](https://apn-checklists.s3.amazonaws.com/foundational/partner-hosted/partner-hosted/CVLHEC5X7.html). The list of checks can be seen in the group file at:
|
||||
|
||||
[groups/group25_ftr](groups/group25_FTR)
|
||||
|
||||
The `ftr` group of checks uses existing and extra checks. To get a AWS FTR report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g ftr
|
||||
```
|
||||
|
||||
## HIPAA Checks
|
||||
|
||||
With this group of checks, Prowler shows results of controls related to the "Security Rule" of the Health Insurance Portability and Accountability Act aka [HIPAA](https://www.hhs.gov/hipaa/for-professionals/security/index.html) as defined in [45 CFR Subpart C - Security Standards for the Protection of Electronic Protected Health Information](https://www.law.cornell.edu/cfr/text/45/part-164/subpart-C) within [PART 160 - GENERAL ADMINISTRATIVE REQUIREMENTS](https://www.law.cornell.edu/cfr/text/45/part-160) and [Subpart A](https://www.law.cornell.edu/cfr/text/45/part-164/subpart-A) and [Subpart C](https://www.law.cornell.edu/cfr/text/45/part-164/subpart-C) of PART 164 - SECURITY AND PRIVACY
|
||||
|
||||
More information on the original PR is [here](https://github.com/prowler-cloud/prowler/issues/227).
|
||||
|
||||
### Note on Business Associate Addendum's (BAA)
|
||||
|
||||
Under the HIPAA regulations, cloud service providers (CSPs) such as AWS are considered business associates. The Business Associate Addendum (BAA) is an AWS contract that is required under HIPAA rules to ensure that AWS appropriately safeguards protected health information (PHI). The BAA also serves to clarify and limit, as appropriate, the permissible uses and disclosures of PHI by AWS, based on the relationship between AWS and our customers, and the activities or services being performed by AWS. Customers may use any AWS service in an account designated as a HIPAA account, but they should only process, store, and transmit protected health information (PHI) in the HIPAA-eligible services defined in the Business Associate Addendum (BAA). For the latest list of HIPAA-eligible AWS services, see [HIPAA Eligible Services Reference](https://aws.amazon.com/compliance/hipaa-eligible-services-reference/).
|
||||
|
||||
More information on AWS & HIPAA can be found [here](https://aws.amazon.com/compliance/hipaa-compliance/)
|
||||
|
||||
The list of checks showed by this group is as follows, they will be mostly relevant for Subsections [164.306 Security standards: General rules](https://www.law.cornell.edu/cfr/text/45/164.306) and [164.312 Technical safeguards](https://www.law.cornell.edu/cfr/text/45/164.312). Prowler is only able to make checks in the spirit of the technical requirements outlined in these Subsections, and cannot cover all procedural controls required. They be found in the group file at:
|
||||
|
||||
[groups/group10_hipaa](groups/group10_hipaa)
|
||||
|
||||
The `hipaa` group of checks uses existing and extra checks. To get a HIPAA report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g hipaa
|
||||
```
|
||||
|
||||
## Trust Boundaries Checks
|
||||
|
||||
### Definition and Terms
|
||||
|
||||
The term "trust boundary" is originating from the threat modelling process and the most popular contributor Adam Shostack and author of "Threat Modeling: Designing for Security" defines it as following ([reference](https://adam.shostack.org/uncover.html)):
|
||||
|
||||
> Trust boundaries are perhaps the most subjective of all: these represent the border between trusted and untrusted elements. Trust is complex. You might trust your mechanic with your car, your dentist with your teeth, and your banker with your money, but you probably don't trust your dentist to change your spark plugs.
|
||||
|
||||
AWS is made to be flexible for service links within and between different AWS accounts, we all know that.
|
||||
|
||||
This group of checks helps to analyse a particular AWS account (subject) on existing links to other AWS accounts across various AWS services, in order to identify untrusted links.
|
||||
|
||||
### Run
|
||||
To give it a quick shot just call:
|
||||
|
||||
```sh
|
||||
./prowler -g trustboundaries
|
||||
```
|
||||
|
||||
### Scenarios
|
||||
|
||||
Currently, this check group supports two different scenarios:
|
||||
|
||||
1. Single account environment: no action required, the configuration is happening automatically for you.
|
||||
2. Multi account environment: in case you environment has multiple trusted and known AWS accounts you maybe want to append them manually to [groups/group16_trustboundaries](groups/group16_trustboundaries) as a space separated list into `GROUP_TRUSTBOUNDARIES_TRUSTED_ACCOUNT_IDS` variable, then just run prowler.
|
||||
|
||||
### Coverage
|
||||
|
||||
Current coverage of Amazon Web Service (AWS) taken from [here](https://docs.aws.amazon.com/whitepapers/latest/aws-overview/introduction.html):
|
||||
| Topic | Service | Trust Boundary |
|
||||
|---------------------------------|------------|---------------------------------------------------------------------------|
|
||||
| Networking and Content Delivery | Amazon VPC | VPC endpoints connections ([extra786](checks/check_extra786)) |
|
||||
| | | VPC endpoints allowlisted principals ([extra787](checks/check_extra787)) |
|
||||
|
||||
All ideas or recommendations to extend this group are very welcome [here](https://github.com/prowler-cloud/prowler/issues/new/choose).
|
||||
|
||||
### Detailed Explanation of the Concept
|
||||
|
||||
The diagrams depict two common scenarios, single account and multi account environments.
|
||||
Every circle represents one AWS account.
|
||||
The dashed line represents the trust boundary, that separates trust and untrusted AWS accounts.
|
||||
The arrow simply describes the direction of the trust, however the data can potentially flow in both directions.
|
||||
|
||||
Single Account environment assumes that only the AWS account subject to this analysis is trusted. However, there is a chance that two VPCs are existing within that one AWS account which are still trusted as a self reference.
|
||||

|
||||
|
||||
Multi Account environments assumes a minimum of two trusted or known accounts. For this particular example all trusted and known accounts will be tested. Therefore `GROUP_TRUSTBOUNDARIES_TRUSTED_ACCOUNT_IDS` variable in [groups/group16_trustboundaries](groups/group16_trustboundaries) should include all trusted accounts Account #A, Account #B, Account #C, and Account #D in order to finally raise Account #E and Account #F for being untrusted or unknown.
|
||||

|
||||
|
||||
## Custom Checks
|
||||
Using `./prowler -c extra9999 -a` you can build your own on-the-fly custom check by specifying the AWS CLI command to execute.
|
||||
> Omit the "aws" command and only use its parameters within quotes and do not nest quotes in the aws parameter, --output text is already included in the check.
|
||||
>
|
||||
Here is an example of a check to find SGs with inbound port 80:
|
||||
|
||||
```sh
|
||||
./prowler -c extra9999 -a 'ec2 describe-security-groups --filters Name=ip-permission.to-port,Values=80 --query SecurityGroups[*].GroupId[]]'
|
||||
```
|
||||
|
||||
In order to add any new check feel free to create a new extra check in the extras group or other group. To do so, you will need to follow these steps:
|
||||
|
||||
1. Follow structure in file `checks/check_sample`
|
||||
2. Name your check with a number part of an existing group or a new one
|
||||
3. Save changes and run it as `./prowler -c extraNN`
|
||||
4. Send me a pull request! :)
|
||||
|
||||
## Add Custom Groups
|
||||
|
||||
1. Follow structure in file `groups/groupN_sample`
|
||||
1. Name your group with a non existing number
|
||||
1. Save changes and run it as `./prowler -g extraNN`
|
||||
1. Send me a pull request! :)
|
||||
|
||||
- You can also create a group with only the checks that you want to perform in your company, for instance a group named `group9_mycompany` with only the list of checks that you care or your particular compliance applies.
|
||||
|
||||
## Third Party Integrations
|
||||
|
||||
### Telegram
|
||||
|
||||
Javier Pecete has done an awesome job integrating Prowler with Telegram, you have more details here <https://github.com/i4specete/ServerTelegramBot>
|
||||
|
||||
### Cloud Security Suite
|
||||
|
||||
The guys of SecurityFTW have added Prowler in their Cloud Security Suite along with other cool security tools <https://github.com/SecurityFTW/cs-suite>
|
||||
|
||||
## License
|
||||
[https://prowler-cloud.github.io/prowler/](https://prowler-cloud.github.io/prowler/)
|
||||
# 📃 License
|
||||
|
||||
Prowler is licensed as Apache License 2.0 as specified in each file. You may obtain a copy of the License at
|
||||
<http://www.apache.org/licenses/LICENSE-2.0>
|
||||
|
||||
**I'm not related anyhow with CIS organization, I just write and maintain Prowler to help companies over the world to make their cloud infrastructure more secure.**
|
||||
|
||||
If you want to contact me visit <https://blyx.com/contact> or follow me on Twitter <https://twitter.com/prowler-cloud> my DMs are open.
|
||||
|
||||
|
||||
## Prowler 3.0
|
||||
### Project Structure
|
||||
```
|
||||
.
|
||||
├── README.md
|
||||
├── check
|
||||
│ └── check.py
|
||||
├── poc.py
|
||||
└── providers
|
||||
└── aws
|
||||
├── aws_provider.py
|
||||
└── services
|
||||
└── iam
|
||||
├── iam_disable_30_days_credentials
|
||||
│ ├── iam_disable_30_days_credentials.metadata.json
|
||||
│ └── iam_disable_30_days_credentials.py
|
||||
└── iam_service.py
|
||||
```
|
||||
|
||||
26
docs/about.md
Normal file
@@ -0,0 +1,26 @@
|
||||
---
|
||||
hide:
|
||||
- toc
|
||||
---
|
||||
# About
|
||||
|
||||
## Author
|
||||
Prowler was created by **Toni de la Fuente** in 2016.
|
||||
|
||||
| <br>[](https://twitter.com/toniblyx)|
|
||||
|:--:|
|
||||
| <b>Toni de la Fuente </b>|
|
||||
|
||||
## Maintainers
|
||||
Prowler is maintained by the Engineers of the **Prowler Team** :
|
||||
|
||||
| [](https://twitter.com/NachoRivCor) | [](https://twitter.com/sergargar1) |[](https://twitter.com/jfagoagas) |
|
||||
|:--:|:--:|:--:
|
||||
| <b>Nacho Rivera</b>| <b>Sergio Garcia</b>| <b>Pepe Fagoaga</b>|
|
||||
|
||||
|
||||
|
||||
## License
|
||||
|
||||
Prowler is licensed as **Apache License 2.0** as specified in each file. You may obtain a copy of the License at
|
||||
<http://www.apache.org/licenses/LICENSE-2.0>
|
||||
9
docs/contact.md
Normal file
@@ -0,0 +1,9 @@
|
||||
# Contact Us
|
||||
|
||||
For technical support or any type of inquiries, you are very welcome to:
|
||||
|
||||
- Reach out to community members on the [**Prowler Slack channel**](https://join.slack.com/t/prowler-workspace/shared_invite/zt-1hix76xsl-2uq222JIXrC7Q8It~9ZNog)
|
||||
|
||||
- Open an Issue or a Pull Request in our [**GitHub repository**](https://github.com/prowler-cloud/prowler).
|
||||
|
||||
We will appreciate all types of feedback and contribution, Prowler would not be the same without our vibrant community! 😃
|
||||
BIN
docs/favicon.ico
Normal file
|
After Width: | Height: | Size: 1.2 KiB |
81
docs/getting-started/requirements.md
Normal file
@@ -0,0 +1,81 @@
|
||||
# Requirements
|
||||
|
||||
Prowler has been written in Python using the [AWS SDK (Boto3)](https://boto3.amazonaws.com/v1/documentation/api/latest/index.html#) and [Azure SDK](https://learn.microsoft.com/en-us/python/api/overview/azure/?view=azure-python).
|
||||
## AWS
|
||||
|
||||
Since Prowler uses AWS Credentials under the hood, you can follow any authentication method as described [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-precedence).
|
||||
|
||||
### AWS Authentication
|
||||
|
||||
Make sure you have properly configured your AWS-CLI with a valid Access Key and Region or declare AWS variables properly (or instance profile/role):
|
||||
|
||||
```console
|
||||
aws configure
|
||||
```
|
||||
|
||||
or
|
||||
|
||||
```console
|
||||
export AWS_ACCESS_KEY_ID="ASXXXXXXX"
|
||||
export AWS_SECRET_ACCESS_KEY="XXXXXXXXX"
|
||||
export AWS_SESSION_TOKEN="XXXXXXXXX"
|
||||
```
|
||||
|
||||
Those credentials must be associated to a user or role with proper permissions to do all checks. To make sure, add the following AWS managed policies to the user or role being used:
|
||||
|
||||
- arn:aws:iam::aws:policy/SecurityAudit
|
||||
- arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
|
||||
> Moreover, some read-only additional permissions are needed for several checks, make sure you attach also the custom policy [prowler-additions-policy.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-additions-policy.json) to the role you are using.
|
||||
|
||||
> If you want Prowler to send findings to [AWS Security Hub](https://aws.amazon.com/security-hub), make sure you also attach the custom policy [prowler-security-hub.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-security-hub.json).
|
||||
|
||||
## Azure
|
||||
|
||||
Prowler for azure supports the following authentication types:
|
||||
|
||||
- Service principal authentication by environment variables (Enterprise Application)
|
||||
- Current az cli credentials stored
|
||||
- Interactive browser authentication
|
||||
- Managed identity authentication
|
||||
|
||||
### Service Principal authentication
|
||||
|
||||
To allow Prowler assume the service principal identity to start the scan it is needed to configure the following environment variables:
|
||||
|
||||
```console
|
||||
export AZURE_CLIENT_ID="XXXXXXXXX"
|
||||
export AZURE_TENANT_ID="XXXXXXXXX"
|
||||
export AZURE_CLIENT_SECRET="XXXXXXX"
|
||||
```
|
||||
|
||||
If you try to execute Prowler with the `--sp-env-auth` flag and those variables are empty or not exported, the execution is going to fail.
|
||||
### AZ CLI / Browser / Managed Identity authentication
|
||||
|
||||
The other three cases does not need additional configuration, `--az-cli-auth` and `--managed-identity-auth` are automated options, `--browser-auth` needs the user to authenticate using the default browser to start the scan.
|
||||
|
||||
### Permissions
|
||||
|
||||
To use each one you need to pass the proper flag to the execution. Prowler fro Azure handles two types of permission scopes, which are:
|
||||
|
||||
- **Azure Active Directory permissions**: Used to retrieve metadata from the identity assumed by Prowler and future AAD checks (not mandatory to have access to execute the tool)
|
||||
- **Subscription scope permissions**: Required to launch the checks against your resources, mandatory to launch the tool.
|
||||
|
||||
|
||||
#### Azure Active Directory scope
|
||||
|
||||
Azure Active Directory (AAD) permissions required by the tool are the following:
|
||||
|
||||
- `Directory.Read.All`
|
||||
- `Policy.Read.All`
|
||||
|
||||
The best way to assign it is through the azure web console:
|
||||
|
||||

|
||||
|
||||
#### Subscriptions scope
|
||||
|
||||
Regarding the subscription scope, Prowler by default scans all the subscriptions that is able to list, so it is required to add the following RBAC builtin roles per subscription to the entity that is going to be assumed by the tool:
|
||||
|
||||
- `Security Reader`
|
||||
- `Reader`
|
||||
BIN
docs/img/AAD-permissions.png
Normal file
|
After Width: | Height: | Size: 358 KiB |
1
docs/img/ProwlerPro-icon.svg
Normal file
@@ -0,0 +1 @@
|
||||
<svg id="Layer_1" data-name="Layer 1" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" viewBox="0 0 240.29 285.79"><defs><style>.cls-1{fill:url(#linear-gradient);}.cls-2{fill:#71be44;}</style><linearGradient id="linear-gradient" x1="157.45" y1="97.85" x2="211.7" y2="97.85" gradientUnits="userSpaceOnUse"><stop offset="0" stop-color="#5a9b37"/><stop offset="1" stop-color="#71be44"/></linearGradient></defs><circle class="cls-1" cx="148.2" cy="97.85" r="67.45"/><path class="cls-2" d="M66.28,30.4H148.2a0,0,0,0,1,0,0V185.35a81.93,81.93,0,0,1-81.93,81.93h0a0,0,0,0,1,0,0V30.4A0,0,0,0,1,66.28,30.4Z"/></svg>
|
||||
|
After Width: | Height: | Size: 635 B |
1
docs/img/ProwlerPro-logo.svg
Normal file
|
After Width: | Height: | Size: 8.7 KiB |
BIN
docs/img/allowlist-keys.png
Normal file
|
After Width: | Height: | Size: 10 KiB |
BIN
docs/img/allowlist-row.png
Normal file
|
After Width: | Height: | Size: 51 KiB |
BIN
docs/img/architecture.png
Normal file
|
After Width: | Height: | Size: 258 KiB |
BIN
docs/img/extended-display.png
Normal file
|
After Width: | Height: | Size: 172 KiB |
BIN
docs/img/nacho.png
Normal file
|
After Width: | Height: | Size: 113 KiB |
BIN
docs/img/pepe.png
Normal file
|
After Width: | Height: | Size: 100 KiB |
BIN
docs/img/prowler-logo.png
Normal file
|
After Width: | Height: | Size: 27 KiB |
|
Before Width: | Height: | Size: 76 KiB After Width: | Height: | Size: 76 KiB |
|
Before Width: | Height: | Size: 9.2 KiB After Width: | Height: | Size: 9.2 KiB |
|
Before Width: | Height: | Size: 8.7 KiB After Width: | Height: | Size: 8.7 KiB |
|
Before Width: | Height: | Size: 52 KiB After Width: | Height: | Size: 52 KiB |
BIN
docs/img/sergio.png
Normal file
|
After Width: | Height: | Size: 80 KiB |
BIN
docs/img/short-display.png
Normal file
|
After Width: | Height: | Size: 98 KiB |
BIN
docs/img/toni.png
Normal file
|
After Width: | Height: | Size: 87 KiB |
125
docs/index.md
Normal file
@@ -0,0 +1,125 @@
|
||||
<p href="https://github.com/prowler-cloud/prowler">
|
||||
<img align="right" src="./img/prowler-logo.png" height="100">
|
||||
</p>
|
||||
<br>
|
||||
|
||||
# Prowler Documentation
|
||||
|
||||
Welcome to [Prowler](https://github.com/prowler-cloud/prowler/) Documentation! 📄
|
||||
|
||||
- You are currently in the **Getting Started** section where you can find general information and requirements to help you start with the tool.
|
||||
- In the [Tutorials](tutorials/overview) section you will see how to take advantage of all the features in Prowler.
|
||||
- In the [Contact Us](contact) section you can find how to reach us out in case of technical issues.
|
||||
- In the [About](about) section you will find more information about the Prowler team and license.
|
||||
|
||||
## About Prowler
|
||||
|
||||
**Prowler** is an Open Source security tool to perform AWS and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
|
||||
|
||||
It contains hundreds of controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.
|
||||
|
||||
## Quick Start
|
||||
|
||||
### Installation
|
||||
|
||||
Prowler is available as a project in [PyPI](https://pypi.org/project/prowler-cloud/), thus can be installed using pip:
|
||||
|
||||
```bash
|
||||
pip install prowler-cloud
|
||||
prowler -v
|
||||
```
|
||||
|
||||
## Prowler container versions
|
||||
|
||||
The available versions of Prowler are the following:
|
||||
|
||||
- latest: in sync with master branch (bear in mind that it is not a stable version)
|
||||
- <x.y.z> (release): you can find the releases [here](https://github.com/prowler-cloud/prowler/releases), those are stable releases.
|
||||
- stable: this tag always point to the latest release.
|
||||
|
||||
The container images are available here:
|
||||
|
||||
- [DockerHub](https://hub.docker.com/r/toniblyx/prowler/tags)
|
||||
- [AWS Public ECR](https://gallery.ecr.aws/o4g1s5r6/prowler)
|
||||
|
||||
## High level architecture
|
||||
|
||||
You can run Prowler from your workstation, an EC2 instance, Fargate or any other container, Codebuild, CloudShell and Cloud9.
|
||||
|
||||

|
||||
## Basic Usage
|
||||
|
||||
To run prowler, you will need to specify the provider (e.g aws or azure):
|
||||
|
||||
```console
|
||||
prowler <provider>
|
||||
```
|
||||

|
||||
> Running the `prowler` command without options will use your environment variable credentials, see [Requirements](getting-started/requirements/) section to review the credentials settings.
|
||||
|
||||
By default, prowler will generate a CSV and a JSON report, however you could generate an HTML or an JSON-ASFF report with `-M` or `--output-modes`:
|
||||
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html
|
||||
```
|
||||
|
||||
You can use `-l`/`--list-checks` or `--list-services` to list all available checks or services within the provider.
|
||||
|
||||
```console
|
||||
prowler <provider> --list-checks
|
||||
prowler <provider> --list-services
|
||||
```
|
||||
|
||||
For executing specific checks or services you can use options `-c`/`checks` or `-s`/`services`:
|
||||
|
||||
```console
|
||||
prowler azure --checks storage_blob_public_access_level_is_disabled
|
||||
prowler aws --services s3 ec2
|
||||
```
|
||||
|
||||
Also, checks and services can be excluded with options `-e`/`--excluded-checks` or `--excluded-services`:
|
||||
|
||||
```console
|
||||
prowler aws --excluded-checks s3_bucket_public_access
|
||||
prowler azure --excluded-services defender iam
|
||||
```
|
||||
|
||||
You can always use `-h`/`--help` to access to the usage information and all the possible options:
|
||||
|
||||
```console
|
||||
prowler -h
|
||||
```
|
||||
|
||||
### AWS
|
||||
|
||||
Use a custom AWS profile with `-p`/`--profile` and/or AWS regions which you want to audit with `-f`/`--filter-region`:
|
||||
|
||||
```console
|
||||
prowler aws --profile custom-profile -f us-east-1 eu-south-2
|
||||
```
|
||||
> By default, `prowler` will scan all AWS regions.
|
||||
|
||||
### Azure
|
||||
|
||||
With Azure you need to specify which auth method is going to be used:
|
||||
|
||||
```console
|
||||
# To use service principal authentication
|
||||
prowler azure --sp-env-auth
|
||||
|
||||
# To use az cli authentication
|
||||
prowler azure --az-cli-auth
|
||||
|
||||
# To use browser authentication
|
||||
prowler azure --browser-auth
|
||||
|
||||
# To use managed identity auth
|
||||
prowler azure --managed-identity-auth
|
||||
```
|
||||
|
||||
More details in [Requirements](getting-started/requirements.md)
|
||||
|
||||
Prowler by default scans all the subscriptions that is allowed to scan, if you want to scan a single subscription or various concrete subscriptions you can use the following flag (using az cli auth as example):
|
||||
```console
|
||||
prowler azure --az-cli-auth --subscription-ids <subscription ID 1> <subscription ID 2> ... <subscription ID N>
|
||||
```
|
||||
76
docs/tutorials/allowlist.md
Normal file
@@ -0,0 +1,76 @@
|
||||
# Allowlisting
|
||||
Sometimes you may find resources that are intentionally configured in a certain way that may be a bad practice but it is all right with it, for example an AWS S3 Bucket open to the internet hosting a web site, or an AWS Security Group with an open port needed in your use case.
|
||||
|
||||
Allowlist option works along with other options and adds a `WARNING` instead of `INFO`, `PASS` or `FAIL` to any output format.
|
||||
|
||||
You can use `-w`/`--allowlist-file` with the path of your allowlist yaml file, but first, let's review the syntax.
|
||||
|
||||
## Allowlist Yaml File Syntax
|
||||
|
||||
### Account, Check and/or Region can be * to apply for all the cases
|
||||
### Resources is a list that can have either Regex or Keywords:
|
||||
########################### ALLOWLIST EXAMPLE ###########################
|
||||
Allowlist:
|
||||
Accounts:
|
||||
"123456789012":
|
||||
Checks:
|
||||
"iam_user_hardware_mfa_enabled":
|
||||
Regions:
|
||||
- "us-east-1"
|
||||
Resources:
|
||||
- "user-1" # Will ignore user-1 in check iam_user_hardware_mfa_enabled
|
||||
- "user-2" # Will ignore user-2 in check iam_user_hardware_mfa_enabled
|
||||
"*":
|
||||
Regions:
|
||||
- "*"
|
||||
Resources:
|
||||
- "test" # Will ignore every resource containing the string "test" in every account and region
|
||||
|
||||
"*":
|
||||
Checks:
|
||||
"s3_bucket_object_versioning":
|
||||
Regions:
|
||||
- "eu-west-1"
|
||||
- "us-east-1"
|
||||
Resources:
|
||||
- "ci-logs" # Will ignore bucket "ci-logs" AND ALSO bucket "ci-logs-replica" in specified check and regions
|
||||
- "logs" # Will ignore EVERY BUCKET containing the string "logs" in specified check and regions
|
||||
- "[[:alnum:]]+-logs" # Will ignore all buckets containing the terms ci-logs, qa-logs, etc. in specified check and regions
|
||||
|
||||
|
||||
## Supported Allowlist Locations
|
||||
|
||||
The allowlisting flag supports the following locations:
|
||||
|
||||
### Local file
|
||||
You will need to pass the local path where your Allowlist YAML file is located:
|
||||
```
|
||||
prowler <provider> -w allowlist.yaml
|
||||
```
|
||||
### AWS S3 URI
|
||||
You will need to pass the S3 URI where your Allowlist YAML file was uploaded to your bucket:
|
||||
```
|
||||
prowler aws -w s3://<bucket>/<prefix>/allowlist.yaml
|
||||
```
|
||||
> Make sure that the used AWS credentials have s3:GetObject permissions in the S3 path where the allowlist file is located.
|
||||
|
||||
### AWS DynamoDB Table ARN
|
||||
|
||||
You will need to pass the DynamoDB Allowlist Table ARN:
|
||||
|
||||
```
|
||||
prowler aws -w arn:aws:dynamodb:<region_name>:<account_id>:table/<table_name>
|
||||
```
|
||||
|
||||
1. The DynamoDB Table must have the following String keys:
|
||||
<img src="/img/allowlist-keys.png"/>
|
||||
|
||||
- The Allowlist Table must have the following columns:
|
||||
- Accounts (String): This field can contain either an Account ID or an `*` (which applies to all the accounts that use this table as an allowlist).
|
||||
- Checks (String): This field can contain either a Prowler Check Name or an `*` (which applies to all the scanned checks).
|
||||
- Regions (List): This field contains a list of regions where this allowlist rule is applied (it can also contains an `*` to apply all scanned regions).
|
||||
- Resources (List): This field contains a list of regex expressions that applies to the resources that are wanted to be allowlisted.
|
||||
|
||||
<img src="/img/allowlist-row.png"/>
|
||||
|
||||
> Make sure that the used AWS credentials have `dynamodb:PartiQLSelect` permissions in the table.
|
||||
49
docs/tutorials/aws/organizations.md
Normal file
@@ -0,0 +1,49 @@
|
||||
# AWS Organizations
|
||||
## Get AWS Account details from your AWS Organization:
|
||||
|
||||
Prowler allows you to get additional information of the scanned account in CSV and JSON outputs. When scanning a single account you get the Account ID as part of the output.
|
||||
|
||||
If you have AWS Organizations Prowler can get your account details like Account Name, Email, ARN, Organization ID and Tags and you will have them next to every finding in the CSV and JSON outputs.
|
||||
|
||||
- In order to do that you can use the option `-O`/`--organizations-role <organizations_role_arn>`. See the following sample command:
|
||||
|
||||
```
|
||||
prowler aws -O arn:aws:iam::<management_organizations_account_id>:role/<role_name>
|
||||
```
|
||||
> Make sure the role in your AWS Organizatiosn management account has the permissions `organizations:ListAccounts*` and `organizations:ListTagsForResource`.
|
||||
|
||||
- In that command Prowler will scan the account and getting the account details from the AWS Organizations management account assuming a role and creating two reports with those details in JSON and CSV.
|
||||
|
||||
In the JSON output below (redacted) you can see tags coded in base64 to prevent breaking CSV or JSON due to its format:
|
||||
|
||||
```json
|
||||
"Account Email": "my-prod-account@domain.com",
|
||||
"Account Name": "my-prod-account",
|
||||
"Account ARN": "arn:aws:organizations::222222222222:account/o-abcde1234/111111111111",
|
||||
"Account Organization": "o-abcde1234",
|
||||
"Account tags": "\"eyJUYWdzIjpasf0=\""
|
||||
```
|
||||
|
||||
The additional fields in CSV header output are as follow:
|
||||
|
||||
```csv
|
||||
ACCOUNT_DETAILS_EMAIL,ACCOUNT_DETAILS_NAME,ACCOUNT_DETAILS_ARN,ACCOUNT_DETAILS_ORG,ACCOUNT_DETAILS_TAGS
|
||||
```
|
||||
|
||||
## Assume Role and across all accounts in AWS Organizations or just a list of accounts:
|
||||
|
||||
If you want to run Prowler across all accounts of AWS Organizations you can do this:
|
||||
|
||||
- First get a list of accounts that are not suspended:
|
||||
|
||||
```
|
||||
ACCOUNTS_IN_ORGS=$(aws organizations list-accounts --query Accounts[?Status==`ACTIVE`].Id --output text)
|
||||
```
|
||||
|
||||
- Then run Prowler to assume a role (same in all members) per each account, in this example it is just running one particular check:
|
||||
|
||||
```
|
||||
for accountId in $ACCOUNTS_IN_ORGS; do prowler aws -O arn:aws:iam::<management_organizations_account_id>:role/<role_name>; done
|
||||
```
|
||||
|
||||
- Using the same for loop it can be scanned a list of accounts with a variable like `ACCOUNTS_LIST='11111111111 2222222222 333333333'`
|
||||
24
docs/tutorials/aws/role-assumption.md
Normal file
@@ -0,0 +1,24 @@
|
||||
# AWS Assume Role
|
||||
|
||||
Prowler uses the AWS SDK (Boto3) underneath so it uses the same authentication methods.
|
||||
|
||||
However, there are few ways to run Prowler against multiple accounts using IAM Assume Role feature depending on each use case:
|
||||
|
||||
1. You can just set up your custom profile inside `~/.aws/config` with all needed information about the role to assume then call it with `prowler aws -p/--profile your-custom-profile`.
|
||||
|
||||
2. You can use `-R`/`--role <role_arn>` and Prowler will get those temporary credentials using `aws sts assume-role`, set them up as environment variables and run against that given account.
|
||||
```sh
|
||||
prowler aws -R arn:aws:iam::<account_id>:role/<role_name>
|
||||
```
|
||||
- Optionally, the session duration (in seconds, by deafult 3600) and the external ID of this role assumption can be defined:
|
||||
|
||||
```sh
|
||||
prowler aws -T/--session-duration <seconds> -I/--external-id <external_id> -R arn:aws:iam::<account_id>:role/<role_name>
|
||||
```
|
||||
|
||||
>To create a role to assume in multiple accounts easier either as CFN Stack or StackSet, look at [this CloudFormation template](iam/create_role_to_assume_cfn.yaml) and adapt it.
|
||||
|
||||
|
||||
> _NOTE 1 about Session Duration_: Depending on the mount of checks you run and the size of your infrastructure, Prowler may require more than 1 hour to finish. Use option `-T <seconds>` to allow up to 12h (43200 seconds). To allow more than 1h you need to modify _"Maximum CLI/API session duration"_ for that particular role, read more [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use.html#id_roles_use_view-role-max-session).
|
||||
|
||||
> _NOTE 2 about Session Duration_: Bear in mind that if you are using roles assumed by role chaining there is a hard limit of 1 hour so consider not using role chaining if possible, read more about that, in foot note 1 below the table [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use.html).
|
||||
38
docs/tutorials/aws/securityhub.md
Normal file
@@ -0,0 +1,38 @@
|
||||
# Security Hub Integration
|
||||
|
||||
Prowler supports natively and as **official integration** sending findings to [AWS Security Hub](https://aws.amazon.com/security-hub). This integration allows Prowler to import its findings to AWS Security Hub.
|
||||
|
||||
With Security Hub, you now have a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, and AWS Firewall Manager, as well as from AWS Partner solutions and from Prowler for free.
|
||||
|
||||
Before sending findings to Prowler, you will need to perform next steps:
|
||||
|
||||
1. Since Security Hub is a region based service, enable it in the region or regions you require. Use the AWS Management Console or using the AWS CLI with this command if you have enough permissions:
|
||||
- `aws securityhub enable-security-hub --region <region>`.
|
||||
2. Enable Prowler as partner integration integration. Use the AWS Management Console or using the AWS CLI with this command if you have enough permissions:
|
||||
- `aws securityhub enable-import-findings-for-product --region <region> --product-arn arn:aws:securityhub:<region>::product/prowler/prowler` (change region also inside the ARN).
|
||||
- Using the AWS Management Console:
|
||||

|
||||
3. Allow Prowler to import its findings to AWS Security Hub by adding the policy below to the role or user running Prowler:
|
||||
- [iam/prowler-security-hub.json](iam/prowler-security-hub.json)
|
||||
|
||||
Once it is enabled, it is as simple as running the command below (for all regions):
|
||||
|
||||
```sh
|
||||
./prowler aws -S
|
||||
```
|
||||
|
||||
or for only one filtered region like eu-west-1:
|
||||
|
||||
```sh
|
||||
./prowler -S -f eu-west-1
|
||||
```
|
||||
|
||||
> **Note 1**: It is recommended to send only fails to Security Hub and that is possible adding `-q` to the command.
|
||||
|
||||
> **Note 2**: Since Prowler perform checks to all regions by defauls you may need to filter by region when runing Security Hub integration, as shown in the example above. Remember to enable Security Hub in the region or regions you need by calling `aws securityhub enable-security-hub --region <region>` and run Prowler with the option `-f <region>` (if no region is used it will try to push findings in all regions hubs).
|
||||
|
||||
> **Note 3** to have updated findings in Security Hub you have to run Prowler periodically. Once a day or every certain amount of hours.
|
||||
|
||||
Once you run findings for first time you will be able to see Prowler findings in Findings section:
|
||||
|
||||

|
||||
27
docs/tutorials/azure/authentication.md
Normal file
@@ -0,0 +1,27 @@
|
||||
# Azure authentication
|
||||
|
||||
By default prowler uses Azure Python SDK identity package authentication methods using the classes `DefaultAzureCredential` and `InteractiveBrowserCredential`.
|
||||
This allows Prowler to authenticate against azure using the following methods:
|
||||
|
||||
- Service principal authentication by environment variables (Enterprise Application)
|
||||
- Current az cli credentials stored
|
||||
- Interactive browser authentication
|
||||
- Managed identity authentication
|
||||
|
||||
To launch the tool it is required to specify which method is used through the following flags:
|
||||
|
||||
```console
|
||||
# To use service principal authentication
|
||||
prowler azure --sp-env-auth
|
||||
|
||||
# To use az cli authentication
|
||||
prowler azure --az-cli-auth
|
||||
|
||||
# To use browser authentication
|
||||
prowler azure --browser-auth
|
||||
|
||||
# To use managed identity auth
|
||||
prowler azure --managed-identity-auth
|
||||
```
|
||||
|
||||
To use Prowler you need to set up also the permissions required to access your resources in your Azure account, to more details refer to [Requirements](getting-started/requirements.md)
|
||||
10
docs/tutorials/azure/subscriptions.md
Normal file
@@ -0,0 +1,10 @@
|
||||
# Azure subscriptions scope
|
||||
|
||||
By default Prowler is multisubscription, which means that is going to scan all the subscriptions is able to list. If you only assign permissions to one subscription it is going to scan a single one.
|
||||
Prowler also has the ability to limit the subscriptions to scan to a set passed as input argument, to do so:
|
||||
|
||||
```console
|
||||
prowler azure --az-cli-auth --subscription-ids <subscription ID 1> <subscription ID 2> ... <subscription ID N>
|
||||
```
|
||||
|
||||
Where you can pass from 1 up to N subscriptions to be scanned.
|
||||
3
docs/tutorials/compliance.md
Normal file
@@ -0,0 +1,3 @@
|
||||
--list-compliance List compliance frameworks
|
||||
--list-compliance-requirements [{ens_rd2022_aws}]
|
||||
--compliance {ens_rd2022_aws} [{ens_rd2022_aws} ...]
|
||||
48
docs/tutorials/logging.md
Normal file
@@ -0,0 +1,48 @@
|
||||
# Logging
|
||||
|
||||
Prowler has a logging feature to be as transparent as possible so you can see every action that is going on will the tool is been executing.
|
||||
|
||||
## Set Log Level
|
||||
|
||||
There are different log levels depending on the logging information that is desired to be displayed:
|
||||
|
||||
- **DEBUG**: it will show low-level logs of Python.
|
||||
- **INFO**: it will show all the API Calls that are being used in the provider.
|
||||
- **WARNING**: it will show the resources that are being **allowlisted**.
|
||||
- **ERROR**: it will show the errors, e.g., not authorized actions.
|
||||
- **CRITICAL**: default log level, if a critical log appears, it will **exit** Prowler’s execution.
|
||||
|
||||
You can establish the log level of Prowler with `--log-level` option:
|
||||
|
||||
```console
|
||||
prowler <provider> --log-level {DEBUG,INFO,WARNING,ERROR,CRITICAL}
|
||||
```
|
||||
|
||||
> By default, Prowler will run with the `CRITICAL` log level, since critical errors will abort the execution.
|
||||
|
||||
## Export Logs to File
|
||||
|
||||
Prowler allows you to export the logs in json format with `--log-file` option:
|
||||
|
||||
```console
|
||||
prowler <provider> --log-level {DEBUG,INFO,WARNING,ERROR,CRITICAL} --log-file <file_name>.json
|
||||
```
|
||||
|
||||
An example of a log file will be the following:
|
||||
|
||||
{
|
||||
"timestamp": "2022-12-01 16:45:56,399",
|
||||
"filename": "ec2_service.py:114",
|
||||
"level": "ERROR",
|
||||
"module": "ec2_service",
|
||||
"message": "eu-west-2 -- ClientError[102]: An error occurred (UnauthorizedOperation) when calling the DescribeSecurityGroups operation: You are not authorized to perform this operation."
|
||||
}
|
||||
{
|
||||
"timestamp": "2022-12-01 16:45:56,438",
|
||||
"filename": "ec2_service.py:134",
|
||||
"level": "ERROR",
|
||||
"module": "ec2_service",
|
||||
"message": "eu-west-2 -- ClientError[124]: An error occurred (UnauthorizedOperation) when calling the DescribeNetworkAcls operation: You are not authorized to perform this operation."
|
||||
}
|
||||
|
||||
> NOTE: Each finding is a `json` object.
|
||||
106
docs/tutorials/misc.md
Normal file
@@ -0,0 +1,106 @@
|
||||
# Miscellaneous
|
||||
## Prowler Version
|
||||
Show Prowler version:
|
||||
```console
|
||||
prowler <provider> -V/-v/--version
|
||||
```
|
||||
## Verbose
|
||||
Execute Prowler in verbose mode (like in Version 2):
|
||||
```console
|
||||
prowler <provider> --verbose
|
||||
```
|
||||
## Show only Fails
|
||||
Prowler can only display the failed findings:
|
||||
```console
|
||||
prowler <provider> -q/--quiet
|
||||
```
|
||||
## Hide Prowler Banner
|
||||
Prowler can run without showing its banner:
|
||||
```console
|
||||
prowler <provider> -b/--no-banner
|
||||
```
|
||||
## Checks
|
||||
Prowler has checks per provider, there are options related with them:
|
||||
|
||||
- List the available checks in the provider:
|
||||
```console
|
||||
prowler <provider> --list-checks
|
||||
```
|
||||
- Execute specific check(s):
|
||||
```console
|
||||
prowler <provider> -c/--checks s3_bucket_public_access
|
||||
```
|
||||
- Exclude specific check(s):
|
||||
```console
|
||||
prowler <provider> -e/--excluded-checks ec2 rds
|
||||
```
|
||||
- Execute checks that appears in a json file:
|
||||
```json
|
||||
<checks_list>.json
|
||||
|
||||
{
|
||||
"<provider>": [
|
||||
"<check_name_1",
|
||||
"<check_name_2",
|
||||
"<check_name_3",
|
||||
...
|
||||
],
|
||||
...
|
||||
}
|
||||
```
|
||||
```console
|
||||
prowler <provider> -C/--checks-file <checks_list>.json
|
||||
```
|
||||
|
||||
## Severities
|
||||
Each check of Prowler has a severity, there are options related with it:
|
||||
|
||||
- List the available checks in the provider:
|
||||
```console
|
||||
prowler <provider> --list-severities
|
||||
```
|
||||
- Execute specific severity(s):
|
||||
```console
|
||||
prowler <provider> --severity critical high
|
||||
```
|
||||
|
||||
## Service
|
||||
Prowler has services per provider, there are options related with them:
|
||||
|
||||
- List the available services in the provider:
|
||||
```console
|
||||
prowler <provider> --list-services
|
||||
```
|
||||
- Execute specific service(s):
|
||||
```console
|
||||
prowler <provider> -s/--services s3 iam
|
||||
```
|
||||
- Exclude specific service(s):
|
||||
```console
|
||||
prowler <provider> --excluded-services ec2 rds
|
||||
```
|
||||
|
||||
## Categories
|
||||
Prowler groups checks in different categories, there are options related with them:
|
||||
|
||||
- List the available categories in the provider:
|
||||
```console
|
||||
prowler <provider> --list-categories
|
||||
```
|
||||
- Execute specific category(s):
|
||||
```console
|
||||
prowler <provider> --categories
|
||||
```
|
||||
|
||||
## AWS
|
||||
|
||||
### Scan specific AWS Region
|
||||
Prowler can scan specific region(s) with:
|
||||
```console
|
||||
prowler <provider> -f/--filter-region eu-west-1 us-east-1
|
||||
```
|
||||
### Use AWS Profile
|
||||
Prowler can use your custom AWS Profile with:
|
||||
```console
|
||||
prowler <provider> -p/--profile <profile_name>
|
||||
```
|
||||
69
docs/tutorials/pentesting.md
Normal file
@@ -0,0 +1,69 @@
|
||||
# Pentesting
|
||||
|
||||
Prowler has some checks that analyse pentesting risks (Secrets, Internet Exposed, AuthN, AuthZ and more).
|
||||
|
||||
## Detect Secrets
|
||||
|
||||
Prowler uses `detect-secrets` library to search for any secrets that are stores in plaintext within your environment.
|
||||
|
||||
The actual checks that have this funcionality are:
|
||||
|
||||
1. autoscaling_find_secrets_ec2_launch_configuration
|
||||
- awslambda_function_no_secrets_in_code
|
||||
- awslambda_function_no_secrets_in_variables
|
||||
- cloudformation_outputs_find_secrets
|
||||
- ec2_instance_secrets_user_data
|
||||
- ecs_task_definitions_no_environment_secrets
|
||||
- ssm_document_secrets
|
||||
|
||||
To execute detect-secrets related checks, you can run the following command:
|
||||
|
||||
```console
|
||||
prowler <provider> --categories secrets
|
||||
```
|
||||
## Internet Exposed Resources
|
||||
|
||||
Several checks analyse resources that are exposed to the Internet, these are:
|
||||
|
||||
1. apigateway_endpoint_public
|
||||
- appstream_fleet_default_internet_access_disabled
|
||||
- awslambda_function_not_publicly_accessible
|
||||
- ec2_ami_public
|
||||
- ec2_ebs_public_snapshot
|
||||
- ec2_instance_internet_facing_with_instance_profile
|
||||
- ec2_instance_public_ip
|
||||
- ec2_networkacl_allow_ingress_any_port
|
||||
- ec2_securitygroup_allow_ingress_from_internet_to_any_port
|
||||
- ec2_securitygroup_allow_wide_open_public_ipv4
|
||||
- ec2_securitygroup_in_use_without_ingress_filtering
|
||||
- ecr_repositories_not_publicly_accessible
|
||||
- eks_control_plane_endpoint_access_restricted
|
||||
- eks_endpoints_not_publicly_accessible
|
||||
- eks_control_plane_endpoint_access_restricted
|
||||
- eks_endpoints_not_publicly_accessible
|
||||
- elbv2_internet_facing
|
||||
- kms_key_not_publicly_accessible
|
||||
- opensearch_service_domains_not_publicly_accessible
|
||||
- rds_instance_no_public_access
|
||||
- rds_snapshots_public_access
|
||||
- s3_bucket_policy_public_write_access
|
||||
- s3_bucket_public_access
|
||||
- sagemaker_notebook_instance_without_direct_internet_access_configured
|
||||
- sns_topics_not_publicly_accessible
|
||||
- sqs_queues_not_publicly_accessible
|
||||
|
||||
...
|
||||
|
||||
To execute internet-exposed related checks, you can run the following command:
|
||||
|
||||
```console
|
||||
prowler <provider> --categories internet-exposed
|
||||
```
|
||||
|
||||
### Shodan
|
||||
|
||||
Prowler allows you check if any elastic ip in your AWS Account is exposed in Shodan with `-N`/`--shodan <shodan_api_key>` option:
|
||||
|
||||
```console
|
||||
prowler aws --shodan <shodan_api_key> -c ec2_elastic_ip_shodan
|
||||
```
|
||||
231
docs/tutorials/reporting.md
Normal file
@@ -0,0 +1,231 @@
|
||||
# Reporting
|
||||
|
||||
By default, Prowler will generate a CSV and a JSON report, however you could generate an HTML or an JSON-ASFF report with `-M` or `--output-modes`:
|
||||
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html
|
||||
```
|
||||
|
||||
## Custom Output Flags
|
||||
By default, Prowler creates a file inside the `output` directory named `prowler-output-ACCOUNT_NUM-OUTPUT_DATE.format`.
|
||||
|
||||
However, both the output file name and directory can be personalised:
|
||||
|
||||
- Custom output report name: you can use the flag `-F`/`--output-filename`
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html -F <custom_report_name>
|
||||
```
|
||||
- Custom output directory: you can use the flag `-o`/`--output-directory`
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html -o <custom_report_directory>
|
||||
```
|
||||
> Both flags can be used simultainously to provide a custom directory and filename.
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html -F <custom_report_name> -o <custom_report_directory>
|
||||
```
|
||||
## Send report to AWS S3 Bucket
|
||||
|
||||
To save your report in an S3 bucket, use `-B`/`--output-bucket` to define a custom output bucket along with `-M` to define the output format that is going to be uploaded to S3:
|
||||
|
||||
```sh
|
||||
prowler <provider> -M csv -B my-bucket/folder/
|
||||
```
|
||||
|
||||
> In the case you do not want to use the assumed role credentials but the initial credentials to put the reports into the S3 bucket, use `-D`/`--output-bucket-no-assume` instead of `-B`/`--output-bucket.
|
||||
|
||||
> Make sure that the used credentials have s3:PutObject permissions in the S3 path where the reports are going to be uploaded.
|
||||
|
||||
## Output Formats
|
||||
|
||||
Prowler supports natively the following output formats:
|
||||
|
||||
- CSV
|
||||
- JSON
|
||||
- JSON-ASFF
|
||||
- HTML
|
||||
|
||||
Hereunder is the structure for each of the supported report formats by Prowler:
|
||||
|
||||
### CSV
|
||||
| ASSESSMENT_START_TIME | FINDING_UNIQUE_ID | PROVIDER | PROFILE | ACCOUNT_ID | ACCOUNT_NAME | ACCOUNT_EMAIL | ACCOUNT_ARN | ACCOUNT_ORG | ACCOUNT_TAGS | REGION | CHECK_ID | CHECK_TITLE | CHECK_TYPE | STATUS | STATUS_EXTENDED | SERVICE_NAME | SUBSERVICE_NAME | SEVERITY | RESOURCE_ID | RESOURCE_ARN | RESOURCE_TYPE | RESOURCE_DETAILS | RESOURCE_TAGS | DESCRIPTION | RISK | RELATED_URL | REMEDIATION_RECOMMENDATION_TEXT | REMEDIATION_RECOMMENDATION_URL | REMEDIATION_RECOMMENDATION_CODE_NATIVEIAC | REMEDIATION_RECOMMENDATION_CODE_TERRAFORM | REMEDIATION_RECOMMENDATION_CODE_CLI | REMEDIATION_RECOMMENDATION_CODE_OTHER | CATEGORIES | DEPENDS_ON | RELATED_TO | NOTES |
|
||||
| ------- | ----------- | ------ | -------- | ------------ | ----------- | ---------- | ---------- | --------------------- | -------------------------- | -------------- | ----------------- | ------------------------ | --------------- | ---------- | ----------------- | --------- | -------------- | ----------------- | ------------------ | --------------------- | -------------------- | ------------------- | ------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- | -------------------- |
|
||||
|
||||
### JSON
|
||||
|
||||
```
|
||||
[{
|
||||
"AssessmentStartTime": "2022-12-01T14:16:57.354413",
|
||||
"FindingUniqueId": "",
|
||||
"Provider": "aws",
|
||||
"Profile": "dev",
|
||||
"AccountId": "ACCOUNT_ID",
|
||||
"OrganizationsInfo": null,
|
||||
"Region": "eu-west-1",
|
||||
"CheckID": "rds_instance_minor_version_upgrade_enabled",
|
||||
"CheckTitle": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"CheckType": [],
|
||||
"ServiceName": "rds",
|
||||
"SubServiceName": "",
|
||||
"Status": "PASS",
|
||||
"StatusExtended": "RDS Instance rds-instance-id has minor version upgrade enabled.",
|
||||
"Severity": "low",
|
||||
"ResourceId": "rds-instance-id",
|
||||
"ResourceArn": "",
|
||||
"ResourceType": "AwsRdsDbInstance",
|
||||
"ResourceDetails": "",
|
||||
"Tags": {
|
||||
"Tag1Key": "value",
|
||||
"Tag2Key": "value"
|
||||
},
|
||||
"Description": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"Risk": "Auto Minor Version Upgrade is a feature that you can enable to have your database automatically upgraded when a new minor database engine version is available. Minor version upgrades often patch security vulnerabilities and fix bugs and therefore should be applied.",
|
||||
"RelatedUrl": "https://aws.amazon.com/blogs/database/best-practices-for-upgrading-amazon-rds-to-major-and-minor-versions-of-postgresql/",
|
||||
"Remediation": {
|
||||
"Code": {
|
||||
"NativeIaC": "https://docs.bridgecrew.io/docs/ensure-aws-db-instance-gets-all-minor-upgrades-automatically#cloudformation",
|
||||
"Terraform": "https://docs.bridgecrew.io/docs/ensure-aws-db-instance-gets-all-minor-upgrades-automatically#terraform",
|
||||
"CLI": "aws rds modify-db-instance --db-instance-identifier <db_instance_id> --auto-minor-version-upgrade --apply-immediately",
|
||||
"Other": "https://www.trendmicro.com/cloudoneconformity/knowledge-base/aws/RDS/rds-auto-minor-version-upgrade.html"
|
||||
},
|
||||
"Recommendation": {
|
||||
"Text": "Enable auto minor version upgrade for all databases and environments.",
|
||||
"Url": "https://aws.amazon.com/blogs/database/best-practices-for-upgrading-amazon-rds-to-major-and-minor-versions-of-postgresql/"
|
||||
}
|
||||
},
|
||||
"Categories": [],
|
||||
"DependsOn": [],
|
||||
"RelatedTo": [],
|
||||
"Notes": ""
|
||||
},{
|
||||
"AssessmentStartTime": "2022-12-01T14:16:57.354413",
|
||||
"FindingUniqueId": "",
|
||||
"Provider": "aws",
|
||||
"Profile": "dev",
|
||||
"AccountId": "ACCOUNT_ID",
|
||||
"OrganizationsInfo": null,
|
||||
"Region": "eu-west-1",
|
||||
"CheckID": "rds_instance_minor_version_upgrade_enabled",
|
||||
"CheckTitle": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"CheckType": [],
|
||||
"ServiceName": "rds",
|
||||
"SubServiceName": "",
|
||||
"Status": "PASS",
|
||||
"StatusExtended": "RDS Instance rds-instance-id has minor version upgrade enabled.",
|
||||
"Severity": "low",
|
||||
"ResourceId": "rds-instance-id",
|
||||
"ResourceArn": "",
|
||||
"ResourceType": "AwsRdsDbInstance",
|
||||
"ResourceDetails": "",
|
||||
"Tags": {
|
||||
"Tag1Key": "value",
|
||||
"Tag2Key": "value"
|
||||
},
|
||||
"Description": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"Risk": "Auto Minor Version Upgrade is a feature that you can enable to have your database automatically upgraded when a new minor database engine version is available. Minor version upgrades often patch security vulnerabilities and fix bugs and therefore should be applied.",
|
||||
"RelatedUrl": "https://aws.amazon.com/blogs/database/best-practices-for-upgrading-amazon-rds-to-major-and-minor-versions-of-postgresql/",
|
||||
"Remediation": {
|
||||
"Code": {
|
||||
"NativeIaC": "https://docs.bridgecrew.io/docs/ensure-aws-db-instance-gets-all-minor-upgrades-automatically#cloudformation",
|
||||
"Terraform": "https://docs.bridgecrew.io/docs/ensure-aws-db-instance-gets-all-minor-upgrades-automatically#terraform",
|
||||
"CLI": "aws rds modify-db-instance --db-instance-identifier <db_instance_id> --auto-minor-version-upgrade --apply-immediately",
|
||||
"Other": "https://www.trendmicro.com/cloudoneconformity/knowledge-base/aws/RDS/rds-auto-minor-version-upgrade.html"
|
||||
},
|
||||
"Recommendation": {
|
||||
"Text": "Enable auto minor version upgrade for all databases and environments.",
|
||||
"Url": "https://aws.amazon.com/blogs/database/best-practices-for-upgrading-amazon-rds-to-major-and-minor-versions-of-postgresql/"
|
||||
}
|
||||
},
|
||||
"Categories": [],
|
||||
"DependsOn": [],
|
||||
"RelatedTo": [],
|
||||
"Notes": ""
|
||||
}]
|
||||
```
|
||||
|
||||
> NOTE: Each finding is a `json` object.
|
||||
|
||||
### JSON-ASFF
|
||||
|
||||
```
|
||||
[{
|
||||
"SchemaVersion": "2018-10-08",
|
||||
"Id": "prowler-rds_instance_minor_version_upgrade_enabled-ACCOUNT_ID-eu-west-1-b1ade474a",
|
||||
"ProductArn": "arn:aws:securityhub:eu-west-1::product/prowler/prowler",
|
||||
"RecordState": "ACTIVE",
|
||||
"ProductFields": {
|
||||
"ProviderName": "Prowler",
|
||||
"ProviderVersion": "3.0-beta-21Nov2022",
|
||||
"ProwlerResourceName": "rds-instance-id"
|
||||
},
|
||||
"GeneratorId": "prowler-rds_instance_minor_version_upgrade_enabled",
|
||||
"AwsAccountId": "ACCOUNT_ID",
|
||||
"Types": [],
|
||||
"FirstObservedAt": "2022-12-01T13:16:57Z",
|
||||
"UpdatedAt": "2022-12-01T13:16:57Z",
|
||||
"CreatedAt": "2022-12-01T13:16:57Z",
|
||||
"Severity": {
|
||||
"Label": "LOW"
|
||||
},
|
||||
"Title": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"Description": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"Resources": [
|
||||
{
|
||||
"Type": "AwsRdsDbInstance",
|
||||
"Id": "rds-instance-id",
|
||||
"Partition": "aws",
|
||||
"Region": "eu-west-1"
|
||||
}
|
||||
],
|
||||
"Compliance": {
|
||||
"Status": "PASSED",
|
||||
"RelatedRequirements": []
|
||||
},
|
||||
"Remediation": {
|
||||
"Recommendation": {
|
||||
"Text": "Enable auto minor version upgrade for all databases and environments.",
|
||||
"Url": "https://aws.amazon.com/blogs/database/best-practices-for-upgrading-amazon-rds-to-major-and-minor-versions-of-postgresql/"
|
||||
}
|
||||
}
|
||||
},{
|
||||
"SchemaVersion": "2018-10-08",
|
||||
"Id": "prowler-rds_instance_minor_version_upgrade_enabled-ACCOUNT_ID-eu-west-1-06d21d75e",
|
||||
"ProductArn": "arn:aws:securityhub:eu-west-1::product/prowler/prowler",
|
||||
"RecordState": "ACTIVE",
|
||||
"ProductFields": {
|
||||
"ProviderName": "Prowler",
|
||||
"ProviderVersion": "3.0-beta-21Nov2022",
|
||||
"ProwlerResourceName": "rds-instance-id"
|
||||
},
|
||||
"GeneratorId": "prowler-rds_instance_minor_version_upgrade_enabled",
|
||||
"AwsAccountId": "ACCOUNT_ID",
|
||||
"Types": [],
|
||||
"FirstObservedAt": "2022-12-01T13:16:57Z",
|
||||
"UpdatedAt": "2022-12-01T13:16:57Z",
|
||||
"CreatedAt": "2022-12-01T13:16:57Z",
|
||||
"Severity": {
|
||||
"Label": "LOW"
|
||||
},
|
||||
"Title": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"Description": "Ensure RDS instances have minor version upgrade enabled.",
|
||||
"Resources": [
|
||||
{
|
||||
"Type": "AwsRdsDbInstance",
|
||||
"Id": "rds-instance-id",
|
||||
"Partition": "aws",
|
||||
"Region": "eu-west-1"
|
||||
}
|
||||
],
|
||||
"Compliance": {
|
||||
"Status": "PASSED",
|
||||
"RelatedRequirements": []
|
||||
},
|
||||
"Remediation": {
|
||||
"Recommendation": {
|
||||
"Text": "Enable auto minor version upgrade for all databases and environments.",
|
||||
"Url": "https://aws.amazon.com/blogs/database/best-practices-for-upgrading-amazon-rds-to-major-and-minor-versions-of-postgresql/"
|
||||
}
|
||||
}
|
||||
}]
|
||||
```
|
||||
|
||||
> NOTE: Each finding is a `json` object.
|
||||
68
mkdocs.yml
Normal file
@@ -0,0 +1,68 @@
|
||||
# Project information
|
||||
site_name: Prowler Documentation
|
||||
site_url: https://docs.prowler.pro/
|
||||
site_description: >-
|
||||
Prowler Documentation Site
|
||||
|
||||
# Theme Configuration
|
||||
theme:
|
||||
language: en
|
||||
logo: img/ProwlerPro-icon.svg
|
||||
name: material
|
||||
favicon: img/ProwlerPro-icon.svg
|
||||
features:
|
||||
- navigation.tabs
|
||||
- navigation.tabs.sticky
|
||||
- navigation.sections
|
||||
- navigation.top
|
||||
palette:
|
||||
primary: black
|
||||
accent: green
|
||||
|
||||
edit_uri: ""
|
||||
# Prowler OSS Repository
|
||||
repo_url: https://github.com/prowler-cloud/prowler/
|
||||
repo_name: prowler-cloud/prowler
|
||||
|
||||
nav:
|
||||
- Getting Started:
|
||||
- Overview: index.md
|
||||
- Requirements: getting-started/requirements.md
|
||||
- Tutorials:
|
||||
- Miscellaneous: tutorials/misc.md
|
||||
- Reporting: tutorials/reporting.md
|
||||
- Compliance: tutorials/compliance.md
|
||||
- Logging: tutorials/logging.md
|
||||
- Allowlist: tutorials/allowlist.md
|
||||
- Pentesting: tutorials/pentesting.md
|
||||
- AWS:
|
||||
- Assume Role: tutorials/aws/role-assumption.md
|
||||
- Security Hub: tutorials/aws/securityhub.md
|
||||
- AWS Organizations: tutorials/aws/organizations.md
|
||||
- Azure:
|
||||
- Authentication: tutorials/azure/authentication.md
|
||||
- Subscriptions: tutorials/azure/subscriptions.md
|
||||
- Contact Us: contact.md
|
||||
- About: about.md
|
||||
# Customization
|
||||
extra:
|
||||
consent:
|
||||
title: Cookie consent
|
||||
description: >-
|
||||
We use cookies to recognize your repeated visits and preferences, as well
|
||||
as to measure the effectiveness of our documentation and whether users
|
||||
find what they're searching for. With your consent, you're helping us to
|
||||
make our documentation better.
|
||||
analytics:
|
||||
provider: google
|
||||
property: G-H5TFH6WJRQ
|
||||
social:
|
||||
- icon: fontawesome/brands/github
|
||||
link: https://github.com/prowler-cloud
|
||||
- icon: fontawesome/brands/docker
|
||||
link: https://hub.docker.com/r/toniblyx
|
||||
- icon: fontawesome/brands/twitter
|
||||
link: https://twitter.com/toniblyx
|
||||
|
||||
# Copyright
|
||||
copyright: Copyright © 2022 Toni de la Fuente, Maintained by the Prowler Team</a>.
|
||||
@@ -17,7 +17,7 @@ Allowlist:
|
||||
Resources:
|
||||
- "test" # Will ignore every resource containing the string "test" in every account and region
|
||||
|
||||
"098765432109":
|
||||
"*":
|
||||
Checks:
|
||||
"s3_bucket_object_versioning":
|
||||
Regions:
|
||||
|
||||
25
prowler
@@ -58,13 +58,22 @@ if __name__ == "__main__":
|
||||
# Arguments to set checks to run
|
||||
# The following arguments needs to be set exclusivelly
|
||||
group = parser.add_mutually_exclusive_group()
|
||||
group.add_argument("-c", "--checks", nargs="+", help="List of checks")
|
||||
group.add_argument("-C", "--checks-file", nargs="?", help="List of checks")
|
||||
group.add_argument("-s", "--services", nargs="+", help="List of services")
|
||||
group.add_argument(
|
||||
"-c", "--checks", nargs="+", help="List of checks to be executed."
|
||||
)
|
||||
group.add_argument(
|
||||
"-C",
|
||||
"--checks-file",
|
||||
nargs="?",
|
||||
help="Json file containing checks to be executed.",
|
||||
)
|
||||
group.add_argument(
|
||||
"-s", "--services", nargs="+", help="List of services to be executed."
|
||||
)
|
||||
group.add_argument(
|
||||
"--severity",
|
||||
nargs="+",
|
||||
help="List of severities [informational, low, medium, high, critical]",
|
||||
help="List of severities to be executed [informational, low, medium, high, critical]",
|
||||
choices=["informational", "low", "medium", "high", "critical"],
|
||||
)
|
||||
group.add_argument(
|
||||
@@ -73,7 +82,9 @@ if __name__ == "__main__":
|
||||
help="Compliance Framework to check against for. The format should be the following: framework_version_provider (e.g.: ens_rd2022_aws)",
|
||||
choices=["ens_rd2022_aws", "cis_1.4_aws", "cis_1.5_aws"],
|
||||
)
|
||||
group.add_argument("--categories", nargs="+", help="List of categories", default=[])
|
||||
group.add_argument(
|
||||
"--categories", nargs="+", help="List of categories to be executed.", default=[]
|
||||
)
|
||||
|
||||
# Exclude checks options
|
||||
parser.add_argument("-e", "--excluded-checks", nargs="+", help="Checks to exclude")
|
||||
@@ -163,7 +174,7 @@ if __name__ == "__main__":
|
||||
"-M",
|
||||
"--output-modes",
|
||||
nargs="+",
|
||||
help="Output mode, by default csv",
|
||||
help="Output mode, by default csv and json",
|
||||
default=["csv", "json"],
|
||||
choices=["csv", "json", "json-asff", "html"],
|
||||
)
|
||||
@@ -220,7 +231,7 @@ if __name__ == "__main__":
|
||||
"--allowlist-file",
|
||||
nargs="?",
|
||||
default=None,
|
||||
help="Path for allowlist yaml file, by default is 'providers/aws/allowlist.yaml'. See default yaml for reference and format.",
|
||||
help="Path for allowlist yaml file, supports local file, S3 URI or DynamoDB ARN. See example yaml in 'providers/allowlist.yaml' for reference and format.",
|
||||
)
|
||||
parser.add_argument(
|
||||
"--verbose",
|
||||
|
||||
3
requirements.txt
Normal file
@@ -0,0 +1,3 @@
|
||||
# Documentation static site generator & deployment tool
|
||||
mkdocs>=1.3.0
|
||||
mkdocs-material>=8.2.1
|
||||