mirror of
https://github.com/prowler-cloud/prowler.git
synced 2026-01-25 02:08:11 +00:00
Compare commits
634 Commits
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
0fa725d2d0 | ||
|
|
2580d820ec | ||
|
|
3f3888f499 | ||
|
|
b20a532ab5 | ||
|
|
b11c9991a3 | ||
|
|
fd9cbe6ba3 | ||
|
|
227b1db493 | ||
|
|
10d8c12913 | ||
|
|
d9a1cc333e | ||
|
|
d1670c8347 | ||
|
|
b03bc8fc0b | ||
|
|
79c975ab9c | ||
|
|
68cf285fb9 | ||
|
|
36ba0ffb1f | ||
|
|
d2b1818700 | ||
|
|
2df02acbd8 | ||
|
|
7fd11b2f0e | ||
|
|
47bab87603 | ||
|
|
1835e1df98 | ||
|
|
dc88b033a0 | ||
|
|
0f784e34db | ||
|
|
698f299edf | ||
|
|
172bb36dfb | ||
|
|
4b1e6c7493 | ||
|
|
6d5c277c73 | ||
|
|
2d4b7ce499 | ||
|
|
3ee3a3b2f1 | ||
|
|
e9e6ff0e24 | ||
|
|
e0c6de76d4 | ||
|
|
5c2a411982 | ||
|
|
08d65cbc41 | ||
|
|
9d2bf429c1 | ||
|
|
d34f863bd4 | ||
|
|
b4abf1c2c7 | ||
|
|
68baaf589e | ||
|
|
be74e41d84 | ||
|
|
848122b0ec | ||
|
|
0edcb7c0d9 | ||
|
|
cc58e06b5e | ||
|
|
0d6ca606ea | ||
|
|
75ee93789f | ||
|
|
05daddafbf | ||
|
|
7bbce6725d | ||
|
|
789b211586 | ||
|
|
826a043748 | ||
|
|
6761048298 | ||
|
|
738fc9acad | ||
|
|
43c0540de7 | ||
|
|
2d1c3d8121 | ||
|
|
f48a5c650d | ||
|
|
66c18eddb8 | ||
|
|
fdd2ee6365 | ||
|
|
c207f60ad8 | ||
|
|
0eaa95c8c0 | ||
|
|
df2fca5935 | ||
|
|
dcaf5d9c7d | ||
|
|
0112969a97 | ||
|
|
3ec0f3d69c | ||
|
|
5555d300a1 | ||
|
|
8155ef4b60 | ||
|
|
a12402f6c8 | ||
|
|
cf28b814cb | ||
|
|
b05f67db19 | ||
|
|
260f4659d5 | ||
|
|
9e700f298c | ||
|
|
56510734c4 | ||
|
|
3938a4d14e | ||
|
|
fa3b9eeeaf | ||
|
|
eb9d6fa25c | ||
|
|
b53307c1c2 | ||
|
|
c3fc708a66 | ||
|
|
b34ffbe6d0 | ||
|
|
f364315e48 | ||
|
|
3ddb5a13a5 | ||
|
|
a24cc399a4 | ||
|
|
305f4b2688 | ||
|
|
9823171d65 | ||
|
|
4761bd8fda | ||
|
|
9c22698723 | ||
|
|
e3892bbcc6 | ||
|
|
629b156f52 | ||
|
|
c45dd47d34 | ||
|
|
ef8831f784 | ||
|
|
c5a42cf5de | ||
|
|
90ebbfc20f | ||
|
|
17cd0dc91d | ||
|
|
fa1f42af59 | ||
|
|
f45ea1ab53 | ||
|
|
0dde3fe483 | ||
|
|
277dc7dd09 | ||
|
|
3215d0b856 | ||
|
|
0167d5efcd | ||
|
|
b48ac808a6 | ||
|
|
616524775c | ||
|
|
5832849b11 | ||
|
|
467c5d01e9 | ||
|
|
24711a2f39 | ||
|
|
24e8286f35 | ||
|
|
e8a1378ad0 | ||
|
|
76bb418ea9 | ||
|
|
cd8770a3e3 | ||
|
|
da834c0935 | ||
|
|
024ffb1117 | ||
|
|
eed7ab9793 | ||
|
|
032feb343f | ||
|
|
eabccba3fa | ||
|
|
d86d656316 | ||
|
|
fa73c91b0b | ||
|
|
2eee50832d | ||
|
|
b40736918b | ||
|
|
ffb1a2e30f | ||
|
|
d6c3c0c6c1 | ||
|
|
ee251721ac | ||
|
|
fdbb9195d5 | ||
|
|
c68b08d9af | ||
|
|
3653bbfca0 | ||
|
|
05c7cc7277 | ||
|
|
5670bf099b | ||
|
|
0c324b0f09 | ||
|
|
968557e38e | ||
|
|
882cdebacb | ||
|
|
07753e1774 | ||
|
|
5b984507fc | ||
|
|
27df481967 | ||
|
|
0943031f23 | ||
|
|
2d95168de0 | ||
|
|
97cae8f92c | ||
|
|
eb213bac92 | ||
|
|
8187788b2c | ||
|
|
c80e08abce | ||
|
|
42fd851e5c | ||
|
|
70e4ebccab | ||
|
|
140f87c741 | ||
|
|
b0d756123e | ||
|
|
6188c92916 | ||
|
|
34c6f96728 | ||
|
|
50fd047c0b | ||
|
|
5bcc05b536 | ||
|
|
ce7d6c8dd5 | ||
|
|
d87a1e28b4 | ||
|
|
227306c572 | ||
|
|
45c2691f89 | ||
|
|
d0c81245b8 | ||
|
|
e494afb1aa | ||
|
|
ecc3c1cf3b | ||
|
|
228b16416a | ||
|
|
17eb74842a | ||
|
|
c01ff74c73 | ||
|
|
f88613b26d | ||
|
|
3464f4241f | ||
|
|
849b703828 | ||
|
|
4b935a40b6 | ||
|
|
5873a23ccb | ||
|
|
eae2786825 | ||
|
|
6407386de5 | ||
|
|
3fe950723f | ||
|
|
52bf6acd46 | ||
|
|
9590e7d7e0 | ||
|
|
7a08140a2d | ||
|
|
d1491cfbd1 | ||
|
|
695b80549d | ||
|
|
11c60a637f | ||
|
|
844ad70bb9 | ||
|
|
5ac7cde577 | ||
|
|
ce3ef0550f | ||
|
|
813f3e7d42 | ||
|
|
d03f97af6b | ||
|
|
019ab0286d | ||
|
|
c6647b4706 | ||
|
|
f913536d88 | ||
|
|
640d1bd176 | ||
|
|
66baccf528 | ||
|
|
6e6dacbace | ||
|
|
cdbb10fb26 | ||
|
|
c34ba3918c | ||
|
|
fa228c876c | ||
|
|
2f4d0af7d7 | ||
|
|
2d3e5235a9 | ||
|
|
8e91ccaa54 | ||
|
|
6955658b36 | ||
|
|
dbb44401fd | ||
|
|
b42ed70c84 | ||
|
|
a28276d823 | ||
|
|
fa4b27dd0e | ||
|
|
0be44d5c49 | ||
|
|
2514596276 | ||
|
|
7008d2a953 | ||
|
|
2539fedfc4 | ||
|
|
b453df7591 | ||
|
|
9e5d5edcba | ||
|
|
2d5de6ff99 | ||
|
|
259e9f1c17 | ||
|
|
daeb53009e | ||
|
|
f12d271ca5 | ||
|
|
965185ca3b | ||
|
|
9c484f6a78 | ||
|
|
de18c3c722 | ||
|
|
9be753b281 | ||
|
|
d6ae122de1 | ||
|
|
c6b90044f2 | ||
|
|
14898b6422 | ||
|
|
26294b0759 | ||
|
|
6da45b5c2b | ||
|
|
674332fddd | ||
|
|
ab8942d05a | ||
|
|
29790b8a5c | ||
|
|
4a4c26ffeb | ||
|
|
25c9bc07b2 | ||
|
|
d22d4c4c83 | ||
|
|
d88640fd20 | ||
|
|
57a2fca3a4 | ||
|
|
f796688c84 | ||
|
|
d6bbf8b7cc | ||
|
|
37ec460f64 | ||
|
|
004b9c95e4 | ||
|
|
86e27b465a | ||
|
|
5e9afddc3a | ||
|
|
de281535b1 | ||
|
|
9df7def14e | ||
|
|
5b9db9795d | ||
|
|
7d2ce7e6ab | ||
|
|
3e807af2b2 | ||
|
|
4c64dc7885 | ||
|
|
e7a7874b34 | ||
|
|
c78a47788b | ||
|
|
922698c5d9 | ||
|
|
8e8a490936 | ||
|
|
231bc0605f | ||
|
|
0298ff9478 | ||
|
|
33a25dcf0e | ||
|
|
54c16e3cdb | ||
|
|
28a978acc2 | ||
|
|
bea26a461f | ||
|
|
ed54c5b8b9 | ||
|
|
13316b68aa | ||
|
|
043986f35b | ||
|
|
2dc4421dd6 | ||
|
|
6c16e2bca2 | ||
|
|
c2b4a8e115 | ||
|
|
63b7bc8794 | ||
|
|
f41ae74ae2 | ||
|
|
98689d223e | ||
|
|
f19cf21146 | ||
|
|
24e19e6b18 | ||
|
|
08376cb15e | ||
|
|
5f6e4663c0 | ||
|
|
9b91c00fcc | ||
|
|
229ab88c2f | ||
|
|
8863d13578 | ||
|
|
e07fc9fbb9 | ||
|
|
0164574fdd | ||
|
|
98eec332d8 | ||
|
|
3d2986fc64 | ||
|
|
29e7f8581e | ||
|
|
4ee3f6c87a | ||
|
|
b8c7440e1f | ||
|
|
d49ff8d9a4 | ||
|
|
07198042bd | ||
|
|
c7a9492e96 | ||
|
|
360c6f3c1c | ||
|
|
89aab4acd5 | ||
|
|
d9b3e842d9 | ||
|
|
3ac4dc8392 | ||
|
|
0d1a5318ec | ||
|
|
94b7a219fd | ||
|
|
ba3eb71abd | ||
|
|
bbc9e11205 | ||
|
|
75571e4266 | ||
|
|
4e879271a0 | ||
|
|
552e0fefc3 | ||
|
|
cb7439a831 | ||
|
|
35d6b8bbc6 | ||
|
|
48b9220ffc | ||
|
|
5537981877 | ||
|
|
711f24a5b2 | ||
|
|
5d2b8bc8aa | ||
|
|
f6ea10db2d | ||
|
|
fc38ba3acb | ||
|
|
0830ad268f | ||
|
|
e633664c2a | ||
|
|
d4c7d9a60a | ||
|
|
5ee0d964f3 | ||
|
|
ba5e0f145f | ||
|
|
34eb9cc063 | ||
|
|
a795fdc40d | ||
|
|
24cba4c4ca | ||
|
|
3d13f4bb9b | ||
|
|
e713d0d321 | ||
|
|
4e34be87a1 | ||
|
|
07307d37a1 | ||
|
|
81463181bc | ||
|
|
02e57927fc | ||
|
|
36925f0dbd | ||
|
|
f9b985e03d | ||
|
|
598ad62b92 | ||
|
|
ea929ab713 | ||
|
|
04e56ced58 | ||
|
|
2278565b86 | ||
|
|
afd0c56b44 | ||
|
|
5ebdf66d22 | ||
|
|
177d8a72a7 | ||
|
|
03ef80dd8e | ||
|
|
6f9825362a | ||
|
|
2167154064 | ||
|
|
f88b35bd80 | ||
|
|
6b9520338e | ||
|
|
438c087856 | ||
|
|
2a43274b06 | ||
|
|
20a9336867 | ||
|
|
c921782714 | ||
|
|
776ac9e3d4 | ||
|
|
d02bd9b717 | ||
|
|
50070e8fe7 | ||
|
|
e3e3b3e279 | ||
|
|
38fba297e8 | ||
|
|
52d65ee4e8 | ||
|
|
9ad2f33dd8 | ||
|
|
02ae23b11d | ||
|
|
70c6d6e7ae | ||
|
|
8efebf992f | ||
|
|
b9be94bcc5 | ||
|
|
e6310c32ac | ||
|
|
654b4702d0 | ||
|
|
262b5a7ee5 | ||
|
|
ef0d4fe34b | ||
|
|
c08342f40c | ||
|
|
e7796268b5 | ||
|
|
0cbe80d2ab | ||
|
|
11d3ba70a0 | ||
|
|
c30e4c4867 | ||
|
|
d1e5087c18 | ||
|
|
618dd442e3 | ||
|
|
7f26fdf2d0 | ||
|
|
64090474e1 | ||
|
|
a69c28713a | ||
|
|
1d4b3095af | ||
|
|
ff75125af8 | ||
|
|
aa0025abbe | ||
|
|
c9436da235 | ||
|
|
12f1eaace7 | ||
|
|
09ef8aba0f | ||
|
|
08c094b8a5 | ||
|
|
e9fb4410cd | ||
|
|
cbdda22a33 | ||
|
|
fe906477da | ||
|
|
b03df619df | ||
|
|
53d89d8d17 | ||
|
|
1e5a1f3e1f | ||
|
|
6efe2979c6 | ||
|
|
92cc2c8e69 | ||
|
|
50dd2e4179 | ||
|
|
7a8fd9c3d3 | ||
|
|
d5a3fc490b | ||
|
|
13f948062b | ||
|
|
b965fda226 | ||
|
|
f9d67f0e9d | ||
|
|
4dfa20e40b | ||
|
|
d5edbaa3a9 | ||
|
|
0cd5ce8c29 | ||
|
|
1c50a87ca2 | ||
|
|
efa83e05e4 | ||
|
|
76a694d043 | ||
|
|
571280f0cd | ||
|
|
c2fc01608e | ||
|
|
2ba144843a | ||
|
|
458dadc9b6 | ||
|
|
6ed0c59762 | ||
|
|
54fbaa808e | ||
|
|
f0db63da35 | ||
|
|
9b8c80b74d | ||
|
|
0c23b6af84 | ||
|
|
1189177079 | ||
|
|
794402e92d | ||
|
|
0de6d87af5 | ||
|
|
567c150eaa | ||
|
|
7ea9225277 | ||
|
|
df25ead15a | ||
|
|
5227d57a55 | ||
|
|
8db86992aa | ||
|
|
79c09e613b | ||
|
|
99d1cea537 | ||
|
|
98bc3f18fe | ||
|
|
b007d01057 | ||
|
|
ea85e0824b | ||
|
|
d75b48877d | ||
|
|
94bda8c17d | ||
|
|
f05cb2859e | ||
|
|
3c6254f086 | ||
|
|
d9dc6c0a49 | ||
|
|
3cfe1b8376 | ||
|
|
83275c5fd0 | ||
|
|
e4698b5843 | ||
|
|
c4b134c0b5 | ||
|
|
5065cdb9e6 | ||
|
|
f72be9a1e4 | ||
|
|
a53f9eb294 | ||
|
|
44e0eedac2 | ||
|
|
d894556191 | ||
|
|
00cac892a7 | ||
|
|
167d332257 | ||
|
|
258abf6fe3 | ||
|
|
451b362c52 | ||
|
|
ff6b433661 | ||
|
|
3af2a44c70 | ||
|
|
7f712e4d72 | ||
|
|
28dee33e4f | ||
|
|
2d0b503f9f | ||
|
|
b0b706e2f4 | ||
|
|
0391fad32b | ||
|
|
167902616c | ||
|
|
ea42a6274b | ||
|
|
65e72d6937 | ||
|
|
bb5ba8c37c | ||
|
|
f5e5921abc | ||
|
|
80a8cfb6a6 | ||
|
|
4e34040e62 | ||
|
|
ba2620d91d | ||
|
|
c2ae4a5efd | ||
|
|
62c1ce73bb | ||
|
|
bab6380d68 | ||
|
|
9502355d22 | ||
|
|
a82d9591ab | ||
|
|
d8fe11f393 | ||
|
|
df5963082c | ||
|
|
c3980e4f27 | ||
|
|
a7155300d3 | ||
|
|
b622fe7229 | ||
|
|
2ddf3c8881 | ||
|
|
38ba009794 | ||
|
|
a55649b3e1 | ||
|
|
fdf80ed89d | ||
|
|
2da27d59b6 | ||
|
|
b67e718412 | ||
|
|
b05286f455 | ||
|
|
2a5f032a52 | ||
|
|
27a79d9c8c | ||
|
|
7ff72c048a | ||
|
|
388c0b2b9f | ||
|
|
bb09267f2a | ||
|
|
0cd13b90f4 | ||
|
|
fbb39a364e | ||
|
|
7bffe6b2d5 | ||
|
|
df4b89366c | ||
|
|
05075d6508 | ||
|
|
5e40d93d63 | ||
|
|
c2f5177afa | ||
|
|
e5e01e51a9 | ||
|
|
8f802f1241 | ||
|
|
a54372e05e | ||
|
|
f964439a15 | ||
|
|
309c1e004b | ||
|
|
9d91250f05 | ||
|
|
1f7262aaaa | ||
|
|
9a5e433489 | ||
|
|
d1f5d58eeb | ||
|
|
e3d118f5bc | ||
|
|
1a11f5777a | ||
|
|
b3e57ca3e5 | ||
|
|
1a70a45805 | ||
|
|
989638a42d | ||
|
|
9204142eaf | ||
|
|
af1d85ae75 | ||
|
|
25d92ca4b0 | ||
|
|
52a3e990c6 | ||
|
|
1370e0dec4 | ||
|
|
f99a89eae2 | ||
|
|
9954763356 | ||
|
|
538496ed6b | ||
|
|
7d80a9d048 | ||
|
|
a0ef56f245 | ||
|
|
e016fb2d6b | ||
|
|
62081cb399 | ||
|
|
bfc8c90abb | ||
|
|
967990b76d | ||
|
|
6ff9f30473 | ||
|
|
025b0547cd | ||
|
|
3370475fe9 | ||
|
|
12896cceaa | ||
|
|
62ffe26b42 | ||
|
|
c83c4d0892 | ||
|
|
9ff9b68d91 | ||
|
|
daa299c7a6 | ||
|
|
67b5de205b | ||
|
|
5a9c064943 | ||
|
|
24ca19d502 | ||
|
|
d2d2c75967 | ||
|
|
684b7fe0b8 | ||
|
|
2c5320a0b0 | ||
|
|
30738d7810 | ||
|
|
5281d521f4 | ||
|
|
58bdbadb11 | ||
|
|
e9b2f1d2fb | ||
|
|
8c8763a620 | ||
|
|
6497f7bfe8 | ||
|
|
9b035230ac | ||
|
|
9d3bff9e54 | ||
|
|
3b86b3ac77 | ||
|
|
c87327bb77 | ||
|
|
c9880b953f | ||
|
|
b187bf12c2 | ||
|
|
19ab29628f | ||
|
|
bbecd505eb | ||
|
|
69d3a9e363 | ||
|
|
f5873fe0d7 | ||
|
|
4762e1cc4c | ||
|
|
8ae989cce8 | ||
|
|
c6adf3a6d8 | ||
|
|
976e07c125 | ||
|
|
7c1dc1c977 | ||
|
|
3e749dd652 | ||
|
|
adf04ba632 | ||
|
|
f7842fdcdd | ||
|
|
b2976984d3 | ||
|
|
7e1b0d13c7 | ||
|
|
8487777f96 | ||
|
|
2d86254549 | ||
|
|
e77486f771 | ||
|
|
53f8a9698f | ||
|
|
bd6eb723dd | ||
|
|
5c78e6b171 | ||
|
|
44ce95979b | ||
|
|
44ce00d6e9 | ||
|
|
df0925394b | ||
|
|
5b5b0b0405 | ||
|
|
6e73321a95 | ||
|
|
d09020d144 | ||
|
|
e2a8fa8738 | ||
|
|
1119ee54af | ||
|
|
e6cd7c838f | ||
|
|
2b59068e50 | ||
|
|
5cc3888022 | ||
|
|
78975c286a | ||
|
|
7a40d9c44b | ||
|
|
460b71e3d9 | ||
|
|
107070e6e2 | ||
|
|
fb176f56d0 | ||
|
|
f67dc57384 | ||
|
|
dc7c0cd981 | ||
|
|
5cda2ad19f | ||
|
|
470b2ae369 | ||
|
|
14ee08ce6d | ||
|
|
c85b2567f7 | ||
|
|
ef110128f2 | ||
|
|
1fc249e772 | ||
|
|
7388cb33d4 | ||
|
|
f40c8f2dc5 | ||
|
|
eb914d03ce | ||
|
|
e087f2e1b6 | ||
|
|
f0c24d5152 | ||
|
|
44f514f02c | ||
|
|
a63c42f59c | ||
|
|
65185943ca | ||
|
|
de1f707434 | ||
|
|
0d0e00a8bd | ||
|
|
5054b82030 | ||
|
|
182d0381c3 | ||
|
|
fb0429b2a5 | ||
|
|
c7a43b09ce | ||
|
|
d18b430c16 | ||
|
|
9b4415f7b3 | ||
|
|
6c36c599a5 | ||
|
|
a6fb000266 | ||
|
|
92024e2b0e | ||
|
|
b229c01450 | ||
|
|
15867d3ef6 | ||
|
|
5abd7817af | ||
|
|
fa0fdbf0d1 | ||
|
|
f30245bb15 | ||
|
|
bc5df671dd | ||
|
|
a796545da5 | ||
|
|
6e58991986 | ||
|
|
85a6634a56 | ||
|
|
5541ec0763 | ||
|
|
a9aabd0082 | ||
|
|
cbd375f5d0 | ||
|
|
de96894a4d | ||
|
|
5e40fc28c9 | ||
|
|
0b34940e20 | ||
|
|
f93dfe5e78 | ||
|
|
b59042d9e9 | ||
|
|
0c2ed53c54 | ||
|
|
fe474ae9df | ||
|
|
6f0d42a881 | ||
|
|
5e479a5050 | ||
|
|
dfbc618d44 | ||
|
|
9f82a8a6d6 | ||
|
|
476d93b33e | ||
|
|
9895f9f595 | ||
|
|
510cca6b29 | ||
|
|
66d2b7b4d9 | ||
|
|
da76f69e51 | ||
|
|
ed1572d2d9 | ||
|
|
7d0a95e98f | ||
|
|
67834c3f8b | ||
|
|
a5e58ad9ce | ||
|
|
5cb363c389 | ||
|
|
b80c7222ea | ||
|
|
611bd909ef | ||
|
|
db3de2d69e | ||
|
|
7b9fae5605 | ||
|
|
d47bb09b2a | ||
|
|
b2899bda69 | ||
|
|
11652838e2 | ||
|
|
a1dcc1310a | ||
|
|
7e2303a732 | ||
|
|
0d7214a4a6 | ||
|
|
cbd23c7fb1 | ||
|
|
a2b40caeda | ||
|
|
66d57a3d36 | ||
|
|
2288702d26 | ||
|
|
cdbf62a9e5 | ||
|
|
25dc6c4a20 | ||
|
|
af2bdc37ea | ||
|
|
438ef9f348 | ||
|
|
6ac6ef359f | ||
|
|
b07b7f3f26 | ||
|
|
ecefda11c7 | ||
|
|
21f8f56c18 | ||
|
|
e52ab12696 | ||
|
|
b89b883741 | ||
|
|
f694a6d12a | ||
|
|
8abcc5988d | ||
|
|
9d5e43e6a2 | ||
|
|
162852634e | ||
|
|
33c6801501 | ||
|
|
eb679f50f1 | ||
|
|
36fcab17f3 | ||
|
|
b22faa01ea | ||
|
|
9b05a9c334 | ||
|
|
0f39ee9b34 | ||
|
|
9a0088c84e | ||
|
|
c533d48cf5 | ||
|
|
6a3ceb6bc0 | ||
|
|
5ad517ce83 |
@@ -1,6 +0,0 @@
|
||||
.git/
|
||||
.github/
|
||||
|
||||
# Ignore output directories
|
||||
output/
|
||||
junit-reports/
|
||||
2
.github/CODEOWNERS
vendored
2
.github/CODEOWNERS
vendored
@@ -1 +1 @@
|
||||
* @prowler-cloud/prowler-team
|
||||
* @prowler-cloud/prowler-oss
|
||||
|
||||
50
.github/ISSUE_TEMPLATE/bug_report.md
vendored
50
.github/ISSUE_TEMPLATE/bug_report.md
vendored
@@ -1,50 +0,0 @@
|
||||
---
|
||||
name: Bug report
|
||||
about: Create a report to help us improve
|
||||
title: "[Bug]: "
|
||||
labels: bug, status/needs-triage
|
||||
assignees: ''
|
||||
|
||||
---
|
||||
|
||||
<!--
|
||||
Please use this template to create your bug report. By providing as much info as possible you help us understand the issue, reproduce it and resolve it for you quicker. Therefore, take a couple of extra minutes to make sure you have provided all info needed.
|
||||
|
||||
PROTIP: record your screen and attach it as a gif to showcase the issue.
|
||||
|
||||
- How to record and attach gif: https://bit.ly/2Mi8T6K
|
||||
-->
|
||||
|
||||
**What happened?**
|
||||
A clear and concise description of what the bug is or what is not working as expected
|
||||
|
||||
|
||||
**How to reproduce it**
|
||||
Steps to reproduce the behavior:
|
||||
1. What command are you running?
|
||||
2. Environment you have, like single account, multi-account, organizations, etc.
|
||||
3. See error
|
||||
|
||||
|
||||
**Expected behavior**
|
||||
A clear and concise description of what you expected to happen.
|
||||
|
||||
|
||||
**Screenshots or Logs**
|
||||
If applicable, add screenshots to help explain your problem.
|
||||
Also, you can add logs (anonymize them first!). Here a command that may help to share a log
|
||||
`bash -x ./prowler -options > debug.log 2>&1` then attach here `debug.log`
|
||||
|
||||
|
||||
**From where are you running Prowler?**
|
||||
Please, complete the following information:
|
||||
- Resource: [e.g. EC2 instance, Fargate task, Docker container manually, EKS, Cloud9, CodeBuild, workstation, etc.)
|
||||
- OS: [e.g. Amazon Linux 2, Mac, Alpine, Windows, etc. ]
|
||||
- AWS-CLI Version [`aws --version`]:
|
||||
- Prowler Version [`./prowler -V`]:
|
||||
- Shell and version:
|
||||
- Others:
|
||||
|
||||
|
||||
**Additional context**
|
||||
Add any other context about the problem here.
|
||||
97
.github/ISSUE_TEMPLATE/bug_report.yml
vendored
Normal file
97
.github/ISSUE_TEMPLATE/bug_report.yml
vendored
Normal file
@@ -0,0 +1,97 @@
|
||||
name: 🐞 Bug Report
|
||||
description: Create a report to help us improve
|
||||
title: "[Bug]: "
|
||||
labels: ["bug", "status/needs-triage"]
|
||||
|
||||
body:
|
||||
- type: textarea
|
||||
id: reproduce
|
||||
attributes:
|
||||
label: Steps to Reproduce
|
||||
description: Steps to reproduce the behavior
|
||||
placeholder: |-
|
||||
1. What command are you running?
|
||||
2. Cloud provider you are launching
|
||||
3. Environment you have, like single account, multi-account, organizations, multi or single subscription, etc.
|
||||
4. See error
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: expected
|
||||
attributes:
|
||||
label: Expected behavior
|
||||
description: A clear and concise description of what you expected to happen.
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: actual
|
||||
attributes:
|
||||
label: Actual Result with Screenshots or Logs
|
||||
description: If applicable, add screenshots to help explain your problem. Also, you can add logs (anonymize them first!). Here a command that may help to share a log `prowler <your arguments> --log-level DEBUG --log-file $(date +%F)_debug.log` then attach here the log file.
|
||||
validations:
|
||||
required: true
|
||||
- type: dropdown
|
||||
id: type
|
||||
attributes:
|
||||
label: How did you install Prowler?
|
||||
options:
|
||||
- Cloning the repository from github.com (git clone)
|
||||
- From pip package (pip install prowler)
|
||||
- From brew (brew install prowler)
|
||||
- Docker (docker pull toniblyx/prowler)
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: environment
|
||||
attributes:
|
||||
label: Environment Resource
|
||||
description: From where are you running Prowler?
|
||||
placeholder: |-
|
||||
1. EC2 instance
|
||||
2. Fargate task
|
||||
3. Docker container locally
|
||||
4. EKS
|
||||
5. Cloud9
|
||||
6. CodeBuild
|
||||
7. Workstation
|
||||
8. Other(please specify)
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: os
|
||||
attributes:
|
||||
label: OS used
|
||||
description: Which OS are you using?
|
||||
placeholder: |-
|
||||
1. Amazon Linux 2
|
||||
2. MacOS
|
||||
3. Alpine Linux
|
||||
4. Windows
|
||||
5. Other(please specify)
|
||||
validations:
|
||||
required: true
|
||||
- type: input
|
||||
id: prowler-version
|
||||
attributes:
|
||||
label: Prowler version
|
||||
description: Which Prowler version are you using?
|
||||
placeholder: |-
|
||||
prowler --version
|
||||
validations:
|
||||
required: true
|
||||
- type: input
|
||||
id: pip-version
|
||||
attributes:
|
||||
label: Pip version
|
||||
description: Which pip version are you using?
|
||||
placeholder: |-
|
||||
pip --version
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: additional
|
||||
attributes:
|
||||
description: Additional context
|
||||
label: Context
|
||||
validations:
|
||||
required: false
|
||||
1
.github/ISSUE_TEMPLATE/config.yml
vendored
Normal file
1
.github/ISSUE_TEMPLATE/config.yml
vendored
Normal file
@@ -0,0 +1 @@
|
||||
blank_issues_enabled: false
|
||||
36
.github/ISSUE_TEMPLATE/feature-request.yml
vendored
Normal file
36
.github/ISSUE_TEMPLATE/feature-request.yml
vendored
Normal file
@@ -0,0 +1,36 @@
|
||||
name: 💡 Feature Request
|
||||
description: Suggest an idea for this project
|
||||
labels: ["enhancement", "status/needs-triage"]
|
||||
|
||||
|
||||
body:
|
||||
- type: textarea
|
||||
id: Problem
|
||||
attributes:
|
||||
label: New feature motivation
|
||||
description: Is your feature request related to a problem? Please describe
|
||||
placeholder: |-
|
||||
1. A clear and concise description of what the problem is. Ex. I'm always frustrated when
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: Solution
|
||||
attributes:
|
||||
label: Solution Proposed
|
||||
description: A clear and concise description of what you want to happen.
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: Alternatives
|
||||
attributes:
|
||||
label: Describe alternatives you've considered
|
||||
description: A clear and concise description of any alternative solutions or features you've considered.
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
id: Context
|
||||
attributes:
|
||||
label: Additional context
|
||||
description: Add any other context or screenshots about the feature request here.
|
||||
validations:
|
||||
required: false
|
||||
20
.github/ISSUE_TEMPLATE/feature_request.md
vendored
20
.github/ISSUE_TEMPLATE/feature_request.md
vendored
@@ -1,20 +0,0 @@
|
||||
---
|
||||
name: Feature request
|
||||
about: Suggest an idea for this project
|
||||
title: ''
|
||||
labels: enhancement, status/needs-triage
|
||||
assignees: ''
|
||||
|
||||
---
|
||||
|
||||
**Is your feature request related to a problem? Please describe.**
|
||||
A clear and concise description of what the problem is. Ex. I'm always frustrated when [...]
|
||||
|
||||
**Describe the solution you'd like**
|
||||
A clear and concise description of what you want to happen.
|
||||
|
||||
**Describe alternatives you've considered**
|
||||
A clear and concise description of any alternative solutions or features you've considered.
|
||||
|
||||
**Additional context**
|
||||
Add any other context or screenshots about the feature request here.
|
||||
15
.github/dependabot.yml
vendored
Normal file
15
.github/dependabot.yml
vendored
Normal file
@@ -0,0 +1,15 @@
|
||||
# To get started with Dependabot version updates, you'll need to specify which
|
||||
# package ecosystems to update and where the package manifests are located.
|
||||
# Please see the documentation for all configuration options:
|
||||
# https://docs.github.com/github/administering-a-repository/configuration-options-for-dependency-updates
|
||||
|
||||
version: 2
|
||||
updates:
|
||||
- package-ecosystem: "pip" # See documentation for possible values
|
||||
directory: "/" # Location of package manifests
|
||||
schedule:
|
||||
interval: "weekly"
|
||||
target-branch: master
|
||||
labels:
|
||||
- "dependencies"
|
||||
- "pip"
|
||||
2
.github/pull_request_template.md
vendored
2
.github/pull_request_template.md
vendored
@@ -1,4 +1,4 @@
|
||||
### Context
|
||||
### Context
|
||||
|
||||
Please include relevant motivation and context for this PR.
|
||||
|
||||
|
||||
227
.github/workflows/build-lint-push-containers.yml
vendored
227
.github/workflows/build-lint-push-containers.yml
vendored
@@ -3,196 +3,115 @@ name: build-lint-push-containers
|
||||
on:
|
||||
push:
|
||||
branches:
|
||||
- 'master'
|
||||
- "master"
|
||||
paths-ignore:
|
||||
- '.github/**'
|
||||
- 'README.md'
|
||||
|
||||
- ".github/**"
|
||||
- "README.md"
|
||||
- "docs/**"
|
||||
|
||||
release:
|
||||
types: [published]
|
||||
|
||||
env:
|
||||
AWS_REGION_STG: eu-west-1
|
||||
AWS_REGION_PRO: us-east-1
|
||||
AWS_REGION_PLATFORM: eu-west-1
|
||||
AWS_REGION: us-east-1
|
||||
IMAGE_NAME: prowler
|
||||
LATEST_TAG: latest
|
||||
STABLE_TAG: stable
|
||||
TEMPORARY_TAG: temporary
|
||||
DOCKERFILE_PATH: util/Dockerfile
|
||||
DOCKERFILE_PATH: ./Dockerfile
|
||||
PYTHON_VERSION: 3.9
|
||||
|
||||
jobs:
|
||||
# Lint Dockerfile using Hadolint
|
||||
# dockerfile-linter:
|
||||
# runs-on: ubuntu-latest
|
||||
# steps:
|
||||
# -
|
||||
# name: Checkout
|
||||
# uses: actions/checkout@v3
|
||||
# -
|
||||
# name: Install Hadolint
|
||||
# run: |
|
||||
# VERSION=$(curl --silent "https://api.github.com/repos/hadolint/hadolint/releases/latest" | \
|
||||
# grep '"tag_name":' | \
|
||||
# sed -E 's/.*"v([^"]+)".*/\1/' \
|
||||
# ) && curl -L -o /tmp/hadolint https://github.com/hadolint/hadolint/releases/download/v${VERSION}/hadolint-Linux-x86_64 \
|
||||
# && chmod +x /tmp/hadolint
|
||||
# -
|
||||
# name: Run Hadolint
|
||||
# run: |
|
||||
# /tmp/hadolint util/Dockerfile
|
||||
|
||||
# Build Prowler OSS container
|
||||
container-build:
|
||||
container-build-push:
|
||||
# needs: dockerfile-linter
|
||||
runs-on: ubuntu-latest
|
||||
env:
|
||||
POETRY_VIRTUALENVS_CREATE: "false"
|
||||
steps:
|
||||
-
|
||||
name: Checkout
|
||||
- name: Checkout
|
||||
uses: actions/checkout@v3
|
||||
-
|
||||
name: Set up Docker Buildx
|
||||
uses: docker/setup-buildx-action@v2
|
||||
-
|
||||
name: Build
|
||||
uses: docker/build-push-action@v2
|
||||
with:
|
||||
# Without pushing to registries
|
||||
push: false
|
||||
tags: ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }}
|
||||
file: ${{ env.DOCKERFILE_PATH }}
|
||||
outputs: type=docker,dest=/tmp/${{ env.IMAGE_NAME }}.tar
|
||||
-
|
||||
name: Share image between jobs
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: ${{ env.IMAGE_NAME }}.tar
|
||||
path: /tmp/${{ env.IMAGE_NAME }}.tar
|
||||
|
||||
# Lint Prowler OSS container using Dockle
|
||||
# container-linter:
|
||||
# needs: container-build
|
||||
# runs-on: ubuntu-latest
|
||||
# steps:
|
||||
# -
|
||||
# name: Get container image from shared
|
||||
# uses: actions/download-artifact@v2
|
||||
# with:
|
||||
# name: ${{ env.IMAGE_NAME }}.tar
|
||||
# path: /tmp
|
||||
# -
|
||||
# name: Load Docker image
|
||||
# run: |
|
||||
# docker load --input /tmp/${{ env.IMAGE_NAME }}.tar
|
||||
# docker image ls -a
|
||||
# -
|
||||
# name: Install Dockle
|
||||
# run: |
|
||||
# VERSION=$(curl --silent "https://api.github.com/repos/goodwithtech/dockle/releases/latest" | \
|
||||
# grep '"tag_name":' | \
|
||||
# sed -E 's/.*"v([^"]+)".*/\1/' \
|
||||
# ) && curl -L -o dockle.deb https://github.com/goodwithtech/dockle/releases/download/v${VERSION}/dockle_${VERSION}_Linux-64bit.deb \
|
||||
# && sudo dpkg -i dockle.deb && rm dockle.deb
|
||||
# -
|
||||
# name: Run Dockle
|
||||
# run: dockle ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }}
|
||||
|
||||
# Push Prowler OSS container to registries
|
||||
container-push:
|
||||
# needs: container-linter
|
||||
needs: container-build
|
||||
runs-on: ubuntu-latest
|
||||
permissions:
|
||||
id-token: write
|
||||
contents: read # This is required for actions/checkout
|
||||
steps:
|
||||
-
|
||||
name: Get container image from shared
|
||||
uses: actions/download-artifact@v2
|
||||
- name: Setup python (release)
|
||||
if: github.event_name == 'release'
|
||||
uses: actions/setup-python@v2
|
||||
with:
|
||||
name: ${{ env.IMAGE_NAME }}.tar
|
||||
path: /tmp
|
||||
-
|
||||
name: Load Docker image
|
||||
python-version: ${{ env.PYTHON_VERSION }}
|
||||
|
||||
- name: Install dependencies (release)
|
||||
if: github.event_name == 'release'
|
||||
run: |
|
||||
docker load --input /tmp/${{ env.IMAGE_NAME }}.tar
|
||||
docker image ls -a
|
||||
-
|
||||
name: Login to DockerHub
|
||||
pipx install poetry
|
||||
pipx inject poetry poetry-bumpversion
|
||||
|
||||
- name: Update Prowler version (release)
|
||||
if: github.event_name == 'release'
|
||||
run: |
|
||||
poetry version ${{ github.event.release.tag_name }}
|
||||
|
||||
- name: Login to DockerHub
|
||||
uses: docker/login-action@v2
|
||||
with:
|
||||
username: ${{ secrets.DOCKERHUB_USERNAME }}
|
||||
password: ${{ secrets.DOCKERHUB_TOKEN }}
|
||||
-
|
||||
name: Login to Public ECR
|
||||
|
||||
- name: Login to Public ECR
|
||||
uses: docker/login-action@v2
|
||||
with:
|
||||
registry: public.ecr.aws
|
||||
username: ${{ secrets.PUBLIC_ECR_AWS_ACCESS_KEY_ID }}
|
||||
password: ${{ secrets.PUBLIC_ECR_AWS_SECRET_ACCESS_KEY }}
|
||||
env:
|
||||
AWS_REGION: ${{ env.AWS_REGION_PRO }}
|
||||
-
|
||||
name: Configure AWS Credentials -- STG
|
||||
AWS_REGION: ${{ env.AWS_REGION }}
|
||||
|
||||
- name: Set up Docker Buildx
|
||||
uses: docker/setup-buildx-action@v2
|
||||
|
||||
- name: Build container image (latest)
|
||||
if: github.event_name == 'push'
|
||||
uses: aws-actions/configure-aws-credentials@v1
|
||||
uses: docker/build-push-action@v2
|
||||
with:
|
||||
aws-region: ${{ env.AWS_REGION_STG }}
|
||||
role-to-assume: ${{ secrets.STG_IAM_ROLE_ARN }}
|
||||
role-session-name: build-lint-containers-stg
|
||||
-
|
||||
name: Login to ECR -- STG
|
||||
if: github.event_name == 'push'
|
||||
uses: docker/login-action@v2
|
||||
with:
|
||||
registry: ${{ secrets.STG_ECR }}
|
||||
-
|
||||
name: Configure AWS Credentials -- PRO
|
||||
push: true
|
||||
tags: |
|
||||
${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.LATEST_TAG }}
|
||||
${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.LATEST_TAG }}
|
||||
file: ${{ env.DOCKERFILE_PATH }}
|
||||
cache-from: type=gha
|
||||
cache-to: type=gha,mode=max
|
||||
|
||||
- name: Build container image (release)
|
||||
if: github.event_name == 'release'
|
||||
uses: aws-actions/configure-aws-credentials@v1
|
||||
uses: docker/build-push-action@v2
|
||||
with:
|
||||
aws-region: ${{ env.AWS_REGION_PRO }}
|
||||
role-to-assume: ${{ secrets.PRO_IAM_ROLE_ARN }}
|
||||
role-session-name: build-lint-containers-pro
|
||||
-
|
||||
name: Login to ECR -- PRO
|
||||
if: github.event_name == 'release'
|
||||
uses: docker/login-action@v2
|
||||
with:
|
||||
registry: ${{ secrets.PRO_ECR }}
|
||||
-
|
||||
# Push to master branch - push "latest" tag
|
||||
name: Tag (latest)
|
||||
# Use local context to get changes
|
||||
# https://github.com/docker/build-push-action#path-context
|
||||
context: .
|
||||
push: true
|
||||
tags: |
|
||||
${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ github.event.release.tag_name }}
|
||||
${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.STABLE_TAG }}
|
||||
${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ github.event.release.tag_name }}
|
||||
${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.STABLE_TAG }}
|
||||
file: ${{ env.DOCKERFILE_PATH }}
|
||||
cache-from: type=gha
|
||||
cache-to: type=gha,mode=max
|
||||
|
||||
dispatch-action:
|
||||
needs: container-build-push
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- name: Get latest commit info
|
||||
if: github.event_name == 'push'
|
||||
run: |
|
||||
docker tag ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }} ${{ secrets.STG_ECR }}/${{ secrets.STG_ECR_REPOSITORY }}:${{ env.LATEST_TAG }}
|
||||
docker tag ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }} ${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.LATEST_TAG }}
|
||||
docker tag ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }} ${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.LATEST_TAG }}
|
||||
-
|
||||
# Push to master branch - push "latest" tag
|
||||
name: Push (latest)
|
||||
LATEST_COMMIT_HASH=$(echo ${{ github.event.after }} | cut -b -7)
|
||||
echo "LATEST_COMMIT_HASH=${LATEST_COMMIT_HASH}" >> $GITHUB_ENV
|
||||
- name: Dispatch event for latest
|
||||
if: github.event_name == 'push'
|
||||
run: |
|
||||
docker push ${{ secrets.STG_ECR }}/${{ secrets.STG_ECR_REPOSITORY }}:${{ env.LATEST_TAG }}
|
||||
docker push ${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.LATEST_TAG }}
|
||||
docker push ${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ env.LATEST_TAG }}
|
||||
-
|
||||
# Push the new release
|
||||
name: Tag (release)
|
||||
curl https://api.github.com/repos/${{ secrets.DISPATCH_OWNER }}/${{ secrets.DISPATCH_REPO }}/dispatches -H "Accept: application/vnd.github+json" -H "Authorization: Bearer ${{ secrets.ACCESS_TOKEN }}" -H "X-GitHub-Api-Version: 2022-11-28" --data '{"event_type":"dispatch","client_payload":{"version":"latest", "tag": "${{ env.LATEST_COMMIT_HASH }}"}}'
|
||||
- name: Dispatch event for release
|
||||
if: github.event_name == 'release'
|
||||
run: |
|
||||
docker tag ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }} ${{ secrets.PRO_ECR }}/${{ secrets.PRO_ECR }}:${{ github.event.release.tag_name }}
|
||||
docker tag ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }} ${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ github.event.release.tag_name }}
|
||||
docker tag ${{ env.IMAGE_NAME }}:${{ env.TEMPORARY_TAG }} ${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ github.event.release.tag_name }}
|
||||
-
|
||||
# Push the new release
|
||||
name: Push (release)
|
||||
if: github.event_name == 'release'
|
||||
run: |
|
||||
docker push ${{ secrets.PRO_ECR }}/${{ secrets.PRO_ECR }}:${{ github.event.release.tag_name }}
|
||||
docker push ${{ secrets.DOCKER_HUB_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ github.event.release.tag_name }}
|
||||
docker push ${{ secrets.PUBLIC_ECR_REPOSITORY }}/${{ env.IMAGE_NAME }}:${{ github.event.release.tag_name }}
|
||||
-
|
||||
name: Delete artifacts
|
||||
if: always()
|
||||
uses: geekyeggo/delete-artifact@v1
|
||||
with:
|
||||
name: ${{ env.IMAGE_NAME }}.tar
|
||||
curl https://api.github.com/repos/${{ secrets.DISPATCH_OWNER }}/${{ secrets.DISPATCH_REPO }}/dispatches -H "Accept: application/vnd.github+json" -H "Authorization: Bearer ${{ secrets.ACCESS_TOKEN }}" -H "X-GitHub-Api-Version: 2022-11-28" --data '{"event_type":"dispatch","client_payload":{"version":"release", "tag":"${{ github.event.release.tag_name }}"}}'
|
||||
|
||||
57
.github/workflows/codeql.yml
vendored
Normal file
57
.github/workflows/codeql.yml
vendored
Normal file
@@ -0,0 +1,57 @@
|
||||
# For most projects, this workflow file will not need changing; you simply need
|
||||
# to commit it to your repository.
|
||||
#
|
||||
# You may wish to alter this file to override the set of languages analyzed,
|
||||
# or to provide custom queries or build logic.
|
||||
#
|
||||
# ******** NOTE ********
|
||||
# We have attempted to detect the languages in your repository. Please check
|
||||
# the `language` matrix defined below to confirm you have the correct set of
|
||||
# supported CodeQL languages.
|
||||
#
|
||||
name: "CodeQL"
|
||||
|
||||
on:
|
||||
push:
|
||||
branches: [ "master", prowler-2, prowler-3.0-dev ]
|
||||
pull_request:
|
||||
# The branches below must be a subset of the branches above
|
||||
branches: [ "master" ]
|
||||
schedule:
|
||||
- cron: '00 12 * * *'
|
||||
|
||||
jobs:
|
||||
analyze:
|
||||
name: Analyze
|
||||
runs-on: ubuntu-latest
|
||||
permissions:
|
||||
actions: read
|
||||
contents: read
|
||||
security-events: write
|
||||
|
||||
strategy:
|
||||
fail-fast: false
|
||||
matrix:
|
||||
language: [ 'python' ]
|
||||
# Learn more about CodeQL language support at https://aka.ms/codeql-docs/language-support
|
||||
|
||||
steps:
|
||||
- name: Checkout repository
|
||||
uses: actions/checkout@v3
|
||||
|
||||
# Initializes the CodeQL tools for scanning.
|
||||
- name: Initialize CodeQL
|
||||
uses: github/codeql-action/init@v2
|
||||
with:
|
||||
languages: ${{ matrix.language }}
|
||||
# If you wish to specify custom queries, you can do so here or in a config file.
|
||||
# By default, queries listed here will override any specified in a config file.
|
||||
# Prefix the list here with "+" to use these queries and those in the config file.
|
||||
|
||||
# Details on CodeQL's query packs refer to : https://docs.github.com/en/code-security/code-scanning/automatically-scanning-your-code-for-vulnerabilities-and-errors/configuring-code-scanning#using-queries-in-ql-packs
|
||||
# queries: security-extended,security-and-quality
|
||||
|
||||
- name: Perform CodeQL Analysis
|
||||
uses: github/codeql-action/analyze@v2
|
||||
with:
|
||||
category: "/language:${{matrix.language}}"
|
||||
64
.github/workflows/pull-request.yml
vendored
Normal file
64
.github/workflows/pull-request.yml
vendored
Normal file
@@ -0,0 +1,64 @@
|
||||
name: pr-lint-test
|
||||
|
||||
on:
|
||||
push:
|
||||
branches:
|
||||
- "master"
|
||||
pull_request:
|
||||
branches:
|
||||
- "master"
|
||||
|
||||
jobs:
|
||||
build:
|
||||
runs-on: ubuntu-latest
|
||||
strategy:
|
||||
matrix:
|
||||
python-version: ["3.9"]
|
||||
|
||||
steps:
|
||||
- uses: actions/checkout@v3
|
||||
- name: Install poetry
|
||||
run: |
|
||||
python -m pip install --upgrade pip
|
||||
pipx install poetry
|
||||
- name: Set up Python ${{ matrix.python-version }}
|
||||
uses: actions/setup-python@v4
|
||||
with:
|
||||
python-version: ${{ matrix.python-version }}
|
||||
cache: 'poetry'
|
||||
- name: Install dependencies
|
||||
run: |
|
||||
poetry install
|
||||
poetry run pip list
|
||||
VERSION=$(curl --silent "https://api.github.com/repos/hadolint/hadolint/releases/latest" | \
|
||||
grep '"tag_name":' | \
|
||||
sed -E 's/.*"v([^"]+)".*/\1/' \
|
||||
) && curl -L -o /tmp/hadolint "https://github.com/hadolint/hadolint/releases/download/v${VERSION}/hadolint-Linux-x86_64" \
|
||||
&& chmod +x /tmp/hadolint
|
||||
- name: Poetry check
|
||||
run: |
|
||||
poetry lock --check
|
||||
- name: Lint with flake8
|
||||
run: |
|
||||
poetry run flake8 . --ignore=E266,W503,E203,E501,W605,E128 --exclude contrib
|
||||
- name: Checking format with black
|
||||
run: |
|
||||
poetry run black --check .
|
||||
- name: Lint with pylint
|
||||
run: |
|
||||
poetry run pylint --disable=W,C,R,E -j 0 -rn -sn prowler/
|
||||
- name: Bandit
|
||||
run: |
|
||||
poetry run bandit -q -lll -x '*_test.py,./contrib/' -r .
|
||||
- name: Safety
|
||||
run: |
|
||||
poetry run safety check
|
||||
- name: Vulture
|
||||
run: |
|
||||
poetry run vulture --exclude "contrib" --min-confidence 100 .
|
||||
- name: Hadolint
|
||||
run: |
|
||||
/tmp/hadolint Dockerfile --ignore=DL3013
|
||||
- name: Test with pytest
|
||||
run: |
|
||||
poetry run pytest tests -n auto
|
||||
77
.github/workflows/pypi-release.yml
vendored
Normal file
77
.github/workflows/pypi-release.yml
vendored
Normal file
@@ -0,0 +1,77 @@
|
||||
name: pypi-release
|
||||
|
||||
on:
|
||||
release:
|
||||
types: [published]
|
||||
|
||||
env:
|
||||
RELEASE_TAG: ${{ github.event.release.tag_name }}
|
||||
|
||||
jobs:
|
||||
release-prowler-job:
|
||||
runs-on: ubuntu-latest
|
||||
env:
|
||||
POETRY_VIRTUALENVS_CREATE: "false"
|
||||
name: Release Prowler to PyPI
|
||||
steps:
|
||||
# Checks-out your repository under $GITHUB_WORKSPACE, so your job can access it
|
||||
- uses: actions/checkout@v3
|
||||
|
||||
- name: Install dependencies
|
||||
run: |
|
||||
pipx install poetry
|
||||
pipx inject poetry poetry-bumpversion
|
||||
- name: setup python
|
||||
uses: actions/setup-python@v4
|
||||
with:
|
||||
python-version: 3.9
|
||||
cache: 'poetry'
|
||||
- name: Change version and Build package
|
||||
run: |
|
||||
poetry version ${{ env.RELEASE_TAG }}
|
||||
git config user.name "github-actions"
|
||||
git config user.email "<noreply@github.com>"
|
||||
git add prowler/config/config.py pyproject.toml
|
||||
git commit -m "chore(release): ${{ env.RELEASE_TAG }}" --no-verify
|
||||
git tag -fa ${{ env.RELEASE_TAG }} -m "chore(release): ${{ env.RELEASE_TAG }}"
|
||||
git push -f origin ${{ env.RELEASE_TAG }}
|
||||
poetry build
|
||||
- name: Publish prowler package to PyPI
|
||||
run: |
|
||||
poetry config pypi-token.pypi ${{ secrets.PYPI_API_TOKEN }}
|
||||
poetry publish
|
||||
# Create pull request with new version
|
||||
- name: Create Pull Request
|
||||
uses: peter-evans/create-pull-request@v4
|
||||
with:
|
||||
token: ${{ secrets.PROWLER_ACCESS_TOKEN }}
|
||||
commit-message: "chore(release): update Prowler Version to ${{ env.RELEASE_TAG }}."
|
||||
branch: release-${{ env.RELEASE_TAG }}
|
||||
labels: "status/waiting-for-revision, severity/low"
|
||||
title: "chore(release): update Prowler Version to ${{ env.RELEASE_TAG }}"
|
||||
body: |
|
||||
### Description
|
||||
|
||||
This PR updates Prowler Version to ${{ env.RELEASE_TAG }}.
|
||||
|
||||
### License
|
||||
|
||||
By submitting this pull request, I confirm that my contribution is made under the terms of the Apache 2.0 license.
|
||||
- name: Replicate PyPi Package
|
||||
run: |
|
||||
rm -rf ./dist && rm -rf ./build && rm -rf prowler.egg-info
|
||||
pip install toml
|
||||
python util/replicate_pypi_package.py
|
||||
poetry build
|
||||
- name: Publish prowler-cloud package to PyPI
|
||||
run: |
|
||||
poetry config pypi-token.pypi ${{ secrets.PYPI_API_TOKEN }}
|
||||
poetry publish
|
||||
# Create pull request to github.com/Homebrew/homebrew-core to update prowler formula
|
||||
- name: Bump Homebrew formula
|
||||
uses: mislav/bump-homebrew-formula-action@v2
|
||||
with:
|
||||
formula-name: prowler
|
||||
base-branch: release-${{ env.RELEASE_TAG }}
|
||||
env:
|
||||
COMMITTER_TOKEN: ${{ secrets.PROWLER_ACCESS_TOKEN }}
|
||||
67
.github/workflows/refresh_aws_services_regions.yml
vendored
Normal file
67
.github/workflows/refresh_aws_services_regions.yml
vendored
Normal file
@@ -0,0 +1,67 @@
|
||||
# This is a basic workflow to help you get started with Actions
|
||||
|
||||
name: Refresh regions of AWS services
|
||||
|
||||
on:
|
||||
schedule:
|
||||
- cron: "0 9 * * *" #runs at 09:00 UTC everyday
|
||||
|
||||
env:
|
||||
GITHUB_BRANCH: "master"
|
||||
AWS_REGION_DEV: us-east-1
|
||||
|
||||
# A workflow run is made up of one or more jobs that can run sequentially or in parallel
|
||||
jobs:
|
||||
# This workflow contains a single job called "build"
|
||||
build:
|
||||
# The type of runner that the job will run on
|
||||
runs-on: ubuntu-latest
|
||||
permissions:
|
||||
id-token: write
|
||||
pull-requests: write
|
||||
contents: write
|
||||
# Steps represent a sequence of tasks that will be executed as part of the job
|
||||
steps:
|
||||
# Checks-out your repository under $GITHUB_WORKSPACE, so your job can access it
|
||||
- uses: actions/checkout@v3
|
||||
with:
|
||||
ref: ${{ env.GITHUB_BRANCH }}
|
||||
|
||||
- name: setup python
|
||||
uses: actions/setup-python@v2
|
||||
with:
|
||||
python-version: 3.9 #install the python needed
|
||||
|
||||
- name: Install dependencies
|
||||
run: |
|
||||
python -m pip install --upgrade pip
|
||||
pip install boto3
|
||||
|
||||
- name: Configure AWS Credentials -- DEV
|
||||
uses: aws-actions/configure-aws-credentials@v1
|
||||
with:
|
||||
aws-region: ${{ env.AWS_REGION_DEV }}
|
||||
role-to-assume: ${{ secrets.DEV_IAM_ROLE_ARN }}
|
||||
role-session-name: refresh-AWS-regions-dev
|
||||
|
||||
# Runs a single command using the runners shell
|
||||
- name: Run a one-line script
|
||||
run: python3 util/update_aws_services_regions.py
|
||||
|
||||
# Create pull request
|
||||
- name: Create Pull Request
|
||||
uses: peter-evans/create-pull-request@v4
|
||||
with:
|
||||
token: ${{ secrets.PROWLER_ACCESS_TOKEN }}
|
||||
commit-message: "feat(regions_update): Update regions for AWS services."
|
||||
branch: "aws-services-regions-updated-${{ github.sha }}"
|
||||
labels: "status/waiting-for-revision, severity/low"
|
||||
title: "chore(regions_update): Changes in regions for AWS services."
|
||||
body: |
|
||||
### Description
|
||||
|
||||
This PR updates the regions for AWS services.
|
||||
|
||||
### License
|
||||
|
||||
By submitting this pull request, I confirm that my contribution is made under the terms of the Apache 2.0 license.
|
||||
16
.gitignore
vendored
16
.gitignore
vendored
@@ -5,6 +5,13 @@
|
||||
[._]ss[a-gi-z]
|
||||
[._]sw[a-p]
|
||||
|
||||
# Python code
|
||||
__pycache__
|
||||
venv/
|
||||
build/
|
||||
dist/
|
||||
*.egg-info/
|
||||
|
||||
# Session
|
||||
Session.vim
|
||||
Sessionx.vim
|
||||
@@ -33,8 +40,9 @@ junit-reports/
|
||||
# VSCode files
|
||||
.vscode/
|
||||
|
||||
terraform-kickstarter/.terraform.lock.hcl
|
||||
# Terraform
|
||||
.terraform*
|
||||
*.tfstate
|
||||
|
||||
terraform-kickstarter/.terraform/providers/registry.terraform.io/hashicorp/aws/3.56.0/darwin_amd64/terraform-provider-aws_v3.56.0_x5
|
||||
|
||||
terraform-kickstarter/terraform.tfstate
|
||||
# .env
|
||||
.env*
|
||||
|
||||
@@ -1,13 +1,99 @@
|
||||
repos:
|
||||
## GENERAL
|
||||
- repo: https://github.com/pre-commit/pre-commit-hooks
|
||||
rev: v3.3.0
|
||||
rev: v4.4.0
|
||||
hooks:
|
||||
- id: check-merge-conflict
|
||||
- id: check-yaml
|
||||
args: ['--unsafe']
|
||||
args: ["--unsafe"]
|
||||
- id: check-json
|
||||
- id: end-of-file-fixer
|
||||
- id: trailing-whitespace
|
||||
- id: no-commit-to-branch
|
||||
- id: pretty-format-json
|
||||
args: ['--autofix']
|
||||
args: ["--autofix", --no-sort-keys, --no-ensure-ascii]
|
||||
|
||||
## TOML
|
||||
- repo: https://github.com/macisamuele/language-formatters-pre-commit-hooks
|
||||
rev: v2.7.0
|
||||
hooks:
|
||||
- id: pretty-format-toml
|
||||
args: [--autofix]
|
||||
files: pyproject.toml
|
||||
|
||||
## BASH
|
||||
- repo: https://github.com/koalaman/shellcheck-precommit
|
||||
rev: v0.9.0
|
||||
hooks:
|
||||
- id: shellcheck
|
||||
## PYTHON
|
||||
- repo: https://github.com/myint/autoflake
|
||||
rev: v2.0.1
|
||||
hooks:
|
||||
- id: autoflake
|
||||
args:
|
||||
[
|
||||
"--in-place",
|
||||
"--remove-all-unused-imports",
|
||||
"--remove-unused-variable",
|
||||
]
|
||||
|
||||
- repo: https://github.com/timothycrosley/isort
|
||||
rev: 5.12.0
|
||||
hooks:
|
||||
- id: isort
|
||||
args: ["--profile", "black"]
|
||||
|
||||
- repo: https://github.com/psf/black
|
||||
rev: 23.1.0
|
||||
hooks:
|
||||
- id: black
|
||||
|
||||
- repo: https://github.com/pycqa/flake8
|
||||
rev: 6.0.0
|
||||
hooks:
|
||||
- id: flake8
|
||||
exclude: contrib
|
||||
args: ["--ignore=E266,W503,E203,E501,W605"]
|
||||
|
||||
- repo: https://github.com/python-poetry/poetry
|
||||
rev: 1.4.0 # add version here
|
||||
hooks:
|
||||
- id: poetry-check
|
||||
- id: poetry-lock
|
||||
|
||||
- repo: https://github.com/hadolint/hadolint
|
||||
rev: v2.12.1-beta
|
||||
hooks:
|
||||
- id: hadolint
|
||||
args: ["--ignore=DL3013"]
|
||||
|
||||
- repo: local
|
||||
hooks:
|
||||
- id: pylint
|
||||
name: pylint
|
||||
entry: bash -c 'pylint --disable=W,C,R,E -j 0 -rn -sn prowler/'
|
||||
language: system
|
||||
|
||||
- id: pytest-check
|
||||
name: pytest-check
|
||||
entry: bash -c 'pytest tests -n auto'
|
||||
language: system
|
||||
|
||||
- id: bandit
|
||||
name: bandit
|
||||
description: "Bandit is a tool for finding common security issues in Python code"
|
||||
entry: bash -c 'bandit -q -lll -x '*_test.py,./contrib/' -r .'
|
||||
language: system
|
||||
|
||||
- id: safety
|
||||
name: safety
|
||||
description: "Safety is a tool that checks your installed dependencies for known security vulnerabilities"
|
||||
entry: bash -c 'safety check'
|
||||
language: system
|
||||
|
||||
- id: vulture
|
||||
name: vulture
|
||||
description: "Vulture finds unused code in Python programs."
|
||||
entry: bash -c 'vulture --exclude "contrib" --min-confidence 100 .'
|
||||
language: system
|
||||
|
||||
23
.readthedocs.yaml
Normal file
23
.readthedocs.yaml
Normal file
@@ -0,0 +1,23 @@
|
||||
# .readthedocs.yaml
|
||||
# Read the Docs configuration file
|
||||
# See https://docs.readthedocs.io/en/stable/config-file/v2.html for details
|
||||
|
||||
# Required
|
||||
version: 2
|
||||
|
||||
build:
|
||||
os: "ubuntu-22.04"
|
||||
tools:
|
||||
python: "3.9"
|
||||
jobs:
|
||||
post_create_environment:
|
||||
# Install poetry
|
||||
# https://python-poetry.org/docs/#installing-manually
|
||||
- pip install poetry
|
||||
# Tell poetry to not use a virtual environment
|
||||
- poetry config virtualenvs.create false
|
||||
post_install:
|
||||
- poetry install -E docs
|
||||
|
||||
mkdocs:
|
||||
configuration: mkdocs.yml
|
||||
33
Dockerfile
Normal file
33
Dockerfile
Normal file
@@ -0,0 +1,33 @@
|
||||
FROM python:3.9-alpine
|
||||
|
||||
LABEL maintainer="https://github.com/prowler-cloud/prowler"
|
||||
|
||||
# Update system dependencies
|
||||
RUN apk --no-cache upgrade
|
||||
|
||||
# Create nonroot user
|
||||
RUN mkdir -p /home/prowler && \
|
||||
echo 'prowler:x:1000:1000:prowler:/home/prowler:' > /etc/passwd && \
|
||||
echo 'prowler:x:1000:' > /etc/group && \
|
||||
chown -R prowler:prowler /home/prowler
|
||||
USER prowler
|
||||
|
||||
# Copy necessary files
|
||||
WORKDIR /home/prowler
|
||||
COPY prowler/ /home/prowler/prowler/
|
||||
COPY pyproject.toml /home/prowler
|
||||
COPY README.md /home/prowler
|
||||
|
||||
# Install dependencies
|
||||
ENV HOME='/home/prowler'
|
||||
ENV PATH="$HOME/.local/bin:$PATH"
|
||||
#hadolint ignore=DL3013
|
||||
RUN pip install --no-cache-dir --upgrade pip && \
|
||||
pip install --no-cache-dir .
|
||||
|
||||
# Remove Prowler directory and build files
|
||||
USER 0
|
||||
RUN rm -rf /home/prowler/prowler /home/prowler/pyproject.toml /home/prowler/README.md /home/prowler/build /home/prowler/prowler.egg-info
|
||||
|
||||
USER prowler
|
||||
ENTRYPOINT ["prowler"]
|
||||
2
LICENSE
2
LICENSE
@@ -198,4 +198,4 @@ Copyright 2018 Netflix, Inc.
|
||||
distributed under the License is distributed on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
See the License for the specific language governing permissions and
|
||||
limitations under the License.
|
||||
limitations under the License.
|
||||
|
||||
@@ -1,5 +0,0 @@
|
||||
```
|
||||
./prowler -l # to see all available checks and their groups.
|
||||
./prowler -L # to see all available groups only.
|
||||
./prowler -l -g groupname # to see checks in a particular group
|
||||
```
|
||||
40
Makefile
Normal file
40
Makefile
Normal file
@@ -0,0 +1,40 @@
|
||||
.DEFAULT_GOAL:=help
|
||||
|
||||
##@ Testing
|
||||
test: ## Test with pytest
|
||||
pytest -n auto -vvv -s -x
|
||||
|
||||
coverage: ## Show Test Coverage
|
||||
coverage run --skip-covered -m pytest -v && \
|
||||
coverage report -m && \
|
||||
rm -rf .coverage
|
||||
|
||||
##@ Linting
|
||||
format: ## Format Code
|
||||
@echo "Running black..."
|
||||
black .
|
||||
|
||||
lint: ## Lint Code
|
||||
@echo "Running flake8..."
|
||||
flake8 . --ignore=E266,W503,E203,E501,W605,E128 --exclude contrib
|
||||
@echo "Running black... "
|
||||
black --check .
|
||||
@echo "Running pylint..."
|
||||
pylint --disable=W,C,R,E -j 0 providers lib util config
|
||||
|
||||
##@ PyPI
|
||||
pypi-clean: ## Delete the distribution files
|
||||
rm -rf ./dist && rm -rf ./build && rm -rf prowler.egg-info
|
||||
|
||||
pypi-build: ## Build package
|
||||
$(MAKE) pypi-clean && \
|
||||
poetry build
|
||||
|
||||
pypi-upload: ## Upload package
|
||||
python3 -m twine upload --repository pypi dist/*
|
||||
|
||||
|
||||
##@ Help
|
||||
help: ## Show this help.
|
||||
@echo "Prowler Makefile"
|
||||
@awk 'BEGIN {FS = ":.*##"; printf "\nUsage:\n make \033[36m<target>\033[0m\n"} /^[a-zA-Z_-]+:.*?##/ { printf " \033[36m%-15s\033[0m %s\n", $$1, $$2 } /^##@/ { printf "\n\033[1m%s\033[0m\n", substr($$0, 5) } ' $(MAKEFILE_LIST)
|
||||
13
Pipfile
13
Pipfile
@@ -1,13 +0,0 @@
|
||||
[[source]]
|
||||
name = "pypi"
|
||||
url = "https://pypi.org/simple"
|
||||
verify_ssl = true
|
||||
|
||||
[dev-packages]
|
||||
|
||||
[packages]
|
||||
boto3 = ">=1.9.188"
|
||||
detect-secrets = "==1.0.3"
|
||||
|
||||
[requires]
|
||||
python_version = "3.7"
|
||||
851
README.md
851
README.md
@@ -1,782 +1,251 @@
|
||||
<p align="center">
|
||||
<img align="center" src="docs/images/prowler-pro-dark.png#gh-dark-mode-only" width="150" height="36">
|
||||
<img align="center" src="docs/images/prowler-pro-light.png#gh-light-mode-only" width="15%" height="15%">
|
||||
<img align="center" src="https://github.com/prowler-cloud/prowler/blob/62c1ce73bbcdd6b9e5ba03dfcae26dfd165defd9/docs/img/prowler-pro-dark.png?raw=True#gh-dark-mode-only" width="150" height="36">
|
||||
<img align="center" src="https://github.com/prowler-cloud/prowler/blob/62c1ce73bbcdd6b9e5ba03dfcae26dfd165defd9/docs/img/prowler-pro-light.png?raw=True#gh-light-mode-only" width="15%" height="15%">
|
||||
</p>
|
||||
<p align="center">
|
||||
<b><i>   Explore the Pro version of Prowler at <a href="https://prowler.pro">prowler.pro</a></i></b>
|
||||
<b><i>See all the things you and your team can do with ProwlerPro at <a href="https://prowler.pro">prowler.pro</a></i></b>
|
||||
</p>
|
||||
<hr>
|
||||
<p align="center">
|
||||
<img src="https://user-images.githubusercontent.com/3985464/113734260-7ba06900-96fb-11eb-82bc-d4f68a1e2710.png" />
|
||||
</p>
|
||||
<p align="center">
|
||||
<a href="https://discord.gg/UjSMCVnxSB"><img alt="Discord Shield" src="https://img.shields.io/discord/807208614288818196"></a>
|
||||
<a href="https://join.slack.com/t/prowler-workspace/shared_invite/zt-1hix76xsl-2uq222JIXrC7Q8It~9ZNog"><img alt="Slack Shield" src="https://img.shields.io/badge/slack-prowler-brightgreen.svg?logo=slack"></a>
|
||||
<a href="https://pypi.org/project/prowler-cloud/"><img alt="Python Version" src="https://img.shields.io/pypi/v/prowler.svg"></a>
|
||||
<a href="https://pypi.python.org/pypi/prowler-cloud/"><img alt="Python Version" src="https://img.shields.io/pypi/pyversions/prowler.svg"></a>
|
||||
<a href="https://pypistats.org/packages/prowler"><img alt="PyPI Prowler Downloads" src="https://img.shields.io/pypi/dw/prowler.svg?label=prowler%20downloads"></a>
|
||||
<a href="https://pypistats.org/packages/prowler-cloud"><img alt="PyPI Prowler-Cloud Downloads" src="https://img.shields.io/pypi/dw/prowler-cloud.svg?label=prowler-cloud%20downloads"></a>
|
||||
<a href="https://formulae.brew.sh/formula/prowler#default"><img alt="Brew Prowler Downloads" src="https://img.shields.io/homebrew/installs/dm/prowler?label=brew%20downloads"></a>
|
||||
<a href="https://hub.docker.com/r/toniblyx/prowler"><img alt="Docker Pulls" src="https://img.shields.io/docker/pulls/toniblyx/prowler"></a>
|
||||
<a href="https://hub.docker.com/r/toniblyx/prowler"><img alt="Docker" src="https://img.shields.io/docker/cloud/build/toniblyx/prowler"></a>
|
||||
<a href="https://hub.docker.com/r/toniblyx/prowler"><img alt="Docker" src="https://img.shields.io/docker/image-size/toniblyx/prowler"></a>
|
||||
<a href="https://gallery.ecr.aws/o4g1s5r6/prowler"><img width="120" height=19" alt="AWS ECR Gallery" src="https://user-images.githubusercontent.com/3985464/151531396-b6535a68-c907-44eb-95a1-a09508178616.png"></a>
|
||||
<a href="https://gallery.ecr.aws/prowler-cloud/prowler"><img width="120" height=19" alt="AWS ECR Gallery" src="https://user-images.githubusercontent.com/3985464/151531396-b6535a68-c907-44eb-95a1-a09508178616.png"></a>
|
||||
</p>
|
||||
<p align="center">
|
||||
<a href="https://github.com/prowler-cloud/prowler"><img alt="Repo size" src="https://img.shields.io/github/repo-size/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler"><img alt="Lines" src="https://img.shields.io/tokei/lines/github/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler/issues"><img alt="Issues" src="https://img.shields.io/github/issues/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler/releases"><img alt="Version" src="https://img.shields.io/github/v/release/prowler-cloud/prowler?include_prereleases"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler/releases"><img alt="Version" src="https://img.shields.io/github/release-date/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler"><img alt="Contributors" src="https://img.shields.io/github/contributors-anon/prowler-cloud/prowler"></a>
|
||||
<a href="https://github.com/prowler-cloud/prowler"><img alt="License" src="https://img.shields.io/github/license/prowler-cloud/prowler"></a>
|
||||
<a href="https://twitter.com/ToniBlyx"><img alt="Twitter" src="https://img.shields.io/twitter/follow/toniblyx?style=social"></a>
|
||||
<a href="https://twitter.com/prowlercloud"><img alt="Twitter" src="https://img.shields.io/twitter/follow/prowlercloud?style=social"></a>
|
||||
</p>
|
||||
|
||||
<p align="center">
|
||||
<i>Prowler</i> is an Open Source security tool to perform AWS security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It contains more than 200 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custome security frameworks.
|
||||
</p>
|
||||
# Description
|
||||
|
||||
## Table of Contents
|
||||
`Prowler` is an Open Source security tool to perform AWS and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
|
||||
|
||||
- [Description](#description)
|
||||
- [Features](#features)
|
||||
- [High level architecture](#high-level-architecture)
|
||||
- [Requirements and Installation](#requirements-and-installation)
|
||||
- [Usage](#usage)
|
||||
- [Screenshots](#screenshots)
|
||||
- [Advanced Usage](#advanced-usage)
|
||||
- [Security Hub integration](#security-hub-integration)
|
||||
- [CodeBuild deployment](#codebuild-deployment)
|
||||
- [Allowlist](#allowlist-or-remove-a-fail-from-resources)
|
||||
- [Fix](#how-to-fix-every-fail)
|
||||
- [Troubleshooting](#troubleshooting)
|
||||
- [Extras](#extras)
|
||||
- [Forensics Ready Checks](#forensics-ready-checks)
|
||||
- [GDPR Checks](#gdpr-checks)
|
||||
- [HIPAA Checks](#hipaa-checks)
|
||||
- [Trust Boundaries Checks](#trust-boundaries-checks)
|
||||
- [Multi Account and Continuous Monitoring](util/org-multi-account/README.md)
|
||||
- [Custom Checks](#custom-checks)
|
||||
- [Third Party Integrations](#third-party-integrations)
|
||||
- [Full list of checks and groups](/LIST_OF_CHECKS_AND_GROUPS.md)
|
||||
- [License](#license)
|
||||
It contains hundreds of controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.
|
||||
|
||||
## Description
|
||||
# 📖 Documentation
|
||||
|
||||
Prowler is a command line tool that helps you with AWS security assessment, auditing, hardening and incident response.
|
||||
The full documentation can now be found at [https://docs.prowler.cloud](https://docs.prowler.cloud)
|
||||
|
||||
## Looking for Prowler v2 documentation?
|
||||
For Prowler v2 Documentation, please go to https://github.com/prowler-cloud/prowler/tree/2.12.1.
|
||||
|
||||
It follows guidelines of the CIS Amazon Web Services Foundations Benchmark (49 checks) and has more than 100 additional checks including related to GDPR, HIPAA, PCI-DSS, ISO-27001, FFIEC, SOC2 and others.
|
||||
# ⚙️ Install
|
||||
|
||||
Read more about [CIS Amazon Web Services Foundations Benchmark v1.2.0 - 05-23-2018](https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf)
|
||||
## Pip package
|
||||
Prowler is available as a project in [PyPI](https://pypi.org/project/prowler-cloud/), thus can be installed using pip with Python >= 3.9:
|
||||
|
||||
## Features
|
||||
```console
|
||||
pip install prowler
|
||||
prowler -v
|
||||
```
|
||||
More details at https://docs.prowler.cloud
|
||||
|
||||
+200 checks covering security best practices across all AWS regions and most of AWS services and related to the next groups:
|
||||
## Containers
|
||||
|
||||
- Identity and Access Management [group1]
|
||||
- Logging [group2]
|
||||
- Monitoring [group3]
|
||||
- Networking [group4]
|
||||
- CIS Level 1 [cislevel1]
|
||||
- CIS Level 2 [cislevel2]
|
||||
- Extras *see Extras section* [extras]
|
||||
- Forensics related group of checks [forensics-ready]
|
||||
- GDPR [gdpr] Read more [here](#gdpr-checks)
|
||||
- HIPAA [hipaa] Read more [here](#hipaa-checks)
|
||||
- Trust Boundaries [trustboundaries] Read more [here](#trust-boundaries-checks)
|
||||
- Secrets
|
||||
- Internet exposed resources
|
||||
- EKS-CIS
|
||||
- Also includes PCI-DSS, ISO-27001, FFIEC, SOC2, ENS (Esquema Nacional de Seguridad of Spain).
|
||||
- AWS FTR [FTR] Read more [here](#aws-ftr-checks)
|
||||
The available versions of Prowler are the following:
|
||||
|
||||
With Prowler you can:
|
||||
- `latest`: in sync with master branch (bear in mind that it is not a stable version)
|
||||
- `<x.y.z>` (release): you can find the releases [here](https://github.com/prowler-cloud/prowler/releases), those are stable releases.
|
||||
- `stable`: this tag always point to the latest release.
|
||||
|
||||
The container images are available here:
|
||||
|
||||
- Get a direct colorful or monochrome report
|
||||
- A HTML, CSV, JUNIT, JSON or JSON ASFF (Security Hub) format report
|
||||
- Send findings directly to Security Hub
|
||||
- Run specific checks and groups or create your own
|
||||
- Check multiple AWS accounts in parallel or sequentially
|
||||
- And more! Read examples below
|
||||
- [DockerHub](https://hub.docker.com/r/toniblyx/prowler/tags)
|
||||
- [AWS Public ECR](https://gallery.ecr.aws/prowler-cloud/prowler)
|
||||
|
||||
## High level architecture
|
||||
## From Github
|
||||
|
||||
Python >= 3.9 is required with pip and poetry:
|
||||
|
||||
```
|
||||
git clone https://github.com/prowler-cloud/prowler
|
||||
cd prowler
|
||||
poetry shell
|
||||
poetry install
|
||||
python prowler.py -v
|
||||
```
|
||||
|
||||
# 📐✏️ High level architecture
|
||||
|
||||
You can run Prowler from your workstation, an EC2 instance, Fargate or any other container, Codebuild, CloudShell and Cloud9.
|
||||
|
||||
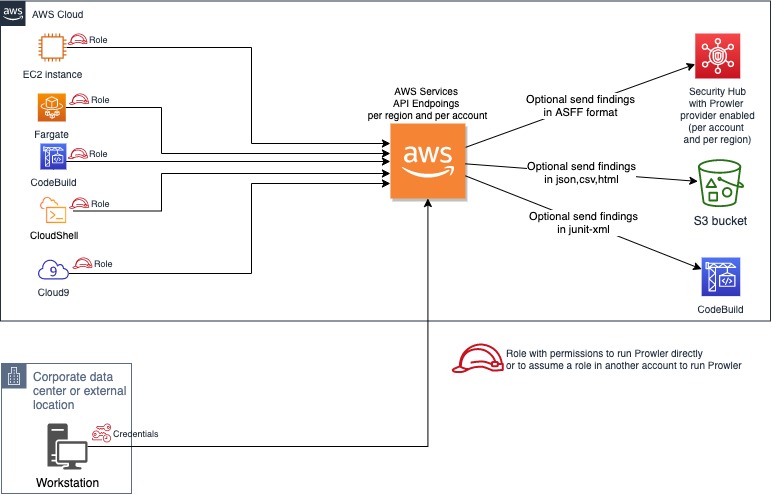
|
||||
## Requirements and Installation
|
||||
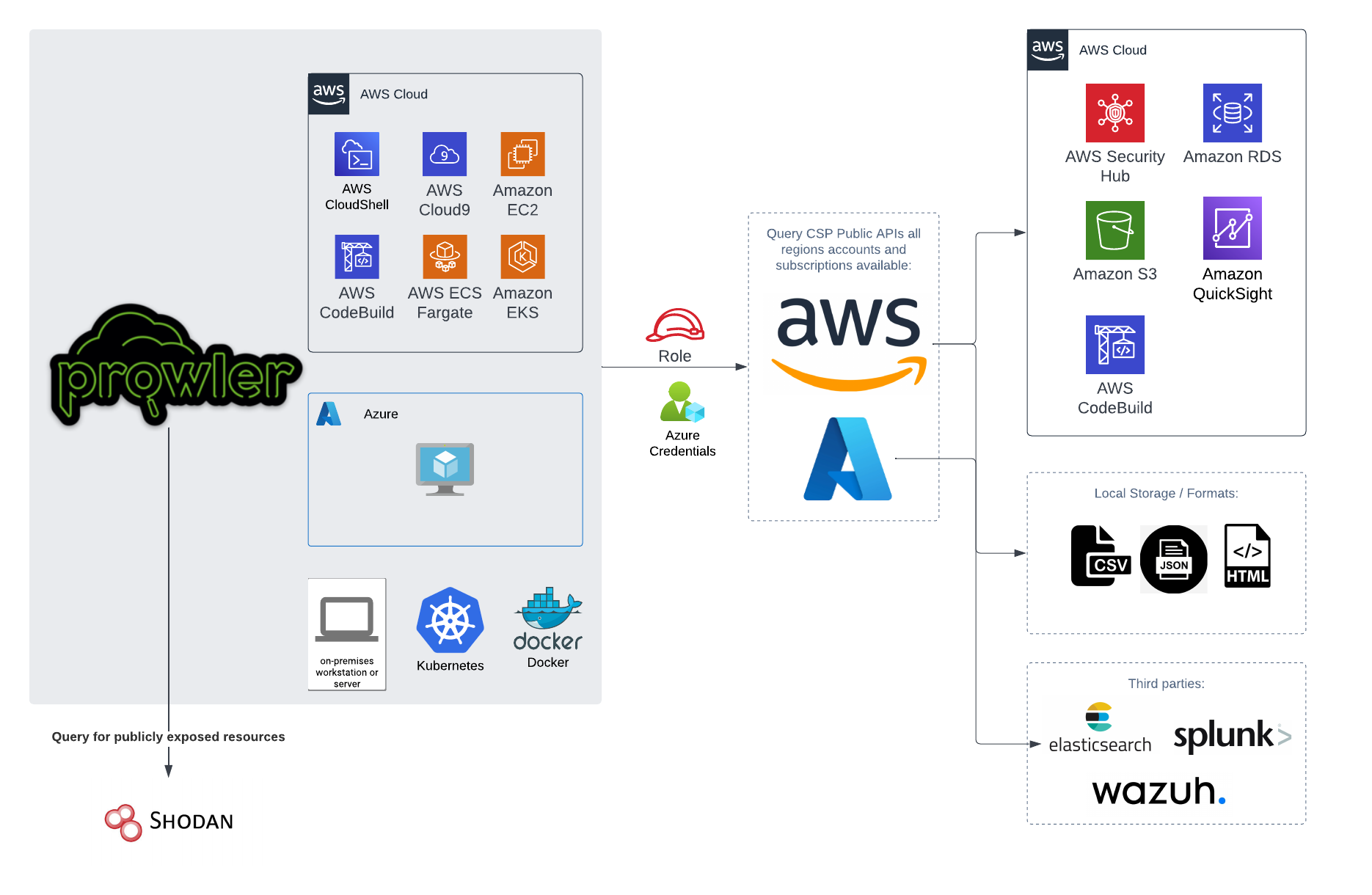
|
||||
|
||||
Prowler has been written in bash using AWS-CLI underneath and it works in Linux, Mac OS or Windows with cygwin or virtualization. Also requires `jq` and `detect-secrets` to work properly.
|
||||
# 📝 Requirements
|
||||
|
||||
- Make sure the latest version of AWS-CLI is installed. It works with either v1 or v2, however _latest v2 is recommended if using new regions since they require STS v2 token_, and other components needed, with Python pip already installed.
|
||||
Prowler has been written in Python using the [AWS SDK (Boto3)](https://boto3.amazonaws.com/v1/documentation/api/latest/index.html#) and [Azure SDK](https://azure.github.io/azure-sdk-for-python/).
|
||||
## AWS
|
||||
|
||||
- For Amazon Linux (`yum` based Linux distributions and AWS CLI v2):
|
||||
```
|
||||
sudo yum update -y
|
||||
sudo yum remove -y awscli
|
||||
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
|
||||
unzip awscliv2.zip
|
||||
sudo ./aws/install
|
||||
sudo yum install -y python3 jq git
|
||||
sudo pip3 install detect-secrets==1.0.3
|
||||
git clone https://github.com/prowler-cloud/prowler
|
||||
```
|
||||
- For Ubuntu Linux (`apt` based Linux distributions and AWS CLI v2):
|
||||
```
|
||||
sudo apt update
|
||||
sudo apt install python3 python3-pip jq git zip
|
||||
pip install detect-secrets==1.0.3
|
||||
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
|
||||
unzip awscliv2.zip
|
||||
sudo ./aws/install
|
||||
git clone https://github.com/prowler-cloud/prowler
|
||||
```
|
||||
Since Prowler uses AWS Credentials under the hood, you can follow any authentication method as described [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-precedence).
|
||||
Make sure you have properly configured your AWS-CLI with a valid Access Key and Region or declare AWS variables properly (or instance profile/role):
|
||||
|
||||
> NOTE: detect-secrets Yelp version is no longer supported, the one from IBM is mantained now. Use the one mentioned below or the specific Yelp version 1.0.3 to make sure it works as expected (`pip install detect-secrets==1.0.3`):
|
||||
```sh
|
||||
pip install "git+https://github.com/ibm/detect-secrets.git@master#egg=detect-secrets"
|
||||
```
|
||||
```console
|
||||
aws configure
|
||||
```
|
||||
|
||||
AWS-CLI can be also installed it using other methods, refer to official documentation for more details: <https://aws.amazon.com/cli/>, but `detect-secrets` has to be installed using `pip` or `pip3`.
|
||||
or
|
||||
|
||||
- Once Prowler repository is cloned, get into the folder and you can run it:
|
||||
```console
|
||||
export AWS_ACCESS_KEY_ID="ASXXXXXXX"
|
||||
export AWS_SECRET_ACCESS_KEY="XXXXXXXXX"
|
||||
export AWS_SESSION_TOKEN="XXXXXXXXX"
|
||||
```
|
||||
|
||||
```sh
|
||||
cd prowler
|
||||
./prowler
|
||||
```
|
||||
Those credentials must be associated to a user or role with proper permissions to do all checks. To make sure, add the following AWS managed policies to the user or role being used:
|
||||
|
||||
- Since Prowler users AWS CLI under the hood, you can follow any authentication method as described [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-precedence). Make sure you have properly configured your AWS-CLI with a valid Access Key and Region or declare AWS variables properly (or instance profile/role):
|
||||
- arn:aws:iam::aws:policy/SecurityAudit
|
||||
- arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
|
||||
```sh
|
||||
aws configure
|
||||
```
|
||||
> Moreover, some read-only additional permissions are needed for several checks, make sure you attach also the custom policy [prowler-additions-policy.json](https://github.com/prowler-cloud/prowler/blob/master/permissions/prowler-additions-policy.json) to the role you are using.
|
||||
|
||||
or
|
||||
> If you want Prowler to send findings to [AWS Security Hub](https://aws.amazon.com/security-hub), make sure you also attach the custom policy [prowler-security-hub.json](https://github.com/prowler-cloud/prowler/blob/master/permissions/prowler-security-hub.json).
|
||||
|
||||
```sh
|
||||
export AWS_ACCESS_KEY_ID="ASXXXXXXX"
|
||||
export AWS_SECRET_ACCESS_KEY="XXXXXXXXX"
|
||||
export AWS_SESSION_TOKEN="XXXXXXXXX"
|
||||
```
|
||||
## Azure
|
||||
|
||||
- Those credentials must be associated to a user or role with proper permissions to do all checks. To make sure, add the AWS managed policies, SecurityAudit and ViewOnlyAccess, to the user or role being used. Policy ARNs are:
|
||||
Prowler for Azure supports the following authentication types:
|
||||
|
||||
```sh
|
||||
arn:aws:iam::aws:policy/SecurityAudit
|
||||
arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
```
|
||||
- Service principal authentication by environment variables (Enterprise Application)
|
||||
- Current az cli credentials stored
|
||||
- Interactive browser authentication
|
||||
- Managed identity authentication
|
||||
|
||||
> Additional permissions needed: to make sure Prowler can scan all services included in the group *Extras*, make sure you attach also the custom policy [prowler-additions-policy.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-additions-policy.json) to the role you are using. If you want Prowler to send findings to [AWS Security Hub](https://aws.amazon.com/security-hub), make sure you also attach the custom policy [prowler-security-hub.json](https://github.com/prowler-cloud/prowler/blob/master/iam/prowler-security-hub.json).
|
||||
### Service Principal authentication
|
||||
|
||||
## Usage
|
||||
To allow Prowler assume the service principal identity to start the scan, it is needed to configure the following environment variables:
|
||||
|
||||
1. Run the `prowler` command without options (it will use your environment variable credentials if they exist or will default to using the `~/.aws/credentials` file and run checks over all regions when needed. The default region is us-east-1):
|
||||
|
||||
```sh
|
||||
./prowler
|
||||
```
|
||||
|
||||
Use `-l` to list all available checks and the groups (sections) that reference them. To list all groups use `-L` and to list content of a group use `-l -g <groupname>`.
|
||||
|
||||
If you want to avoid installing dependencies run it using Docker:
|
||||
|
||||
```sh
|
||||
docker run -ti --rm --name prowler --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest
|
||||
```
|
||||
|
||||
In case you want to get reports created by Prowler use docker volume option like in the example below:
|
||||
```sh
|
||||
docker run -ti --rm -v /your/local/output:/prowler/output --name prowler --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest -g hipaa -M csv,json,html
|
||||
```
|
||||
|
||||
1. For custom AWS-CLI profile and region, use the following: (it will use your custom profile and run checks over all regions when needed):
|
||||
|
||||
```sh
|
||||
./prowler -p custom-profile -r us-east-1
|
||||
```
|
||||
|
||||
1. For a single check use option `-c`:
|
||||
|
||||
```sh
|
||||
./prowler -c check310
|
||||
```
|
||||
|
||||
With Docker:
|
||||
|
||||
```sh
|
||||
docker run -ti --rm --name prowler --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest "-c check310"
|
||||
```
|
||||
|
||||
or multiple checks separated by comma:
|
||||
|
||||
```sh
|
||||
./prowler -c check310,check722
|
||||
```
|
||||
|
||||
or all checks but some of them:
|
||||
|
||||
```sh
|
||||
./prowler -E check42,check43
|
||||
```
|
||||
|
||||
or for custom profile and region:
|
||||
|
||||
```sh
|
||||
./prowler -p custom-profile -r us-east-1 -c check11
|
||||
```
|
||||
|
||||
or for a group of checks use group name:
|
||||
|
||||
```sh
|
||||
./prowler -g group1 # for iam related checks
|
||||
```
|
||||
|
||||
or exclude some checks in the group:
|
||||
|
||||
```sh
|
||||
./prowler -g group4 -E check42,check43
|
||||
```
|
||||
|
||||
Valid check numbers are based on the AWS CIS Benchmark guide, so 1.1 is check11 and 3.10 is check310
|
||||
|
||||
### Regions
|
||||
|
||||
By default, Prowler scans all opt-in regions available, that might take a long execution time depending on the number of resources and regions used. Same applies for GovCloud or China regions. See below Advance usage for examples.
|
||||
|
||||
Prowler has two parameters related to regions: `-r` that is used query AWS services API endpoints (it uses `us-east-1` by default and required for GovCloud or China) and the option `-f` that is to filter those regions you only want to scan. For example if you want to scan Dublin only use `-f eu-west-1` and if you want to scan Dublin and Ohio `-f eu-west-1,us-east-1`, note the regions are separated by a comma deliminator (it can be used as before with `-f 'eu-west-1,us-east-1'`).
|
||||
|
||||
## Screenshots
|
||||
|
||||
- Sample screenshot of default console report first lines of command `./prowler`:
|
||||
|
||||
<img width="900" src="https://user-images.githubusercontent.com/3985464/141444529-84640bed-be0b-4112-80a2-2a43e3ebf53f.png">
|
||||
|
||||
- Sample screenshot of the html output `-M html`:
|
||||
|
||||
<img width="900" alt="Prowler html" src="https://user-images.githubusercontent.com/3985464/141443976-41d32cc2-533d-405a-92cb-affc3995d6ec.png">
|
||||
|
||||
- Sample screenshot of the Quicksight dashboard, see [quicksight-security-dashboard.workshop.aws](https://quicksight-security-dashboard.workshop.aws/):
|
||||
|
||||
<img width="900" alt="Prowler with Quicksight" src="https://user-images.githubusercontent.com/3985464/128932819-0156e838-286d-483c-b953-fda68a325a3d.png">
|
||||
|
||||
- Sample screenshot of the junit-xml output in CodeBuild `-M junit-xml`:
|
||||
|
||||
<img width="900" src="https://user-images.githubusercontent.com/3985464/113942824-ca382b00-9801-11eb-84e5-d7731548a7a9.png">
|
||||
|
||||
### Save your reports
|
||||
|
||||
1. If you want to save your report for later analysis thare are different ways, natively (supported text, mono, csv, json, json-asff, junit-xml and html, see note below for more info):
|
||||
|
||||
```sh
|
||||
./prowler -M csv
|
||||
```
|
||||
|
||||
or with multiple formats at the same time:
|
||||
|
||||
```sh
|
||||
./prowler -M csv,json,json-asff,html
|
||||
```
|
||||
|
||||
or just a group of checks in multiple formats:
|
||||
|
||||
```sh
|
||||
./prowler -g gdpr -M csv,json,json-asff
|
||||
```
|
||||
|
||||
or if you want a sorted and dynamic HTML report do:
|
||||
|
||||
```sh
|
||||
./prowler -M html
|
||||
```
|
||||
|
||||
Now `-M` creates a file inside the prowler `output` directory named `prowler-output-AWSACCOUNTID-YYYYMMDDHHMMSS.format`. You don't have to specify anything else, no pipes, no redirects.
|
||||
|
||||
or just saving the output to a file like below:
|
||||
|
||||
```sh
|
||||
./prowler -M mono > prowler-report.txt
|
||||
```
|
||||
|
||||
To generate JUnit report files, include the junit-xml format. This can be combined with any other format. Files are written inside a prowler root directory named `junit-reports`:
|
||||
|
||||
```sh
|
||||
./prowler -M text,junit-xml
|
||||
```
|
||||
|
||||
>Note about output formats to use with `-M`: "text" is the default one with colors, "mono" is like default one but monochrome, "csv" is comma separated values, "json" plain basic json (without comma between lines) and "json-asff" is also json with Amazon Security Finding Format that you can ship to Security Hub using `-S`.
|
||||
|
||||
To save your report in an S3 bucket, use `-B` to define a custom output bucket along with `-M` to define the output format that is going to be uploaded to S3:
|
||||
|
||||
```sh
|
||||
./prowler -M csv -B my-bucket/folder/
|
||||
```
|
||||
>In the case you do not want to use the assumed role credentials but the initial credentials to put the reports into the S3 bucket, use `-D` instead of `-B`. Make sure that the used credentials have s3:PutObject permissions in the S3 path where the reports are going to be uploaded.
|
||||
|
||||
When generating multiple formats and running using Docker, to retrieve the reports, bind a local directory to the container, e.g.:
|
||||
|
||||
```sh
|
||||
docker run -ti --rm --name prowler --volume "$(pwd)":/prowler/output --env AWS_ACCESS_KEY_ID --env AWS_SECRET_ACCESS_KEY --env AWS_SESSION_TOKEN toniblyx/prowler:latest -M csv,json
|
||||
```
|
||||
|
||||
1. To perform an assessment based on CIS Profile Definitions you can use cislevel1 or cislevel2 with `-g` flag, more information about this [here, page 8](https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf):
|
||||
|
||||
```sh
|
||||
./prowler -g cislevel1
|
||||
```
|
||||
|
||||
1. If you want to run Prowler to check multiple AWS accounts in parallel (runs up to 4 simultaneously `-P 4`) but you may want to read below in Advanced Usage section to do so assuming a role:
|
||||
|
||||
```sh
|
||||
grep -E '^\[([0-9A-Aa-z_-]+)\]' ~/.aws/credentials | tr -d '][' | shuf | \
|
||||
xargs -n 1 -L 1 -I @ -r -P 4 ./prowler -p @ -M csv 2> /dev/null >> all-accounts.csv
|
||||
```
|
||||
|
||||
1. For help about usage run:
|
||||
|
||||
```
|
||||
./prowler -h
|
||||
```
|
||||
|
||||
## Advanced Usage
|
||||
|
||||
### Assume Role:
|
||||
|
||||
Prowler uses the AWS CLI underneath so it uses the same authentication methods. However, there are few ways to run Prowler against multiple accounts using IAM Assume Role feature depending on eachg use case. You can just set up your custom profile inside `~/.aws/config` with all needed information about the role to assume then call it with `./prowler -p your-custom-profile`. Additionally you can use `-A 123456789012` and `-R RemoteRoleToAssume` and Prowler will get those temporary credentials using `aws sts assume-role`, set them up as environment variables and run against that given account. To create a role to assume in multiple accounts easier eather as CFN Stack or StackSet, look at [this CloudFormation template](iam/create_role_to_assume_cfn.yaml) and adapt it.
|
||||
|
||||
```sh
|
||||
./prowler -A 123456789012 -R ProwlerRole
|
||||
```console
|
||||
export AZURE_CLIENT_ID="XXXXXXXXX"
|
||||
export AZURE_TENANT_ID="XXXXXXXXX"
|
||||
export AZURE_CLIENT_SECRET="XXXXXXX"
|
||||
```
|
||||
|
||||
```sh
|
||||
./prowler -A 123456789012 -R ProwlerRole -I 123456
|
||||
If you try to execute Prowler with the `--sp-env-auth` flag and those variables are empty or not exported, the execution is going to fail.
|
||||
### AZ CLI / Browser / Managed Identity authentication
|
||||
|
||||
The other three cases do not need additional configuration, `--az-cli-auth` and `--managed-identity-auth` are automated options, `--browser-auth` needs the user to authenticate using the default browser to start the scan.
|
||||
|
||||
### Permissions
|
||||
|
||||
To use each one, you need to pass the proper flag to the execution. Prowler for Azure handles two types of permission scopes, which are:
|
||||
|
||||
- **Azure Active Directory permissions**: Used to retrieve metadata from the identity assumed by Prowler and future AAD checks (not mandatory to have access to execute the tool)
|
||||
- **Subscription scope permissions**: Required to launch the checks against your resources, mandatory to launch the tool.
|
||||
|
||||
|
||||
#### Azure Active Directory scope
|
||||
|
||||
Azure Active Directory (AAD) permissions required by the tool are the following:
|
||||
|
||||
- `Directory.Read.All`
|
||||
- `Policy.Read.All`
|
||||
|
||||
|
||||
#### Subscriptions scope
|
||||
|
||||
Regarding the subscription scope, Prowler by default scans all the subscriptions that is able to list, so it is required to add the following RBAC builtin roles per subscription to the entity that is going to be assumed by the tool:
|
||||
|
||||
- `Security Reader`
|
||||
- `Reader`
|
||||
|
||||
|
||||
# 💻 Basic Usage
|
||||
|
||||
To run prowler, you will need to specify the provider (e.g aws or azure):
|
||||
|
||||
```console
|
||||
prowler <provider>
|
||||
```
|
||||
|
||||
> *NOTE 1 about Session Duration*: By default it gets credentials valid for 1 hour (3600 seconds). Depending on the mount of checks you run and the size of your infrastructure, Prowler may require more than 1 hour to finish. Use option `-T <seconds>` to allow up to 12h (43200 seconds). To allow more than 1h you need to modify *"Maximum CLI/API session duration"* for that particular role, read more [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use.html#id_roles_use_view-role-max-session).
|
||||
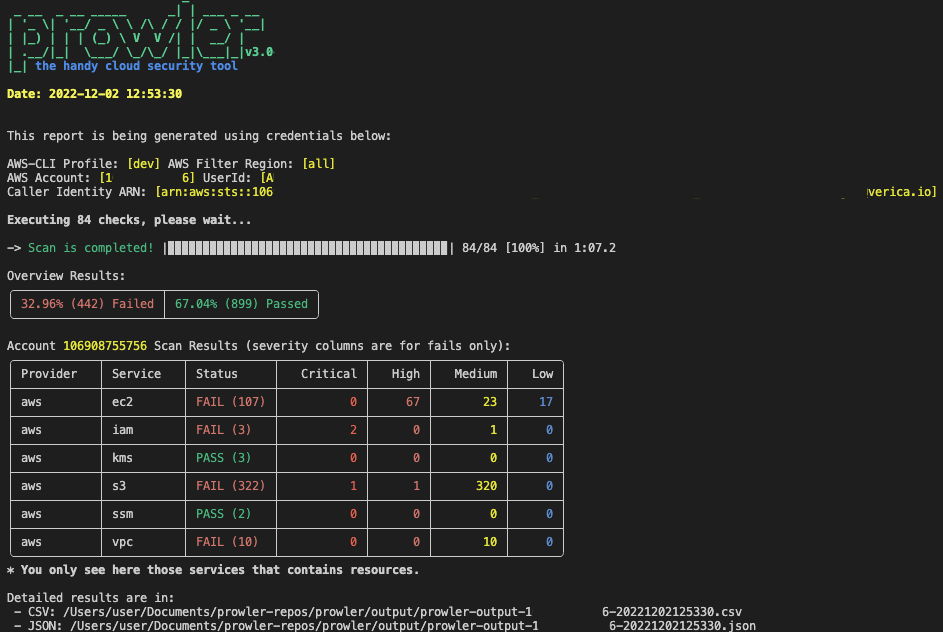
|
||||
|
||||
> *NOTE 2 about Session Duration*: Bear in mind that if you are using roles assumed by role chaining there is a hard limit of 1 hour so consider not using role chaining if possible, read more about that, in foot note 1 below the table [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use.html).
|
||||
> Running the `prowler` command without options will use your environment variable credentials.
|
||||
|
||||
For example, if you want to get only the fails in CSV format from all checks regarding RDS without banner from the AWS Account 123456789012 assuming the role RemoteRoleToAssume and set a fixed session duration of 1h:
|
||||
By default, prowler will generate a CSV, a JSON and a HTML report, however you can generate JSON-ASFF (only for AWS Security Hub) report with `-M` or `--output-modes`:
|
||||
|
||||
```sh
|
||||
./prowler -A 123456789012 -R RemoteRoleToAssume -T 3600 -b -M cvs -q -g rds
|
||||
```
|
||||
or with a given External ID:
|
||||
```sh
|
||||
./prowler -A 123456789012 -R RemoteRoleToAssume -T 3600 -I 123456 -b -M cvs -q -g rds
|
||||
```console
|
||||
prowler <provider> -M csv json json-asff html
|
||||
```
|
||||
|
||||
### Assume Role and across all accounts in AWS Organizations or just a list of accounts:
|
||||
The html report will be located in the `output` directory as the other files and it will look like:
|
||||
|
||||
If you want to run Prowler or just a check or a group across all accounts of AWS Organizations you can do this:
|
||||
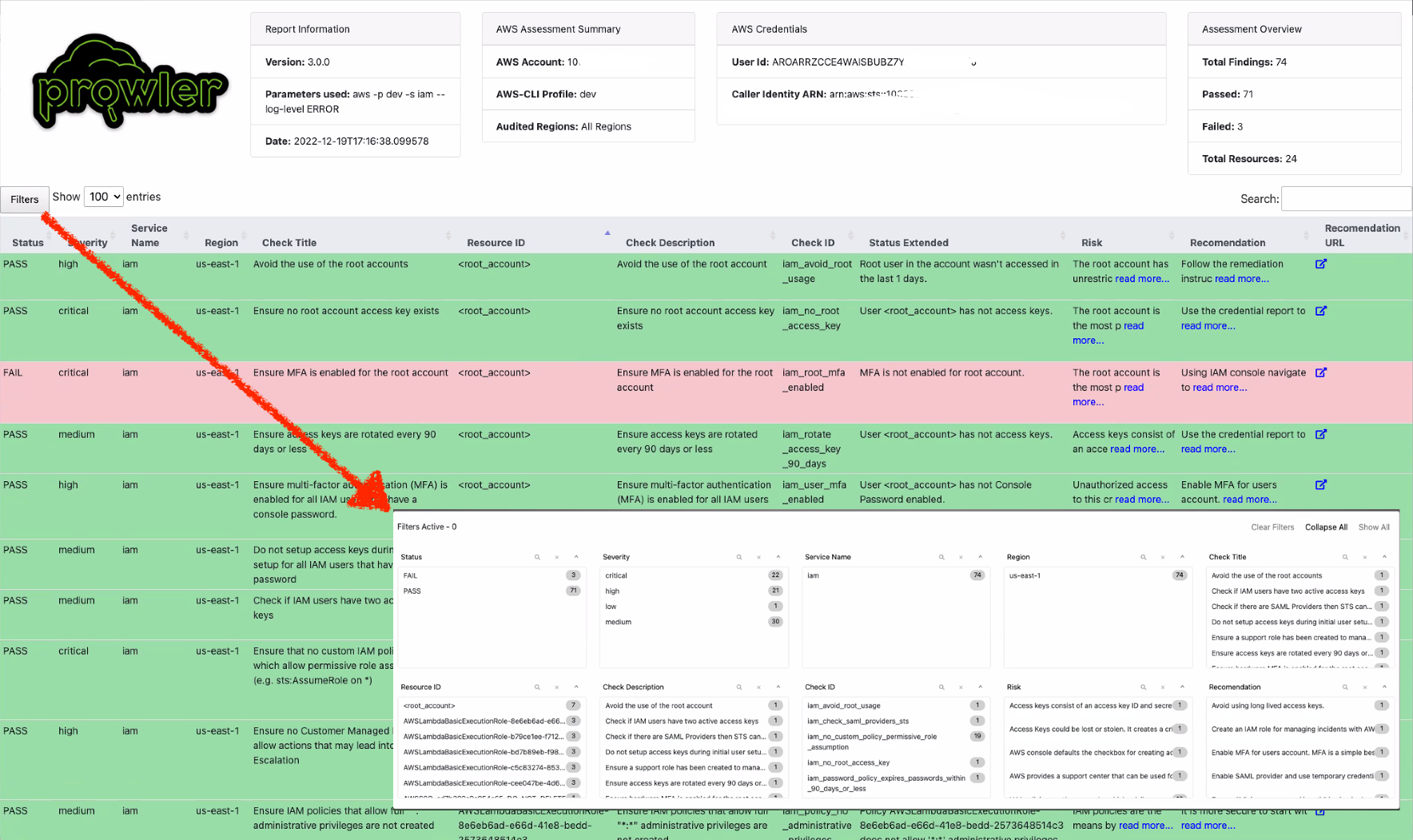
|
||||
|
||||
First get a list of accounts that are not suspended:
|
||||
```
|
||||
ACCOUNTS_IN_ORGS=$(aws organizations list-accounts --query Accounts[?Status==`ACTIVE`].Id --output text)
|
||||
```
|
||||
Then run Prowler to assume a role (same in all members) per each account, in this example it is just running one particular check:
|
||||
```
|
||||
for accountId in $ACCOUNTS_IN_ORGS; do ./prowler -A $accountId -R RemoteRoleToAssume -c extra79; done
|
||||
```
|
||||
Using the same for loop it can be scanned a list of accounts with a variable like `ACCOUNTS_LIST='11111111111 2222222222 333333333'`
|
||||
You can use `-l`/`--list-checks` or `--list-services` to list all available checks or services within the provider.
|
||||
|
||||
### Get AWS Account details from your AWS Organization:
|
||||
|
||||
From Prowler v2.8, you can get additional information of the scanned account in CSV and JSON outputs. When scanning a single account you get the Account ID as part of the output. Now, if you have AWS Organizations and are scanning multiple accounts using the assume role functionality, Prowler can get your account details like Account Name, Email, ARN, Organization ID and Tags and you will have them next to every finding in the CSV and JSON outputs.
|
||||
In order to do that you can use the new option `-O <management account id>`, requires `-R <role to assume>` and also needs permissions `organizations:ListAccounts*` and `organizations:ListTagsForResource`. See the following sample command:
|
||||
```
|
||||
./prowler -R ProwlerScanRole -A 111111111111 -O 222222222222 -M json,csv
|
||||
```
|
||||
In that command Prowler will scan the account `111111111111` assuming the role `ProwlerScanRole` and getting the account details from the AWS Organizatiosn management account `222222222222` assuming the same role `ProwlerScanRole` for that and creating two reports with those details in JSON and CSV.
|
||||
|
||||
In the JSON output below (redacted) you can see tags coded in base64 to prevent breaking CSV or JSON due to its format:
|
||||
|
||||
```json
|
||||
"Account Email": "my-prod-account@domain.com",
|
||||
"Account Name": "my-prod-account",
|
||||
"Account ARN": "arn:aws:organizations::222222222222:account/o-abcde1234/111111111111",
|
||||
"Account Organization": "o-abcde1234",
|
||||
"Account tags": "\"eyJUYWdzIjpasf0=\""
|
||||
```
|
||||
The additional fields in CSV header output are as follow:
|
||||
|
||||
```csv
|
||||
ACCOUNT_DETAILS_EMAIL,ACCOUNT_DETAILS_NAME,ACCOUNT_DETAILS_ARN,ACCOUNT_DETAILS_ORG,ACCOUNT_DETAILS_TAGS
|
||||
```console
|
||||
prowler <provider> --list-checks
|
||||
prowler <provider> --list-services
|
||||
```
|
||||
|
||||
### GovCloud
|
||||
For executing specific checks or services you can use options `-c`/`--checks` or `-s`/`--services`:
|
||||
|
||||
Prowler runs in GovCloud regions as well. To make sure it points to the right API endpoint use `-r` to either `us-gov-west-1` or `us-gov-east-1`. If not filter region is used it will look for resources in both GovCloud regions by default:
|
||||
```sh
|
||||
./prowler -r us-gov-west-1
|
||||
```
|
||||
> For Security Hub integration see below in Security Hub section.
|
||||
|
||||
### Custom folder for custom checks
|
||||
|
||||
Flag `-x /my/own/checks` will include any check in that particular directory (files must start by check). To see how to write checks see [Add Custom Checks](#add-custom-checks) section.
|
||||
|
||||
S3 URIs are also supported as custom folders for custom checks, e.g. `s3://bucket/prefix/checks`. Prowler will download the folder locally and run the checks as they are called with default execution,`-c` or `-g`.
|
||||
>Make sure that the used credentials have s3:GetObject permissions in the S3 path where the custom checks are located.
|
||||
|
||||
### Show or log only FAILs
|
||||
|
||||
In order to remove noise and get only FAIL findings there is a `-q` flag that makes Prowler to show and log only FAILs.
|
||||
It can be combined with any other option.
|
||||
Will show WARNINGS when a resource is excluded, just to take into consideration.
|
||||
|
||||
```sh
|
||||
# -q option combined with -M csv -b
|
||||
./prowler -q -M csv -b
|
||||
```console
|
||||
prowler aws --checks s3_bucket_public_access
|
||||
prowler aws --services s3 ec2
|
||||
```
|
||||
|
||||
### Set the entropy limit for detect-secrets
|
||||
Also, checks and services can be excluded with options `-e`/`--excluded-checks` or `--excluded-services`:
|
||||
|
||||
Sets the entropy limit for high entropy base64 strings from environment variable `BASE64_LIMIT`. Value must be between 0.0 and 8.0, defaults is 4.5.
|
||||
Sets the entropy limit for high entropy hex strings from environment variable `HEX_LIMIT`. Value must be between 0.0 and 8.0, defaults is 3.0.
|
||||
|
||||
```sh
|
||||
export BASE64_LIMIT=4.5
|
||||
export HEX_LIMIT=3.0
|
||||
```
|
||||
### Run Prowler using AWS CloudShell
|
||||
|
||||
An easy way to run Prowler to scan your account is using AWS CloudShell. Read more and learn how to do it [here](util/cloudshell/README.md).
|
||||
|
||||
## Security Hub integration
|
||||
|
||||
Since October 30th 2020 (version v2.3RC5), Prowler supports natively and as **official integration** sending findings to [AWS Security Hub](https://aws.amazon.com/security-hub). This integration allows Prowler to import its findings to AWS Security Hub. With Security Hub, you now have a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, and AWS Firewall Manager, as well as from AWS Partner solutions and from Prowler for free.
|
||||
|
||||
Before sending findings to Prowler, you need to perform next steps:
|
||||
1. Since Security Hub is a region based service, enable it in the region or regions you require. Use the AWS Management Console or using the AWS CLI with this command if you have enough permissions:
|
||||
- `aws securityhub enable-security-hub --region <region>`.
|
||||
2. Enable Prowler as partner integration integration. Use the AWS Management Console or using the AWS CLI with this command if you have enough permissions:
|
||||
- `aws securityhub enable-import-findings-for-product --region <region> --product-arn arn:aws:securityhub:<region>::product/prowler/prowler` (change region also inside the ARN).
|
||||
- Using the AWS Management Console:
|
||||

|
||||
3. As mentioned in section "Custom IAM Policy", to allow Prowler to import its findings to AWS Security Hub you need to add the policy below to the role or user running Prowler:
|
||||
- [iam/prowler-security-hub.json](iam/prowler-security-hub.json)
|
||||
|
||||
Once it is enabled, it is as simple as running the command below (for all regions):
|
||||
|
||||
```sh
|
||||
./prowler -M json-asff -S
|
||||
```
|
||||
or for only one filtered region like eu-west-1:
|
||||
```sh
|
||||
./prowler -M json-asff -q -S -f eu-west-1
|
||||
```
|
||||
> Note 1: It is recommended to send only fails to Security Hub and that is possible adding `-q` to the command.
|
||||
|
||||
> Note 2: Since Prowler perform checks to all regions by defaults you may need to filter by region when runing Security Hub integration, as shown in the example above. Remember to enable Security Hub in the region or regions you need by calling `aws securityhub enable-security-hub --region <region>` and run Prowler with the option `-f <region>` (if no region is used it will try to push findings in all regions hubs).
|
||||
|
||||
> Note 3: to have updated findings in Security Hub you have to run Prowler periodically. Once a day or every certain amount of hours.
|
||||
|
||||
Once you run findings for first time you will be able to see Prowler findings in Findings section:
|
||||
|
||||

|
||||
|
||||
### Security Hub in GovCloud regions
|
||||
|
||||
To use Prowler and Security Hub integration in GovCloud there is an additional requirement, usage of `-r` is needed to point the API queries to the right API endpoint. Here is a sample command that sends only failed findings to Security Hub in region `us-gov-west-1`:
|
||||
```
|
||||
./prowler -r us-gov-west-1 -f us-gov-west-1 -S -M csv,json-asff -q
|
||||
```console
|
||||
prowler aws --excluded-checks s3_bucket_public_access
|
||||
prowler aws --excluded-services s3 ec2
|
||||
```
|
||||
|
||||
### Security Hub in China regions
|
||||
You can always use `-h`/`--help` to access to the usage information and all the possible options:
|
||||
|
||||
To use Prowler and Security Hub integration in China regions there is an additional requirement, usage of `-r` is needed to point the API queries to the right API endpoint. Here is a sample command that sends only failed findings to Security Hub in region `cn-north-1`:
|
||||
```
|
||||
./prowler -r cn-north-1 -f cn-north-1 -q -S -M csv,json-asff
|
||||
```console
|
||||
prowler -h
|
||||
```
|
||||
|
||||
## CodeBuild deployment
|
||||
|
||||
Either to run Prowler once or based on a schedule this template makes it pretty straight forward. This template will create a CodeBuild environment and run Prowler directly leaving all reports in a bucket and creating a report also inside CodeBuild basedon the JUnit output from Prowler. Scheduling can be cron based like `cron(0 22 * * ? *)` or rate based like `rate(5 hours)` since CloudWatch Event rules (or Eventbridge) is used here.
|
||||
|
||||
The Cloud Formation template that helps you doing that is [here](https://github.com/prowler-cloud/prowler/blob/master/util/codebuild/codebuild-prowler-audit-account-cfn.yaml).
|
||||
|
||||
> This is a simple solution to monitor one account. For multiples accounts see [Multi Account and Continuous Monitoring](util/org-multi-account/README.md).
|
||||
|
||||
## Allowlist or remove a fail from resources
|
||||
|
||||
Sometimes you may find resources that are intentionally configured in a certain way that may be a bad practice but it is all right with it, for example an S3 bucket open to the internet hosting a web site, or a security group with an open port needed in your use case. Now you can use `-w allowlist_sample.txt` and add your resources as `checkID:resourcename` as in this command:
|
||||
|
||||
## Checks Configurations
|
||||
Several Prowler's checks have user configurable variables that can be modified in a common **configuration file**.
|
||||
This file can be found in the following path:
|
||||
```
|
||||
./prowler -w allowlist_sample.txt
|
||||
prowler/config/config.yaml
|
||||
```
|
||||
|
||||
S3 URIs are also supported as allowlist file, e.g. `s3://bucket/prefix/allowlist_sample.txt`
|
||||
>Make sure that the used credentials have s3:GetObject permissions in the S3 path where the allowlist file is located.
|
||||
## AWS
|
||||
|
||||
DynamoDB table ARNs are also supported as allowlist file, e.g. `arn:aws:dynamodb:us-east-1:111111222222:table/allowlist`
|
||||
>Make sure that the table has `account_id` as partition key and `rule` as sort key, and that the used credentials have `dynamodb:PartiQLSelect` permissions in the table.
|
||||
><p align="left"><img src="https://user-images.githubusercontent.com/38561120/165769502-296f9075-7cc8-445e-8158-4b21804bfe7e.png" alt="image" width="397" height="252" /></p>
|
||||
Use a custom AWS profile with `-p`/`--profile` and/or AWS regions which you want to audit with `-f`/`--filter-region`:
|
||||
|
||||
>The field `account_id` can contains either an account ID or an `*` (which applies to all the accounts that use this table as a whitelist). As in the traditional allowlist file, the `rule` field must contain `checkID:resourcename` pattern.
|
||||
><p><img src="https://user-images.githubusercontent.com/38561120/165770610-ed5c2764-7538-44c2-9195-bcfdecc4ef9b.png" alt="image" width="394" /></p>
|
||||
|
||||
|
||||
|
||||
Allowlist option works along with other options and adds a `WARNING` instead of `INFO`, `PASS` or `FAIL` to any output format except for `json-asff`.
|
||||
|
||||
## How to fix every FAIL
|
||||
|
||||
Check your report and fix the issues following all specific guidelines per check in <https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf>
|
||||
|
||||
## Troubleshooting
|
||||
|
||||
### STS expired token
|
||||
|
||||
If you are using an STS token for AWS-CLI and your session is expired you probably get this error:
|
||||
|
||||
```sh
|
||||
A client error (ExpiredToken) occurred when calling the GenerateCredentialReport operation: The security token included in the request is expired
|
||||
```console
|
||||
prowler aws --profile custom-profile -f us-east-1 eu-south-2
|
||||
```
|
||||
> By default, `prowler` will scan all AWS regions.
|
||||
|
||||
To fix it, please renew your token by authenticating again to the AWS API, see next section below if you use MFA.
|
||||
## Azure
|
||||
|
||||
### Run Prowler with MFA protected credentials
|
||||
With Azure you need to specify which auth method is going to be used:
|
||||
|
||||
To run Prowler using a profile that requires MFA you just need to get the session token before hand. Just make sure you use this command:
|
||||
|
||||
```sh
|
||||
aws --profile <YOUR_AWS_PROFILE> sts get-session-token --duration 129600 --serial-number <ARN_OF_MFA> --token-code <MFA_TOKEN_CODE> --output text
|
||||
```console
|
||||
prowler azure [--sp-env-auth, --az-cli-auth, --browser-auth, --managed-identity-auth]
|
||||
```
|
||||
> By default, `prowler` will scan all Azure subscriptions.
|
||||
|
||||
Once you get your token you can export it as environment variable:
|
||||
# 🎉 New Features
|
||||
|
||||
```sh
|
||||
export AWS_PROFILE=YOUR_AWS_PROFILE
|
||||
export AWS_SESSION_TOKEN=YOUR_NEW_TOKEN
|
||||
AWS_SECRET_ACCESS_KEY=YOUR_SECRET
|
||||
export AWS_ACCESS_KEY_ID=YOUR_KEY
|
||||
```
|
||||
- Python: we got rid of all bash and it is now all in Python.
|
||||
- Faster: huge performance improvements (same account from 2.5 hours to 4 minutes).
|
||||
- Developers and community: we have made it easier to contribute with new checks and new compliance frameworks. We also included unit tests.
|
||||
- Multi-cloud: in addition to AWS, we have added Azure, we plan to include GCP and OCI soon, let us know if you want to contribute!
|
||||
|
||||
or set manually up your `~/.aws/credentials` file properly.
|
||||
|
||||
There are some helpfull tools to save time in this process like [aws-mfa-script](https://github.com/asagage/aws-mfa-script) or [aws-cli-mfa](https://github.com/sweharris/aws-cli-mfa).
|
||||
|
||||
### AWS Managed IAM Policies
|
||||
|
||||
[ViewOnlyAccess](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_job-functions.html#jf_view-only-user)
|
||||
- Use case: This user can view a list of AWS resources and basic metadata in the account across all services. The user cannot read resource content or metadata that goes beyond the quota and list information for resources.
|
||||
- Policy description: This policy grants List*, Describe*, Get*, View*, and Lookup* access to resources for most AWS services. To see what actions this policy includes for each service, see [ViewOnlyAccess Permissions](https://console.aws.amazon.com/iam/home#policies/arn:aws:iam::aws:policy/job-function/ViewOnlyAccess)
|
||||
|
||||
[SecurityAudit](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_job-functions.html#jf_security-auditor)
|
||||
- Use case: This user monitors accounts for compliance with security requirements. This user can access logs and events to investigate potential security breaches or potential malicious activity.
|
||||
- Policy description: This policy grants permissions to view configuration data for many AWS services and to review their logs. To see what actions this policy includes for each service, see [SecurityAudit Permissions](https://console.aws.amazon.com/iam/home#policies/arn:aws:iam::aws:policy/SecurityAudit)
|
||||
|
||||
### Custom IAM Policy
|
||||
|
||||
[Prowler-Additions-Policy](iam/prowler-additions-policy.json)
|
||||
|
||||
Some new and specific checks require Prowler to inherit more permissions than SecurityAudit and ViewOnlyAccess to work properly. In addition to the AWS managed policies, "SecurityAudit" and "ViewOnlyAccess", the user/role you use for checks may need to be granted a custom policy with a few more read-only permissions (to support additional services mostly). Here is an example policy with the additional rights, "Prowler-Additions-Policy" (see below bootstrap script for set it up):
|
||||
|
||||
- [iam/prowler-additions-policy.json](iam/prowler-additions-policy.json)
|
||||
|
||||
[Prowler-Security-Hub Policy](iam/prowler-security-hub.json)
|
||||
|
||||
Allows Prowler to import its findings to [AWS Security Hub](https://aws.amazon.com/security-hub). More information in [Security Hub integration](#security-hub-integration):
|
||||
|
||||
- [iam/prowler-security-hub.json](iam/prowler-security-hub.json)
|
||||
|
||||
### Bootstrap Script
|
||||
|
||||
Quick bash script to set up a "prowler" IAM user with "SecurityAudit" and "ViewOnlyAccess" group with the required permissions (including "Prowler-Additions-Policy"). To run the script below, you need user with administrative permissions; set the `AWS_DEFAULT_PROFILE` to use that account:
|
||||
|
||||
```sh
|
||||
export AWS_DEFAULT_PROFILE=default
|
||||
export ACCOUNT_ID=$(aws sts get-caller-identity --query 'Account' | tr -d '"')
|
||||
aws iam create-group --group-name Prowler
|
||||
aws iam create-policy --policy-name Prowler-Additions-Policy --policy-document file://$(pwd)/iam/prowler-additions-policy.json
|
||||
aws iam attach-group-policy --group-name Prowler --policy-arn arn:aws:iam::aws:policy/SecurityAudit
|
||||
aws iam attach-group-policy --group-name Prowler --policy-arn arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
|
||||
aws iam attach-group-policy --group-name Prowler --policy-arn arn:aws:iam::${ACCOUNT_ID}:policy/Prowler-Additions-Policy
|
||||
aws iam create-user --user-name prowler
|
||||
aws iam add-user-to-group --user-name prowler --group-name Prowler
|
||||
aws iam create-access-key --user-name prowler
|
||||
unset ACCOUNT_ID AWS_DEFAULT_PROFILE
|
||||
```
|
||||
|
||||
The `aws iam create-access-key` command will output the secret access key and the key id; keep these somewhere safe, and add them to `~/.aws/credentials` with an appropriate profile name to use them with Prowler. This is the only time they secret key will be shown. If you lose it, you will need to generate a replacement.
|
||||
|
||||
> [This CloudFormation template](iam/create_role_to_assume_cfn.yaml) may also help you on that task.
|
||||
|
||||
## Extras
|
||||
|
||||
We are adding additional checks to improve the information gather from each account, these checks are out of the scope of the CIS benchmark for AWS, but we consider them very helpful to get to know each AWS account set up and find issues on it.
|
||||
|
||||
Some of these checks look for publicly facing resources may not actually be fully public due to other layered controls like S3 Bucket Policies, Security Groups or Network ACLs.
|
||||
|
||||
To list all existing checks in the extras group run the command below:
|
||||
|
||||
```sh
|
||||
./prowler -l -g extras
|
||||
```
|
||||
|
||||
>There are some checks not included in that list, they are experimental or checks that takes long to run like `extra759` and `extra760` (search for secrets in Lambda function variables and code).
|
||||
|
||||
To check all extras in one command:
|
||||
|
||||
```sh
|
||||
./prowler -g extras
|
||||
```
|
||||
|
||||
or to run just one of the checks:
|
||||
|
||||
```sh
|
||||
./prowler -c extraNUMBER
|
||||
```
|
||||
|
||||
or to run multiple extras in one go:
|
||||
|
||||
```sh
|
||||
./prowler -c extraNumber,extraNumber
|
||||
```
|
||||
|
||||
|
||||
## Forensics Ready Checks
|
||||
|
||||
With this group of checks, Prowler looks if each service with logging or audit capabilities has them enabled to ensure all needed evidences are recorded and collected for an eventual digital forensic investigation in case of incident. List of checks part of this group (you can also see all groups with `./prowler -L`). The list of checks can be seen in the group file at:
|
||||
|
||||
[groups/group8_forensics](groups/group8_forensics)
|
||||
|
||||
The `forensics-ready` group of checks uses existing and extra checks. To get a forensics readiness report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g forensics-ready
|
||||
```
|
||||
|
||||
## GDPR Checks
|
||||
|
||||
With this group of checks, Prowler shows result of checks related to GDPR, more information [here](https://github.com/prowler-cloud/prowler/issues/189). The list of checks can be seen in the group file at:
|
||||
|
||||
[groups/group9_gdpr](groups/group9_gdpr)
|
||||
|
||||
The `gdpr` group of checks uses existing and extra checks. To get a GDPR report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g gdpr
|
||||
```
|
||||
|
||||
## AWS FTR Checks
|
||||
|
||||
With this group of checks, Prowler shows result of checks related to the AWS Foundational Technical Review, more information [here](https://apn-checklists.s3.amazonaws.com/foundational/partner-hosted/partner-hosted/CVLHEC5X7.html). The list of checks can be seen in the group file at:
|
||||
|
||||
[groups/group25_ftr](groups/group25_FTR)
|
||||
|
||||
The `ftr` group of checks uses existing and extra checks. To get a AWS FTR report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g ftr
|
||||
```
|
||||
|
||||
## HIPAA Checks
|
||||
|
||||
With this group of checks, Prowler shows results of controls related to the "Security Rule" of the Health Insurance Portability and Accountability Act aka [HIPAA](https://www.hhs.gov/hipaa/for-professionals/security/index.html) as defined in [45 CFR Subpart C - Security Standards for the Protection of Electronic Protected Health Information](https://www.law.cornell.edu/cfr/text/45/part-164/subpart-C) within [PART 160 - GENERAL ADMINISTRATIVE REQUIREMENTS](https://www.law.cornell.edu/cfr/text/45/part-160) and [Subpart A](https://www.law.cornell.edu/cfr/text/45/part-164/subpart-A) and [Subpart C](https://www.law.cornell.edu/cfr/text/45/part-164/subpart-C) of PART 164 - SECURITY AND PRIVACY
|
||||
|
||||
More information on the original PR is [here](https://github.com/prowler-cloud/prowler/issues/227).
|
||||
|
||||
### Note on Business Associate Addendum's (BAA)
|
||||
|
||||
Under the HIPAA regulations, cloud service providers (CSPs) such as AWS are considered business associates. The Business Associate Addendum (BAA) is an AWS contract that is required under HIPAA rules to ensure that AWS appropriately safeguards protected health information (PHI). The BAA also serves to clarify and limit, as appropriate, the permissible uses and disclosures of PHI by AWS, based on the relationship between AWS and our customers, and the activities or services being performed by AWS. Customers may use any AWS service in an account designated as a HIPAA account, but they should only process, store, and transmit protected health information (PHI) in the HIPAA-eligible services defined in the Business Associate Addendum (BAA). For the latest list of HIPAA-eligible AWS services, see [HIPAA Eligible Services Reference](https://aws.amazon.com/compliance/hipaa-eligible-services-reference/).
|
||||
|
||||
More information on AWS & HIPAA can be found [here](https://aws.amazon.com/compliance/hipaa-compliance/)
|
||||
|
||||
The list of checks showed by this group is as follows, they will be mostly relevant for Subsections [164.306 Security standards: General rules](https://www.law.cornell.edu/cfr/text/45/164.306) and [164.312 Technical safeguards](https://www.law.cornell.edu/cfr/text/45/164.312). Prowler is only able to make checks in the spirit of the technical requirements outlined in these Subsections, and cannot cover all procedural controls required. They be found in the group file at:
|
||||
|
||||
[groups/group10_hipaa](groups/group10_hipaa)
|
||||
|
||||
The `hipaa` group of checks uses existing and extra checks. To get a HIPAA report, run this command:
|
||||
|
||||
```sh
|
||||
./prowler -g hipaa
|
||||
```
|
||||
|
||||
## Trust Boundaries Checks
|
||||
|
||||
### Definition and Terms
|
||||
|
||||
The term "trust boundary" is originating from the threat modelling process and the most popular contributor Adam Shostack and author of "Threat Modeling: Designing for Security" defines it as following ([reference](https://adam.shostack.org/uncover.html)):
|
||||
|
||||
> Trust boundaries are perhaps the most subjective of all: these represent the border between trusted and untrusted elements. Trust is complex. You might trust your mechanic with your car, your dentist with your teeth, and your banker with your money, but you probably don't trust your dentist to change your spark plugs.
|
||||
|
||||
AWS is made to be flexible for service links within and between different AWS accounts, we all know that.
|
||||
|
||||
This group of checks helps to analyse a particular AWS account (subject) on existing links to other AWS accounts across various AWS services, in order to identify untrusted links.
|
||||
|
||||
### Run
|
||||
To give it a quick shot just call:
|
||||
|
||||
```sh
|
||||
./prowler -g trustboundaries
|
||||
```
|
||||
|
||||
### Scenarios
|
||||
|
||||
Currently, this check group supports two different scenarios:
|
||||
|
||||
1. Single account environment: no action required, the configuration is happening automatically for you.
|
||||
2. Multi account environment: in case you environment has multiple trusted and known AWS accounts you maybe want to append them manually to [groups/group16_trustboundaries](groups/group16_trustboundaries) as a space separated list into `GROUP_TRUSTBOUNDARIES_TRUSTED_ACCOUNT_IDS` variable, then just run prowler.
|
||||
|
||||
### Coverage
|
||||
|
||||
Current coverage of Amazon Web Service (AWS) taken from [here](https://docs.aws.amazon.com/whitepapers/latest/aws-overview/introduction.html):
|
||||
| Topic | Service | Trust Boundary |
|
||||
|---------------------------------|------------|---------------------------------------------------------------------------|
|
||||
| Networking and Content Delivery | Amazon VPC | VPC endpoints connections ([extra786](checks/check_extra786)) |
|
||||
| | | VPC endpoints allowlisted principals ([extra787](checks/check_extra787)) |
|
||||
|
||||
All ideas or recommendations to extend this group are very welcome [here](https://github.com/prowler-cloud/prowler/issues/new/choose).
|
||||
|
||||
### Detailed Explanation of the Concept
|
||||
|
||||
The diagrams depict two common scenarios, single account and multi account environments.
|
||||
Every circle represents one AWS account.
|
||||
The dashed line represents the trust boundary, that separates trust and untrusted AWS accounts.
|
||||
The arrow simply describes the direction of the trust, however the data can potentially flow in both directions.
|
||||
|
||||
Single Account environment assumes that only the AWS account subject to this analysis is trusted. However, there is a chance that two VPCs are existing within that one AWS account which are still trusted as a self reference.
|
||||

|
||||
|
||||
Multi Account environments assumes a minimum of two trusted or known accounts. For this particular example all trusted and known accounts will be tested. Therefore `GROUP_TRUSTBOUNDARIES_TRUSTED_ACCOUNT_IDS` variable in [groups/group16_trustboundaries](groups/group16_trustboundaries) should include all trusted accounts Account #A, Account #B, Account #C, and Account #D in order to finally raise Account #E and Account #F for being untrusted or unknown.
|
||||

|
||||
|
||||
## Custom Checks
|
||||
Using `./prowler -c extra9999 -a` you can build your own on-the-fly custom check by specifying the AWS CLI command to execute.
|
||||
> Omit the "aws" command and only use its parameters within quotes and do not nest quotes in the aws parameter, --output text is already included in the check.
|
||||
>
|
||||
Here is an example of a check to find SGs with inbound port 80:
|
||||
|
||||
```sh
|
||||
./prowler -c extra9999 -a 'ec2 describe-security-groups --filters Name=ip-permission.to-port,Values=80 --query SecurityGroups[*].GroupId[]]'
|
||||
```
|
||||
|
||||
In order to add any new check feel free to create a new extra check in the extras group or other group. To do so, you will need to follow these steps:
|
||||
|
||||
1. Follow structure in file `checks/check_sample`
|
||||
2. Name your check with a number part of an existing group or a new one
|
||||
3. Save changes and run it as `./prowler -c extraNN`
|
||||
4. Send me a pull request! :)
|
||||
|
||||
## Add Custom Groups
|
||||
|
||||
1. Follow structure in file `groups/groupN_sample`
|
||||
1. Name your group with a non existing number
|
||||
1. Save changes and run it as `./prowler -g extraNN`
|
||||
1. Send me a pull request! :)
|
||||
|
||||
- You can also create a group with only the checks that you want to perform in your company, for instance a group named `group9_mycompany` with only the list of checks that you care or your particular compliance applies.
|
||||
|
||||
## Third Party Integrations
|
||||
|
||||
### Telegram
|
||||
|
||||
Javier Pecete has done an awesome job integrating Prowler with Telegram, you have more details here <https://github.com/i4specete/ServerTelegramBot>
|
||||
|
||||
### Cloud Security Suite
|
||||
|
||||
The guys of SecurityFTW have added Prowler in their Cloud Security Suite along with other cool security tools <https://github.com/SecurityFTW/cs-suite>
|
||||
|
||||
## License
|
||||
# 📃 License
|
||||
|
||||
Prowler is licensed as Apache License 2.0 as specified in each file. You may obtain a copy of the License at
|
||||
<http://www.apache.org/licenses/LICENSE-2.0>
|
||||
|
||||
**I'm not related anyhow with CIS organization, I just write and maintain Prowler to help companies over the world to make their cloud infrastructure more secure.**
|
||||
|
||||
If you want to contact me visit <https://blyx.com/contact> or follow me on Twitter <https://twitter.com/prowler-cloud> my DMs are open.
|
||||
|
||||
23
SECURITY.md
Normal file
23
SECURITY.md
Normal file
@@ -0,0 +1,23 @@
|
||||
# Security Policy
|
||||
|
||||
## Software Security
|
||||
As an **AWS Partner** and we have passed the [AWS Foundation Technical Review (FTR)](https://aws.amazon.com/partners/foundational-technical-review/) and we use the following tools and automation to make sure our code is secure and dependencies up-to-dated:
|
||||
|
||||
- `bandit` for code security review.
|
||||
- `safety` and `dependabot` for dependencies.
|
||||
- `hadolint` and `dockle` for our containers security.
|
||||
- `snyk` in Docker Hub.
|
||||
- `clair` in Amazon ECR.
|
||||
- `vulture`, `flake8`, `black` and `pylint` for formatting and best practices.
|
||||
|
||||
## Reporting a Vulnerability
|
||||
|
||||
If you would like to report a vulnerability or have a security concern regarding Prowler Open Source or ProwlerPro service, please submit the information by contacting to help@prowler.pro.
|
||||
|
||||
The information you share with Verica as part of this process is kept confidential within Verica and the Prowler team. We will only share this information with a third party if the vulnerability you report is found to affect a third-party product, in which case we will share this information with the third-party product's author or manufacturer. Otherwise, we will only share this information as permitted by you.
|
||||
|
||||
We will review the submitted report, and assign it a tracking number. We will then respond to you, acknowledging receipt of the report, and outline the next steps in the process.
|
||||
|
||||
You will receive a non-automated response to your initial contact within 24 hours, confirming receipt of your reported vulnerability.
|
||||
|
||||
We will coordinate public notification of any validated vulnerability with you. Where possible, we prefer that our respective public disclosures be posted simultaneously.
|
||||
@@ -1,29 +0,0 @@
|
||||
# Each line is a (checkid:item) tuple
|
||||
|
||||
# Example: Will not consider a myignoredbucket failures as full failure. (Still printed as a warning)
|
||||
check26:myignoredbucket
|
||||
|
||||
# Note that by default, this searches for the string appearing *anywhere* in the resource name.
|
||||
# For example:
|
||||
# extra718:ci-logs # Will block bucket "ci-logs" AND ALSO bucket "ci-logs-replica"
|
||||
# extra718:logs # Will block EVERY BUCKET containing the string "logs"
|
||||
|
||||
# line starting with # are ignored as comments
|
||||
# add a line per resource as here:
|
||||
#<checkid1>:<resource to ignore 1>
|
||||
#<checkid1>:<resource to ignore 2>
|
||||
# checkid2
|
||||
#<checkid2>:<resource to ignore 1>
|
||||
|
||||
# REGEXES
|
||||
# This allowlist works with regexes (ERE, the same style of regex as grep -E and bash's =~ use)
|
||||
# therefore:
|
||||
# extra718:[[:alnum:]]+-logs # will ignore all buckets containing the terms ci-logs, qa-logs, etc.
|
||||
|
||||
# EXAMPLE: CONTROL TOWER
|
||||
# When using Control Tower, guardrails prevent access to certain protected resources. The allowlist
|
||||
# below ensures that warnings instead of errors are reported for the affected resources.
|
||||
#extra734:aws-controltower-logs-[[:digit:]]+-[[:alpha:]\-]+
|
||||
#extra734:aws-controltower-s3-access-logs-[[:digit:]]+-[[:alpha:]\-]+
|
||||
#extra764:aws-controltower-logs-[[:digit:]]+-[[:alpha:]\-]+
|
||||
#extra764:aws-controltower-s3-access-logs-[[:digit:]]+-[[:alpha:]\-]+
|
||||
@@ -1,6 +0,0 @@
|
||||
# You can add a comma seperated list of checks like this:
|
||||
check11,check12
|
||||
extra72 # You can also use newlines for each check
|
||||
check13 # This way allows you to add inline comments
|
||||
# Both of these can be combined if you have a standard list and want to add
|
||||
# inline comments for other checks.
|
||||
@@ -1,51 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check11="1.1"
|
||||
CHECK_TITLE_check11="[check11] Avoid the use of the root account"
|
||||
CHECK_SCORED_check11="SCORED"
|
||||
CHECK_CIS_LEVEL_check11="LEVEL1"
|
||||
CHECK_SEVERITY_check11="High"
|
||||
CHECK_ASFF_TYPE_check11="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check101="check11"
|
||||
CHECK_SERVICENAME_check11="iam"
|
||||
CHECK_RISK_check11='The "root" account has unrestricted access to all resources in the AWS account. It is highly recommended that the use of this account be avoided.'
|
||||
CHECK_REMEDIATION_check11='Follow the remediation instructions of the Ensure IAM policies are attached only to groups or roles recommendation.'
|
||||
CHECK_DOC_check11='http://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html'
|
||||
CHECK_CAF_EPIC_check11='IAM'
|
||||
|
||||
check11(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
# "Avoid the use of the root account (Scored)."
|
||||
MAX_DAYS=-1
|
||||
last_login_dates=$(cat $TEMP_REPORT_FILE | awk -F, '{ print $1,$5,$11,$16 }' | grep '<root_account>' | cut -d' ' -f2,3,4)
|
||||
|
||||
failures=0
|
||||
for date in $last_login_dates; do
|
||||
if [[ ${date%T*} =~ ^[0-9]{4}-[0-9]{2}-[0-9]{2}$ ]];then
|
||||
days_not_in_use=$(how_many_days_from_today ${date%T*})
|
||||
if [ "$days_not_in_use" -gt "$MAX_DAYS" ];then
|
||||
failures=1
|
||||
textFail "$REGION: Root user in the account was last accessed ${MAX_DAYS#-} day ago" "$REGION" "root"
|
||||
break
|
||||
fi
|
||||
fi
|
||||
done
|
||||
|
||||
if [[ $failures == 0 ]]; then
|
||||
textPass "$REGION: Root user in the account wasn't accessed in the last ${MAX_DAYS#-} days" "$REGION" "root"
|
||||
fi
|
||||
fi
|
||||
}
|
||||
@@ -1,39 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check110="1.10"
|
||||
CHECK_TITLE_check110="[check110] Ensure IAM password policy prevents password reuse: 24 or greater"
|
||||
CHECK_SCORED_check110="SCORED"
|
||||
CHECK_CIS_LEVEL_check110="LEVEL1"
|
||||
CHECK_SEVERITY_check110="Medium"
|
||||
CHECK_ASFF_TYPE_check110="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check110="check110"
|
||||
CHECK_SERVICENAME_check110="iam"
|
||||
CHECK_RISK_check110='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check110='Ensure "Number of passwords to remember" is set to 24.'
|
||||
CHECK_DOC_check110='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check110='IAM'
|
||||
|
||||
check110(){
|
||||
# "Ensure IAM password policy prevents password reuse: 24 or greater (Scored)"
|
||||
COMMAND110=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --query 'PasswordPolicy.PasswordReusePrevention' --output text 2> /dev/null)
|
||||
if [[ $COMMAND110 ]];then
|
||||
if [[ $COMMAND110 -gt "23" ]];then
|
||||
textPass "$REGION: Password Policy limits reuse" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password Policy has weak reuse requirement (lower than 24)" "$REGION" "password policy"
|
||||
fi
|
||||
else
|
||||
textFail "$REGION: Password Policy missing reuse requirement" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,39 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check111="1.11"
|
||||
CHECK_TITLE_check111="[check111] Ensure IAM password policy expires passwords within 90 days or less"
|
||||
CHECK_SCORED_check111="SCORED"
|
||||
CHECK_CIS_LEVEL_check111="LEVEL1"
|
||||
CHECK_SEVERITY_check111="Medium"
|
||||
CHECK_ASFF_TYPE_check111="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check111="check111"
|
||||
CHECK_SERVICENAME_check111="iam"
|
||||
CHECK_RISK_check111='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check111='Ensure "Password expiration period (in days):" is set to 90 or less.'
|
||||
CHECK_DOC_check111='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check111='IAM'
|
||||
|
||||
check111(){
|
||||
# "Ensure IAM password policy expires passwords within 90 days or less (Scored)"
|
||||
COMMAND111=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --query PasswordPolicy.MaxPasswordAge --output text 2> /dev/null)
|
||||
if [[ $COMMAND111 == [0-9]* ]];then
|
||||
if [[ "$COMMAND111" -le "90" ]];then
|
||||
textPass "$REGION: Password Policy includes expiration (Value: $COMMAND111)" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password expiration is set greater than 90 days" "$REGION" "password policy"
|
||||
fi
|
||||
else
|
||||
textFail "$REGION: Password expiration is not set" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,42 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check112="1.12"
|
||||
CHECK_TITLE_check112="[check112] Ensure no root account access key exists"
|
||||
CHECK_SCORED_check112="SCORED"
|
||||
CHECK_CIS_LEVEL_check112="LEVEL1"
|
||||
CHECK_SEVERITY_check112="Critical"
|
||||
CHECK_ASFF_TYPE_check112="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check112="check112"
|
||||
CHECK_SERVICENAME_check112="iam"
|
||||
CHECK_RISK_check112='The root account is the most privileged user in an AWS account. AWS Access Keys provide programmatic access to a given AWS account. It is recommended that all access keys associated with the root account be removed. Removing access keys associated with the root account limits vectors by which the account can be compromised. Removing the root access keys encourages the creation and use of role based accounts that are least privileged.'
|
||||
CHECK_REMEDIATION_check112='Use the credential report to that the user and ensure the access_key_1_active and access_key_2_active fields are set to FALSE .'
|
||||
CHECK_DOC_check112='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html'
|
||||
CHECK_CAF_EPIC_check112='IAM'
|
||||
|
||||
check112(){
|
||||
# "Ensure no root account access key exists (Scored)"
|
||||
# ensure the access_key_1_active and access_key_2_active fields are set to FALSE.
|
||||
ROOTKEY1=$(cat $TEMP_REPORT_FILE |grep root_account|awk -F',' '{ print $9 }')
|
||||
ROOTKEY2=$(cat $TEMP_REPORT_FILE |grep root_account|awk -F',' '{ print $14 }')
|
||||
if [ "$ROOTKEY1" == "false" ];then
|
||||
textPass "$REGION: No access key 1 found for root" "$REGION" "root access key1"
|
||||
else
|
||||
textFail "$REGION: Found access key 1 for root" "$REGION" "root access key1"
|
||||
fi
|
||||
if [ "$ROOTKEY2" == "false" ];then
|
||||
textPass "$REGION: No access key 2 found for root" "$REGION" "root access key2"
|
||||
else
|
||||
textFail "$REGION: Found access key 2 for root" "$REGION" "root access key2"
|
||||
fi
|
||||
}
|
||||
@@ -1,39 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check113="1.13"
|
||||
CHECK_TITLE_check113="[check113] Ensure MFA is enabled for the root account"
|
||||
CHECK_SCORED_check113="SCORED"
|
||||
CHECK_CIS_LEVEL_check113="LEVEL1"
|
||||
CHECK_SEVERITY_check113="Critical"
|
||||
CHECK_ASFF_TYPE_check113="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check113="check113"
|
||||
CHECK_SERVICENAME_check113="iam"
|
||||
CHECK_RISK_check113='The root account is the most privileged user in an AWS account. MFA adds an extra layer of protection on top of a user name and password. With MFA enabled when a user signs in to an AWS website they will be prompted for their user name and password as well as for an authentication code from their AWS MFA device. When virtual MFA is used for root accounts it is recommended that the device used is NOT a personal device but rather a dedicated mobile device (tablet or phone) that is managed to be kept charged and secured independent of any individual personal devices. ("non-personal virtual MFA") This lessens the risks of losing access to the MFA due to device loss / trade-in or if the individual owning the device is no longer employed at the company.'
|
||||
CHECK_REMEDIATION_check113='Using IAM console navigate to Dashboard and expand Activate MFA on your root account.'
|
||||
CHECK_DOC_check113='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_root-user.html#id_root-user_manage_mfa'
|
||||
CHECK_CAF_EPIC_check113='IAM'
|
||||
|
||||
check113(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
# "Ensure MFA is enabled for the root account (Scored)"
|
||||
COMMAND113=$($AWSCLI iam get-account-summary $PROFILE_OPT --region $REGION --output json --query 'SummaryMap.AccountMFAEnabled')
|
||||
if [ "$COMMAND113" == "1" ]; then
|
||||
textPass "$REGION: Virtual MFA is enabled for root" "$REGION" "MFA"
|
||||
else
|
||||
textFail "$REGION: MFA is not ENABLED for root account" "$REGION" "MFA"
|
||||
fi
|
||||
fi
|
||||
}
|
||||
@@ -1,44 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check114="1.14"
|
||||
CHECK_TITLE_check114="[check114] Ensure hardware MFA is enabled for the root account"
|
||||
CHECK_SCORED_check114="SCORED"
|
||||
CHECK_CIS_LEVEL_check114="LEVEL2"
|
||||
CHECK_SEVERITY_check114="Critical"
|
||||
CHECK_ASFF_TYPE_check114="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check114="check114"
|
||||
CHECK_SERVICENAME_check114="iam"
|
||||
CHECK_RISK_check114='The root account is the most privileged user in an AWS account. MFA adds an extra layer of protection on top of a user name and password. With MFA enabled when a user signs in to an AWS website they will be prompted for their user name and password as well as for an authentication code from their AWS MFA device. For Level 2 it is recommended that the root account be protected with a hardware MFA.'
|
||||
CHECK_REMEDIATION_check114='Using IAM console navigate to Dashboard and expand Activate MFA on your root account.'
|
||||
CHECK_DOC_check114='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_root-user.html#id_root-user_manage_mfa'
|
||||
CHECK_CAF_EPIC_check114='IAM'
|
||||
|
||||
check114(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
# "Ensure hardware MFA is enabled for the root account (Scored)"
|
||||
COMMAND113=$($AWSCLI iam get-account-summary $PROFILE_OPT --region $REGION --output json --query 'SummaryMap.AccountMFAEnabled')
|
||||
if [ "$COMMAND113" == "1" ]; then
|
||||
COMMAND114=$($AWSCLI iam list-virtual-mfa-devices $PROFILE_OPT --region $REGION --output text --assignment-status Assigned --query 'VirtualMFADevices[*].[SerialNumber]' | grep "^arn:${AWS_PARTITION}:iam::[0-9]\{12\}:mfa/root-account-mfa-device$")
|
||||
if [[ "$COMMAND114" ]]; then
|
||||
textFail "$REGION: Only Virtual MFA is enabled for root" "$REGION" "MFA"
|
||||
else
|
||||
textPass "$REGION: Hardware MFA is enabled for root" "$REGION" "MFA"
|
||||
fi
|
||||
else
|
||||
textFail "$REGION: MFA is not ENABLED for root account" "$REGION" "MFA"
|
||||
fi
|
||||
fi
|
||||
}
|
||||
@@ -1,34 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check115="1.15"
|
||||
CHECK_TITLE_check115="[check115] Ensure security questions are registered in the AWS account"
|
||||
CHECK_SCORED_check115="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_check115="LEVEL1"
|
||||
CHECK_SEVERITY_check115="Medium"
|
||||
CHECK_ASFF_TYPE_check115="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check115="check115"
|
||||
CHECK_SERVICENAME_check115="support"
|
||||
CHECK_RISK_check115='The AWS support portal allows account owners to establish security questions that can be used to authenticate individuals calling AWS customer service for support. It is recommended that security questions be established. When creating a new AWS account a default super user is automatically created. This account is referred to as the "root" account. It is recommended that the use of this account be limited and highly controlled. During events in which the root password is no longer accessible or the MFA token associated with root is lost/destroyed it is possible through authentication using secret questions and associated answers to recover root login access.'
|
||||
CHECK_REMEDIATION_check115='Login as root account and from My Account configure Security questions.'
|
||||
CHECK_DOC_check115='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys_retrieve.html'
|
||||
CHECK_CAF_EPIC_check115='IAM'
|
||||
|
||||
check115(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
# "Ensure security questions are registered in the AWS account (Not Scored)"
|
||||
textInfo "${REGION}: No command available for check 1.15. Login to the AWS Console as root & click on the Account. Name -> My Account -> Configure Security Challenge Questions."
|
||||
fi
|
||||
}
|
||||
@@ -1,49 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check116="1.16"
|
||||
CHECK_TITLE_check116="[check116] Ensure IAM policies are attached only to groups or roles"
|
||||
CHECK_SCORED_check116="SCORED"
|
||||
CHECK_CIS_LEVEL_check116="LEVEL1"
|
||||
CHECK_SEVERITY_check116="Low"
|
||||
CHECK_ASFF_TYPE_check116="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check116="AwsIamUser"
|
||||
CHECK_ALTERNATE_check116="check116"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check116="ens-op.acc.3.aws.iam.1"
|
||||
CHECK_SERVICENAME_check116="iam"
|
||||
CHECK_RISK_check116='By default IAM users; groups; and roles have no access to AWS resources. IAM policies are the means by which privileges are granted to users; groups; or roles. It is recommended that IAM policies be applied directly to groups and roles but not users. Assigning privileges at the group or role level reduces the complexity of access management as the number of users grow. Reducing access management complexity may in-turn reduce opportunity for a principal to inadvertently receive or retain excessive privileges.'
|
||||
CHECK_REMEDIATION_check116='Remove any policy attached directly to the user. Use groups or roles instead.'
|
||||
CHECK_DOC_check116='https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html'
|
||||
CHECK_CAF_EPIC_check116='IAM'
|
||||
|
||||
check116(){
|
||||
# "Ensure IAM policies are attached only to groups or roles (Scored)"
|
||||
LIST_USERS=$($AWSCLI iam list-users --query 'Users[*].UserName' --output text $PROFILE_OPT --region $REGION)
|
||||
for user in $LIST_USERS;do
|
||||
USER_ATTACHED_POLICY=$($AWSCLI iam list-attached-user-policies --output text $PROFILE_OPT --region $REGION --user-name $user)
|
||||
USER_INLINE_POLICY=$($AWSCLI iam list-user-policies --output text $PROFILE_OPT --region $REGION --user-name $user)
|
||||
if [[ $USER_ATTACHED_POLICY ]] || [[ $USER_INLINE_POLICY ]]
|
||||
then
|
||||
if [[ $USER_ATTACHED_POLICY ]]
|
||||
then
|
||||
textFail "$REGION: $user has managed policy directly attached" "$REGION" "$user"
|
||||
fi
|
||||
if [[ $USER_INLINE_POLICY ]]
|
||||
then
|
||||
textFail "$REGION: $user has inline policy directly attached" "$REGION" "$user"
|
||||
fi
|
||||
else
|
||||
textPass "$REGION: No policies attached to user $user" "$REGION" "$user"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check117="1.17"
|
||||
CHECK_TITLE_check117="[check117] Maintain current contact details"
|
||||
CHECK_SCORED_check117="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_check117="LEVEL1"
|
||||
CHECK_SEVERITY_check117="Medium"
|
||||
CHECK_ASFF_TYPE_check117="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check117="check117"
|
||||
CHECK_SERVICENAME_check117="support"
|
||||
CHECK_RISK_check117='Ensure contact email and telephone details for AWS accounts are current and map to more than one individual in your organization. An AWS account supports a number of contact details; and AWS will use these to contact the account owner if activity judged to be in breach of Acceptable Use Policy. If an AWS account is observed to be behaving in a prohibited or suspicious manner; AWS will attempt to contact the account owner by email and phone using the contact details listed. If this is unsuccessful and the account behavior needs urgent mitigation; proactive measures may be taken; including throttling of traffic between the account exhibiting suspicious behavior and the AWS API endpoints and the Internet. This will result in impaired service to and from the account in question.'
|
||||
CHECK_REMEDIATION_check117='Using the Billing and Cost Management console complete contact details.'
|
||||
CHECK_DOC_check117='https://docs.aws.amazon.com/awsaccountbilling/latest/aboutv2/manage-account-payment.html#contact-info'
|
||||
CHECK_CAF_EPIC_check117='IAM'
|
||||
|
||||
check117(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
# "Maintain current contact details (Scored)"
|
||||
# No command available
|
||||
textInfo "No command available for check 1.17. See section 1.17 on the CIS Benchmark guide for details."
|
||||
fi
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check118="1.18"
|
||||
CHECK_TITLE_check118="[check118] Ensure security contact information is registered"
|
||||
CHECK_SCORED_check118="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_check118="LEVEL1"
|
||||
CHECK_SEVERITY_check118="Medium"
|
||||
CHECK_ASFF_TYPE_check118="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check118="check118"
|
||||
CHECK_SERVICENAME_check118="support"
|
||||
CHECK_RISK_check118='AWS provides customers with the option of specifying the contact information for accounts security team. It is recommended that this information be provided. Specifying security-specific contact information will help ensure that security advisories sent by AWS reach the team in your organization that is best equipped to respond to them.'
|
||||
CHECK_REMEDIATION_check118='Go to the My Account section and complete alternate contacts.'
|
||||
CHECK_DOC_check118='https://docs.aws.amazon.com/awsaccountbilling/latest/aboutv2/manage-account-payment.html'
|
||||
CHECK_CAF_EPIC_check118='IAM'
|
||||
|
||||
check118(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
# "Ensure security contact information is registered (Scored)"
|
||||
# No command available
|
||||
textInfo "No command available for check 1.18. See section 1.18 on the CIS Benchmark guide for details."
|
||||
fi
|
||||
}
|
||||
@@ -1,54 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check119="1.19"
|
||||
CHECK_TITLE_check119="[check119] Ensure IAM instance roles are used for AWS resource access from instances"
|
||||
CHECK_SCORED_check119="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_check119="LEVEL2"
|
||||
CHECK_SEVERITY_check119="Medium"
|
||||
CHECK_ASFF_TYPE_check119="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check119="AwsEc2Instance"
|
||||
CHECK_ALTERNATE_check119="check119"
|
||||
CHECK_SERVICENAME_check119="ec2"
|
||||
CHECK_RISK_check119='AWS access from within AWS instances can be done by either encoding AWS keys into AWS API calls or by assigning the instance to a role which has an appropriate permissions policy for the required access. AWS IAM roles reduce the risks associated with sharing and rotating credentials that can be used outside of AWS itself. If credentials are compromised; they can be used from outside of the AWS account.'
|
||||
CHECK_REMEDIATION_check119='IAM roles can only be associated at the launch of an instance. To remediate an instance to add it to a role you must create or re-launch a new instance. (Check for external dependencies on its current private ip or public addresses).'
|
||||
CHECK_DOC_check119='http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_switch-role-ec2.html'
|
||||
CHECK_CAF_EPIC_check119='IAM'
|
||||
|
||||
check119(){
|
||||
for regx in $REGIONS; do
|
||||
EC2_DATA=$($AWSCLI ec2 describe-instances $PROFILE_OPT --region $regx --query 'Reservations[].Instances[].[InstanceId, IamInstanceProfile.Arn, State.Name]' --output json 2>&1)
|
||||
if [[ $(echo "$EC2_DATA" | grep UnauthorizedOperation) ]]; then
|
||||
textInfo "$regx: Unauthorized Operation error trying to describe instances" "$regx"
|
||||
continue
|
||||
else
|
||||
EC2_DATA=$(echo $EC2_DATA | jq '.[]|{InstanceId: .[0], ProfileArn: .[1], StateName: .[2]}')
|
||||
INSTANCE_LIST=$(echo $EC2_DATA | jq -r '.InstanceId')
|
||||
fi
|
||||
if [[ $INSTANCE_LIST ]]; then
|
||||
for instance in $INSTANCE_LIST; do
|
||||
STATE_NAME=$(echo $EC2_DATA | jq -r --arg i "$instance" 'select(.InstanceId==$i)|.StateName')
|
||||
if [[ $STATE_NAME != "terminated" && $STATE_NAME != "shutting-down" ]]; then
|
||||
PROFILEARN=$(echo $EC2_DATA | jq -r --arg i "$instance" 'select(.InstanceId==$i)|.ProfileArn')
|
||||
if [[ $PROFILEARN == "null" ]]; then
|
||||
textFail "$regx: Instance $instance not associated with an instance role" "$regx" "$instance"
|
||||
else
|
||||
textPass "$regx: Instance $instance associated with role ${PROFILEARN##*/}" "$regx" "$instance"
|
||||
fi
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: No EC2 instances found" "$regx" "$instance"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,44 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check12="1.2"
|
||||
CHECK_TITLE_check12="[check12] Ensure multi-factor authentication (MFA) is enabled for all IAM users that have a console password"
|
||||
CHECK_SCORED_check12="SCORED"
|
||||
CHECK_CIS_LEVEL_check12="LEVEL1"
|
||||
CHECK_SEVERITY_check12="High"
|
||||
CHECK_ASFF_TYPE_check12="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check12="AwsIamUser"
|
||||
CHECK_ALTERNATE_check102="check12"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check12="ens-op.acc.5.aws.iam.1"
|
||||
CHECK_SERVICENAME_check12="iam"
|
||||
CHECK_RISK_check12='Unauthorized access to this critical account if password is not secure or it is disclosed in any way.'
|
||||
CHECK_REMEDIATION_check12='Enable MFA for root account. MFA is a simple best practice that adds an extra layer of protection on top of your user name and password. Recommended to use hardware keys over virtual MFA.'
|
||||
CHECK_DOC_check12='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_mfa_enable_virtual.html'
|
||||
CHECK_CAF_EPIC_check12='IAM'
|
||||
|
||||
check12(){
|
||||
# "Ensure multi-factor authentication (MFA) is enabled for all IAM users that have a console password (Scored)"
|
||||
# List users with password enabled
|
||||
COMMAND12_LIST_USERS_WITH_PASSWORD_ENABLED=$(cat $TEMP_REPORT_FILE|awk -F, '{ print $1,$4 }' |grep 'true$' | awk '{ print $1 }')
|
||||
COMMAND12=$(
|
||||
for i in $COMMAND12_LIST_USERS_WITH_PASSWORD_ENABLED; do
|
||||
cat $TEMP_REPORT_FILE|awk -F, '{ print $1,$8 }' |grep "^$i " |grep false | awk '{ print $1 }'
|
||||
done)
|
||||
if [[ $COMMAND12 ]]; then
|
||||
for u in $COMMAND12; do
|
||||
textFail "$REGION: User $u has Password enabled but MFA disabled" "$REGION" "$u"
|
||||
done
|
||||
else
|
||||
textPass "$REGION: No users found with Password enabled and MFA disabled" "$REGION" "$u"
|
||||
fi
|
||||
}
|
||||
@@ -1,49 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check120="1.20"
|
||||
CHECK_TITLE_check120="[check120] Ensure a support role has been created to manage incidents with AWS Support"
|
||||
CHECK_SCORED_check120="SCORED"
|
||||
CHECK_CIS_LEVEL_check120="LEVEL1"
|
||||
CHECK_SEVERITY_check120="Medium"
|
||||
CHECK_ASFF_TYPE_check120="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check120="AwsIamRole"
|
||||
CHECK_ALTERNATE_check120="check120"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check120="ens-op.acc.1.aws.iam.4"
|
||||
CHECK_SERVICENAME_check120="iam"
|
||||
CHECK_RISK_check120='AWS provides a support center that can be used for incident notification and response; as well as technical support and customer services. Create an IAM Role to allow authorized users to manage incidents with AWS Support.'
|
||||
CHECK_REMEDIATION_check120='Create an IAM role for managing incidents with AWS.'
|
||||
CHECK_DOC_check120='https://docs.aws.amazon.com/awssupport/latest/user/using-service-linked-roles-sup.html'
|
||||
CHECK_CAF_EPIC_check120='IAM'
|
||||
|
||||
check120(){
|
||||
# "Ensure a support role has been created to manage incidents with AWS Support (Scored)"
|
||||
SUPPORTPOLICYARN=$($AWSCLI iam list-policies --query "Policies[?PolicyName == 'AWSSupportAccess'].Arn" $PROFILE_OPT --region $REGION --output text)
|
||||
if [[ $SUPPORTPOLICYARN ]];then
|
||||
for policyarn in $SUPPORTPOLICYARN;do
|
||||
POLICYROLES=$($AWSCLI iam list-entities-for-policy --policy-arn $policyarn $PROFILE_OPT --region $REGION --output text | awk -F$'\t' '{ print $3 }')
|
||||
if [[ $POLICYROLES ]];then
|
||||
for name in $POLICYROLES; do
|
||||
textPass "$REGION: Support Policy attached to $name" "$REGION" "$name"
|
||||
done
|
||||
# for user in $(echo "$POLICYUSERS" | grep UserName | cut -d'"' -f4) ; do
|
||||
# textInfo "User $user has support access via $policyarn"
|
||||
# done
|
||||
else
|
||||
textFail "$REGION: Support Policy not applied to any Role" "$REGION" "$name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textFail "$REGION: No Support Policy found" "$REGION" "$name"
|
||||
fi
|
||||
}
|
||||
@@ -1,54 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check121="1.21"
|
||||
CHECK_TITLE_check121="[check121] Do not setup access keys during initial user setup for all IAM users that have a console password"
|
||||
CHECK_SCORED_check121="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_check121="LEVEL1"
|
||||
CHECK_SEVERITY_check121="Medium"
|
||||
CHECK_ASFF_TYPE_check121="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check121="AwsIamUser"
|
||||
CHECK_ALTERNATE_check121="check121"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check121="ens-op.acc.1.aws.iam.5"
|
||||
CHECK_SERVICENAME_check121="iam"
|
||||
CHECK_RISK_check121='AWS console defaults the checkbox for creating access keys to enabled. This results in many access keys being generated unnecessarily. In addition to unnecessary credentials; it also generates unnecessary management work in auditing and rotating these keys. Requiring that additional steps be taken by the user after their profile has been created will give a stronger indication of intent that access keys are (a) necessary for their work and (b) once the access key is established on an account that the keys may be in use somewhere in the organization.'
|
||||
CHECK_REMEDIATION_check121='From the IAM console: generate credential report and disable not required keys.'
|
||||
CHECK_DOC_check121='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html'
|
||||
CHECK_CAF_EPIC_check121='IAM'
|
||||
|
||||
check121(){
|
||||
# "Do not setup access keys during initial user setup for all IAM users that have a console password (Not Scored)"
|
||||
LIST_USERS=$($AWSCLI iam list-users --query 'Users[*].UserName' --output text $PROFILE_OPT --region $REGION)
|
||||
# List of USERS with KEY1 last_used_date as N/A
|
||||
LIST_USERS_KEY1_NA=$(for user in $LIST_USERS; do grep "^${user}," $TEMP_REPORT_FILE|awk -F, '{ print $1,$11 }'|grep N/A |awk '{ print $1 }'; done)
|
||||
# List of USERS with KEY1 active, last_used_date as N/A and have a console password
|
||||
LIST_USERS_KEY1_ACTIVE=$(for user in $LIST_USERS_KEY1_NA; do grep "^${user}," $TEMP_REPORT_FILE|awk -F, '{ print $1,$4,$9 }'|grep "true true$"|awk '{ print $1 }'|sed 's/[[:blank:]]+/,/g' ; done)
|
||||
if [[ $LIST_USERS_KEY1_ACTIVE ]]; then
|
||||
for user in $LIST_USERS_KEY1_ACTIVE; do
|
||||
textFail "$REGION: User $user has never used access key 1" "$REGION" "$user"
|
||||
done
|
||||
else
|
||||
textPass "$REGION: No users found with access key 1 never used" "$REGION" "$user"
|
||||
fi
|
||||
# List of USERS with KEY2 last_used_date as N/A
|
||||
LIST_USERS_KEY2_NA=$(for user in $LIST_USERS; do grep "^${user}," $TEMP_REPORT_FILE|awk -F, '{ print $1,$16 }'|grep N/A |awk '{ print $1 }' ; done)
|
||||
# List of USERS with KEY2 active, last_used_date as N/A and have a console password
|
||||
LIST_USERS_KEY2_ACTIVE=$(for user in $LIST_USERS_KEY2_NA; do grep "^${user}," $TEMP_REPORT_FILE|awk -F, '{ print $1,$4,$14 }'|grep "true true$" |awk '{ print $1 }' ; done)
|
||||
if [[ $LIST_USERS_KEY2_ACTIVE ]]; then
|
||||
for user in $LIST_USERS_KEY2_ACTIVE; do
|
||||
textFail "$REGION: User $user has never used access key 2" "$REGION" "$user"
|
||||
done
|
||||
else
|
||||
textPass "$REGION: No users found with access key 2 never used" "$REGION" "$user"
|
||||
fi
|
||||
}
|
||||
@@ -1,50 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check122="1.22"
|
||||
CHECK_TITLE_check122="[check122] Ensure IAM policies that allow full \"*:*\" administrative privileges are not created"
|
||||
CHECK_SCORED_check122="SCORED"
|
||||
CHECK_CIS_LEVEL_check122="LEVEL1"
|
||||
CHECK_SEVERITY_check122="Medium"
|
||||
CHECK_ASFF_TYPE_check122="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check122="AwsIamPolicy"
|
||||
CHECK_ALTERNATE_check122="check122"
|
||||
CHECK_SERVICENAME_check122="iam"
|
||||
CHECK_RISK_check122='IAM policies are the means by which privileges are granted to users; groups; or roles. It is recommended and considered a standard security advice to grant least privilege—that is; granting only the permissions required to perform a task. Determine what users need to do and then craft policies for them that let the users perform only those tasks instead of allowing full administrative privileges. Providing full administrative privileges instead of restricting to the minimum set of permissions that the user is required to do exposes the resources to potentially unwanted actions.'
|
||||
CHECK_REMEDIATION_check122='It is more secure to start with a minimum set of permissions and grant additional permissions as necessary; rather than starting with permissions that are too lenient and then trying to tighten them later. List policies an analyze if permissions are the least possible to conduct business activities.'
|
||||
CHECK_DOC_check122='http://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html'
|
||||
CHECK_CAF_EPIC_check122='IAM'
|
||||
|
||||
check122(){
|
||||
# "Ensure IAM policies that allow full \"*:*\" administrative privileges are not created (Scored)"
|
||||
LIST_CUSTOM_POLICIES=$($AWSCLI iam list-policies --output text $PROFILE_OPT --region $REGION --scope Local --query 'Policies[*].[Arn,DefaultVersionId]' | grep -v -e '^None$' | awk -F '\t' '{print $1","$2"\n"}')
|
||||
if [[ $LIST_CUSTOM_POLICIES ]]; then
|
||||
for policy in $LIST_CUSTOM_POLICIES; do
|
||||
POLICY_ARN=$(awk 'BEGIN{FS=OFS=","}{NF--; print}' <<< "${policy}")
|
||||
POLICY_VERSION=$(awk -F ',' '{print $(NF)}' <<< "${policy}")
|
||||
POLICY_WITH_FULL=$($AWSCLI iam get-policy-version --output text --policy-arn $POLICY_ARN --version-id $POLICY_VERSION --query "[PolicyVersion.Document.Statement] | [] | [?Action!=null] | [?Effect == 'Allow' && Resource == '*' && Action == '*']" $PROFILE_OPT --region $REGION)
|
||||
if [[ $POLICY_WITH_FULL ]]; then
|
||||
POLICIES_ALLOW_LIST="$POLICIES_ALLOW_LIST $POLICY_ARN"
|
||||
else
|
||||
textPass "$REGION: Policy ${policy//,/[comma]} that does not allow full \"*:*\" administrative privileges" "${REGION}" "${policy}"
|
||||
fi
|
||||
done
|
||||
if [[ $POLICIES_ALLOW_LIST ]]; then
|
||||
for policy in $POLICIES_ALLOW_LIST; do
|
||||
textFail "$REGION: Policy ${policy//,/[comma]} allows \"*:*\"" "${REGION}" "${policy}"
|
||||
done
|
||||
fi
|
||||
else
|
||||
textPass "$REGION: No custom policies found" "$REGION"
|
||||
fi
|
||||
}
|
||||
@@ -1,31 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check13="1.3"
|
||||
CHECK_TITLE_check13="[check13] Ensure credentials unused for 90 days or greater are disabled"
|
||||
CHECK_SCORED_check13="SCORED"
|
||||
CHECK_CIS_LEVEL_check13="LEVEL1"
|
||||
CHECK_SEVERITY_check13="Medium"
|
||||
CHECK_ASFF_TYPE_check13="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check13="AwsIamUser"
|
||||
CHECK_ALTERNATE_check103="check13"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check13="ens-op.acc.1.aws.iam.3 ens-op.acc.5.aws.iam.4"
|
||||
CHECK_SERVICENAME_check13="iam"
|
||||
CHECK_RISK_check13='AWS IAM users can access AWS resources using different types of credentials (passwords or access keys). It is recommended that all credentials that have been unused in 90 or greater days be removed or deactivated.'
|
||||
CHECK_REMEDIATION_check13='Use the credential report to ensure password_last_changed is less than 90 days ago.'
|
||||
CHECK_DOC_check13='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html'
|
||||
CHECK_CAF_EPIC_check13='IAM'
|
||||
|
||||
check13(){
|
||||
check_creds_used_in_last_days 90
|
||||
}
|
||||
@@ -1,71 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check14="1.4"
|
||||
CHECK_TITLE_check14="[check14] Ensure access keys are rotated every 90 days or less"
|
||||
CHECK_SCORED_check14="SCORED"
|
||||
CHECK_CIS_LEVEL_check14="LEVEL1"
|
||||
CHECK_SEVERITY_check14="Medium"
|
||||
CHECK_ASFF_TYPE_check14="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check14="AwsIamUser"
|
||||
CHECK_ALTERNATE_check104="check14"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check14="ens-op.acc.1.aws.iam.4 ens-op.acc.5.aws.iam.3"
|
||||
CHECK_SERVICENAME_check14="iam"
|
||||
CHECK_RISK_check14='Access keys consist of an access key ID and secret access key which are used to sign programmatic requests that you make to AWS. AWS users need their own access keys to make programmatic calls to AWS from the AWS Command Line Interface (AWS CLI)- Tools for Windows PowerShell- the AWS SDKs- or direct HTTP calls using the APIs for individual AWS services. It is recommended that all access keys be regularly rotated.'
|
||||
CHECK_REMEDIATION_check14='Use the credential report to ensure access_key_X_last_rotated is less than 90 days ago.'
|
||||
CHECK_DOC_check14='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html'
|
||||
CHECK_CAF_EPIC_check14='IAM'
|
||||
|
||||
check14(){
|
||||
# "Ensure access keys are rotated every 90 days or less (Scored)" # also checked by Security Monkey
|
||||
LIST_OF_USERS_WITH_ACCESS_KEY1=$(cat $TEMP_REPORT_FILE| awk -F, '{ print $1, $9 }' |grep "\ true" | awk '{ print $1 }')
|
||||
LIST_OF_USERS_WITH_ACCESS_KEY2=$(cat $TEMP_REPORT_FILE| awk -F, '{ print $1, $14 }' |grep "\ true" | awk '{ print $1 }')
|
||||
C14_NUM_USERS1=0
|
||||
C14_NUM_USERS2=0
|
||||
if [[ $LIST_OF_USERS_WITH_ACCESS_KEY1 ]]; then
|
||||
# textFail "Users with access key 1 older than 90 days:"
|
||||
for user in $LIST_OF_USERS_WITH_ACCESS_KEY1; do
|
||||
# check access key 1
|
||||
DATEROTATED1=$(cat $TEMP_REPORT_FILE | grep -v user_creation_time | grep "^${user},"| awk -F, '{ print $10 }' | grep -v "N/A" | awk -F"T" '{ print $1 }')
|
||||
HOWOLDER=$(how_older_from_today $DATEROTATED1)
|
||||
|
||||
if [ $HOWOLDER -gt "90" ];then
|
||||
textFail "$REGION: $user has not rotated access key 1 in over 90 days" "$REGION" "$user"
|
||||
C14_NUM_USERS1=$(expr $C14_NUM_USERS1 + 1)
|
||||
fi
|
||||
done
|
||||
if [[ $C14_NUM_USERS1 -eq 0 ]]; then
|
||||
textPass "$REGION: No users with access key 1 older than 90 days" "$REGION" "$user"
|
||||
fi
|
||||
else
|
||||
textPass "$REGION: No users with access key 1" "$REGION" "$user"
|
||||
fi
|
||||
|
||||
if [[ $LIST_OF_USERS_WITH_ACCESS_KEY2 ]]; then
|
||||
# textFail "Users with access key 2 older than 90 days:"
|
||||
for user in $LIST_OF_USERS_WITH_ACCESS_KEY2; do
|
||||
# check access key 2
|
||||
DATEROTATED2=$(cat $TEMP_REPORT_FILE | grep -v user_creation_time | grep "^${user},"| awk -F, '{ print $15 }' | grep -v "N/A" | awk -F"T" '{ print $1 }')
|
||||
HOWOLDER=$(how_older_from_today $DATEROTATED2)
|
||||
if [ $HOWOLDER -gt "90" ];then
|
||||
textFail "$REGION: $user has not rotated access key 2 in over 90 days" "$REGION" "$user"
|
||||
C14_NUM_USERS2=$(expr $C14_NUM_USERS2 + 1)
|
||||
fi
|
||||
done
|
||||
if [[ $C14_NUM_USERS2 -eq 0 ]]; then
|
||||
textPass "$REGION: No users with access key 2 older than 90 days" "$REGION" "$user"
|
||||
fi
|
||||
else
|
||||
textPass "$REGION: No users with access key 2" "$REGION" "$user"
|
||||
fi
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check15="1.5"
|
||||
CHECK_TITLE_check15="[check15] Ensure IAM password policy requires at least one uppercase letter"
|
||||
CHECK_SCORED_check15="SCORED"
|
||||
CHECK_CIS_LEVEL_check15="LEVEL1"
|
||||
CHECK_SEVERITY_check15="Medium"
|
||||
CHECK_ASFF_TYPE_check15="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check105="check15"
|
||||
CHECK_SERVICENAME_check15="iam"
|
||||
CHECK_RISK_check15='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check15='Ensure "Requires at least one uppercase letter" is checked under "Password Policy".'
|
||||
CHECK_DOC_check15='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check15='IAM'
|
||||
|
||||
check15(){
|
||||
# "Ensure IAM password policy requires at least one uppercase letter (Scored)"
|
||||
COMMAND15=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --output json --query 'PasswordPolicy.RequireUppercaseCharacters' 2> /dev/null) # must be true
|
||||
if [[ "$COMMAND15" == "true" ]];then
|
||||
textPass "$REGION: Password Policy requires upper case" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password Policy missing upper-case requirement" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check16="1.6"
|
||||
CHECK_TITLE_check16="[check16] Ensure IAM password policy require at least one lowercase letter"
|
||||
CHECK_SCORED_check16="SCORED"
|
||||
CHECK_CIS_LEVEL_check16="LEVEL1"
|
||||
CHECK_SEVERITY_check16="Medium"
|
||||
CHECK_ASFF_TYPE_check16="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check106="check16"
|
||||
CHECK_SERVICENAME_check16="iam"
|
||||
CHECK_RISK_check16='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check16='Ensure "Requires at least one lowercase letter" is checked under "Password Policy".'
|
||||
CHECK_DOC_check16='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check16='IAM'
|
||||
|
||||
check16(){
|
||||
# "Ensure IAM password policy require at least one lowercase letter (Scored)"
|
||||
COMMAND16=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --output json --query 'PasswordPolicy.RequireLowercaseCharacters' 2> /dev/null) # must be true
|
||||
if [[ "$COMMAND16" == "true" ]];then
|
||||
textPass "$REGION: Password Policy requires lower case" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password Policy missing lower-case requirement" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check17="1.7"
|
||||
CHECK_TITLE_check17="[check17] Ensure IAM password policy require at least one symbol"
|
||||
CHECK_SCORED_check17="SCORED"
|
||||
CHECK_CIS_LEVEL_check17="LEVEL1"
|
||||
CHECK_SEVERITY_check17="Medium"
|
||||
CHECK_ASFF_TYPE_check17="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check107="check17"
|
||||
CHECK_SERVICENAME_check17="iam"
|
||||
CHECK_RISK_check17='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check17='Ensure "Require at least one non-alphanumeric character" is checked under "Password Policy".'
|
||||
CHECK_DOC_check17='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check17='IAM'
|
||||
|
||||
check17(){
|
||||
# "Ensure IAM password policy require at least one symbol (Scored)"
|
||||
COMMAND17=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --output json --query 'PasswordPolicy.RequireSymbols' 2> /dev/null) # must be true
|
||||
if [[ "$COMMAND17" == "true" ]];then
|
||||
textPass "$REGION: Password Policy requires symbol" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password Policy missing symbol requirement" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check18="1.8"
|
||||
CHECK_TITLE_check18="[check18] Ensure IAM password policy require at least one number"
|
||||
CHECK_SCORED_check18="SCORED"
|
||||
CHECK_CIS_LEVEL_check18="LEVEL1"
|
||||
CHECK_SEVERITY_check18="Medium"
|
||||
CHECK_ASFF_TYPE_check18="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check108="check18"
|
||||
CHECK_SERVICENAME_check18="iam"
|
||||
CHECK_RISK_check18='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check18='Ensure "Require at least one number " is checked under "Password Policy".'
|
||||
CHECK_DOC_check18='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check18='IAM'
|
||||
|
||||
check18(){
|
||||
# "Ensure IAM password policy require at least one number (Scored)"
|
||||
COMMAND18=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --output json --query 'PasswordPolicy.RequireNumbers' 2> /dev/null) # must be true
|
||||
if [[ "$COMMAND18" == "true" ]];then
|
||||
textPass "$REGION: Password Policy requires number" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password Policy missing number requirement" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check19="1.9"
|
||||
CHECK_TITLE_check19="[check19] Ensure IAM password policy requires minimum length of 14 or greater"
|
||||
CHECK_SCORED_check19="SCORED"
|
||||
CHECK_CIS_LEVEL_check19="LEVEL1"
|
||||
CHECK_SEVERITY_check19="Medium"
|
||||
CHECK_ASFF_TYPE_check19="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check109="check19"
|
||||
CHECK_SERVICENAME_check19="iam"
|
||||
CHECK_RISK_check19='Password policies are used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets. It is recommended that the password policy require at least one uppercase letter.'
|
||||
CHECK_REMEDIATION_check19='Ensure "Minimum password length" is set to 14 or greater.'
|
||||
CHECK_DOC_check19='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html'
|
||||
CHECK_CAF_EPIC_check19='IAM'
|
||||
|
||||
check19(){
|
||||
# "Ensure IAM password policy requires minimum length of 14 or greater (Scored)"
|
||||
COMMAND19=$($AWSCLI iam get-account-password-policy $PROFILE_OPT --region $REGION --output json --query 'PasswordPolicy.MinimumPasswordLength' 2> /dev/null)
|
||||
if [[ $COMMAND19 -gt "13" ]];then
|
||||
textPass "$REGION: Password Policy requires more than 13 characters" "$REGION" "password policy"
|
||||
else
|
||||
textFail "$REGION: Password Policy missing or weak length requirement" "$REGION" "password policy"
|
||||
fi
|
||||
}
|
||||
@@ -1,68 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check21="2.1"
|
||||
CHECK_TITLE_check21="[check21] Ensure CloudTrail is enabled in all regions"
|
||||
CHECK_SCORED_check21="SCORED"
|
||||
CHECK_CIS_LEVEL_check21="LEVEL1"
|
||||
CHECK_SEVERITY_check21="High"
|
||||
CHECK_ASFF_TYPE_check21="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check21="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check201="check21"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check21="ens-op.acc.7.aws.iam.1 ens-op.mon.1.aws.trail.1"
|
||||
CHECK_SERVICENAME_check21="cloudtrail"
|
||||
CHECK_RISK_check21='AWS CloudTrail is a web service that records AWS API calls for your account and delivers log files to you. The recorded information includes the identity of the API caller; the time of the API call; the source IP address of the API caller; the request parameters; and the response elements returned by the AWS service.'
|
||||
CHECK_REMEDIATION_check21='Ensure Logging is set to ON on all regions (even if they are not being used at the moment.'
|
||||
CHECK_DOC_check21='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrailconcepts.html#cloudtrail-concepts-management-events'
|
||||
CHECK_CAF_EPIC_check21='Logging and Monitoring'
|
||||
|
||||
check21(){
|
||||
trail_count=0
|
||||
# "Ensure CloudTrail is enabled in all regions (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
TRAILS_AND_REGIONS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $regx --query 'trailList[*].{Name:TrailARN, HomeRegion:HomeRegion}' --output text 2>&1 | tr " " ',')
|
||||
if [[ $(echo "$TRAILS_AND_REGIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe trails" "$regx" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $TRAILS_AND_REGIONS ]]; then
|
||||
for reg_trail in $TRAILS_AND_REGIONS; do
|
||||
TRAIL_REGION=$(echo $reg_trail | cut -d',' -f1)
|
||||
if [ $TRAIL_REGION != $regx ]; then # Only report trails once in home region
|
||||
continue
|
||||
fi
|
||||
trail=$(echo $reg_trail | cut -d',' -f2)
|
||||
trail_count=$((trail_count + 1))
|
||||
|
||||
MULTIREGION_TRAIL_STATUS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $TRAIL_REGION --query 'trailList[*].IsMultiRegionTrail' --output text --trail-name-list $trail)
|
||||
if [[ "$MULTIREGION_TRAIL_STATUS" == 'False' ]];then
|
||||
textFail "$regx: Trail $trail is not enabled for all regions" "$regx" "$trail"
|
||||
else
|
||||
TRAIL_ON_OFF_STATUS=$($AWSCLI cloudtrail get-trail-status $PROFILE_OPT --region $TRAIL_REGION --name $trail --query IsLogging --output text)
|
||||
if [[ "$TRAIL_ON_OFF_STATUS" == 'False' ]];then
|
||||
textFail "$regx: Trail $trail is configured for all regions but it is OFF" "$regx" "$trail"
|
||||
else
|
||||
textPass "$regx: Trail $trail is enabled for all regions" "$regx" "$trail"
|
||||
fi
|
||||
fi
|
||||
done
|
||||
fi
|
||||
done
|
||||
if [[ $trail_count == 0 ]]; then
|
||||
if [[ $FILTERREGION ]]; then
|
||||
textFail "$regx: No CloudTrail trails were found in the filtered region" "$regx" "$trail"
|
||||
else
|
||||
textFail "$regx: No CloudTrail trails were found in the account" "$regx" "$trail"
|
||||
fi
|
||||
fi
|
||||
}
|
||||
@@ -1,60 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check22="2.2"
|
||||
CHECK_TITLE_check22="[check22] Ensure CloudTrail log file validation is enabled"
|
||||
CHECK_SCORED_check22="SCORED"
|
||||
CHECK_CIS_LEVEL_check22="LEVEL2"
|
||||
CHECK_SEVERITY_check22="Medium"
|
||||
CHECK_ASFF_TYPE_check22="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check22="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check202="check22"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check22="ens-op.exp.10.aws.trail.1"
|
||||
CHECK_SERVICENAME_check22="cloudtrail"
|
||||
CHECK_RISK_check22='Enabling log file validation will provide additional integrity checking of CloudTrail logs. '
|
||||
CHECK_REMEDIATION_check22='Ensure LogFileValidationEnabled is set to true for each trail.'
|
||||
CHECK_DOC_check22='http://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-log-filevalidation-enabling.html'
|
||||
CHECK_CAF_EPIC_check22='Logging and Monitoring'
|
||||
|
||||
check22(){
|
||||
trail_count=0
|
||||
# "Ensure CloudTrail log file validation is enabled (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
TRAILS_AND_REGIONS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $regx --query 'trailList[*].{Name:TrailARN, HomeRegion:HomeRegion}' --output text 2>&1 | tr " " ',')
|
||||
if [[ $(echo "$TRAILS_AND_REGIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe trails" "$regx" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $TRAILS_AND_REGIONS ]]; then
|
||||
for reg_trail in $TRAILS_AND_REGIONS; do
|
||||
TRAIL_REGION=$(echo $reg_trail | cut -d',' -f1)
|
||||
if [ $TRAIL_REGION != $regx ]; then # Only report trails once in home region
|
||||
continue
|
||||
fi
|
||||
trail=$(echo $reg_trail | cut -d',' -f2)
|
||||
trail_count=$((trail_count + 1))
|
||||
|
||||
LOGFILEVALIDATION_TRAIL_STATUS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $TRAIL_REGION --query 'trailList[*].LogFileValidationEnabled' --output text --trail-name-list $trail)
|
||||
if [[ "$LOGFILEVALIDATION_TRAIL_STATUS" == 'False' ]];then
|
||||
textFail "$regx: Trail $trail log file validation disabled" "$regx" "$trail"
|
||||
else
|
||||
textPass "$regx: Trail $trail log file validation enabled" "$regx" "$trail"
|
||||
fi
|
||||
|
||||
done
|
||||
fi
|
||||
done
|
||||
if [[ $trail_count == 0 ]]; then
|
||||
textFail "$REGION: No CloudTrail trails were found in the account" "$REGION" "$trail"
|
||||
fi
|
||||
}
|
||||
@@ -1,94 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check23="2.3"
|
||||
CHECK_TITLE_check23="[check23] Ensure the S3 bucket CloudTrail logs to is not publicly accessible"
|
||||
CHECK_SCORED_check23="SCORED"
|
||||
CHECK_CIS_LEVEL_check23="LEVEL1"
|
||||
CHECK_SEVERITY_check23="Critical"
|
||||
CHECK_ASFF_TYPE_check23="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check23="AwsS3Bucket"
|
||||
CHECK_ALTERNATE_check203="check23"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check23="ens-op.exp.10.aws.trail.3 ens-op.exp.10.aws.trail.4"
|
||||
CHECK_SERVICENAME_check23="cloudtrail"
|
||||
CHECK_RISK_check23='Allowing public access to CloudTrail log content may aid an adversary in identifying weaknesses in the affected accounts use or configuration.'
|
||||
CHECK_REMEDIATION_check23='Analyze Bucket policy to validate appropriate permissions. Ensure the AllUsers principal is not granted privileges. Ensure the AuthenticatedUsers principal is not granted privileges.'
|
||||
CHECK_DOC_check23='https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_principal.html'
|
||||
CHECK_CAF_EPIC_check23='Logging and Monitoring'
|
||||
|
||||
check23(){
|
||||
trail_count=0
|
||||
# "Ensure the S3 bucket CloudTrail logs to is not publicly accessible (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
TRAILS_AND_REGIONS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $regx --query 'trailList[*].{Name:TrailARN, HomeRegion:HomeRegion}' --output text 2>&1 | tr " " ',')
|
||||
if [[ $(echo "$TRAILS_AND_REGIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe trails" "$regx" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $TRAILS_AND_REGIONS ]]; then
|
||||
for reg_trail in $TRAILS_AND_REGIONS; do
|
||||
TRAIL_REGION=$(echo $reg_trail | cut -d',' -f1)
|
||||
if [ $TRAIL_REGION != $regx ]; then # Only report trails once in home region
|
||||
continue
|
||||
fi
|
||||
trail=$(echo $reg_trail | cut -d',' -f2)
|
||||
trail_count=$((trail_count + 1))
|
||||
|
||||
CLOUDTRAILBUCKET=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $TRAIL_REGION --query 'trailList[*].[S3BucketName]' --output text --trail-name-list $trail)
|
||||
if [[ -z $CLOUDTRAILBUCKET ]]; then
|
||||
textFail "Trail $trail in $TRAIL_REGION does not publish to S3"
|
||||
continue
|
||||
fi
|
||||
|
||||
CLOUDTRAIL_ACCOUNT_ID=$(echo $trail | awk -F: '{ print $5 }')
|
||||
if [ "$CLOUDTRAIL_ACCOUNT_ID" != "$ACCOUNT_NUM" ]; then
|
||||
textInfo "Trail $trail in $TRAIL_REGION S3 logging bucket $CLOUDTRAILBUCKET is not in current account"
|
||||
continue
|
||||
fi
|
||||
|
||||
#
|
||||
# LOCATION - requests referencing buckets created after March 20, 2019
|
||||
# must be made to S3 endpoints in the same region as the bucket was
|
||||
# created.
|
||||
#
|
||||
BUCKET_LOCATION=$($AWSCLI s3api get-bucket-location $PROFILE_OPT --region $regx --bucket $CLOUDTRAILBUCKET --output text 2>&1)
|
||||
if [[ $(echo "$BUCKET_LOCATION" | grep AccessDenied) ]]; then
|
||||
textInfo "Trail $trail in $TRAIL_REGION Access Denied getting bucket location for $CLOUDTRAILBUCKET"
|
||||
continue
|
||||
fi
|
||||
if [[ $BUCKET_LOCATION == "None" ]]; then
|
||||
BUCKET_LOCATION="us-east-1"
|
||||
fi
|
||||
if [[ $BUCKET_LOCATION == "EU" ]]; then
|
||||
BUCKET_LOCATION="eu-west-1"
|
||||
fi
|
||||
|
||||
CLOUDTRAILBUCKET_HASALLPERMISIONS=$($AWSCLI s3api get-bucket-acl --bucket $CLOUDTRAILBUCKET $PROFILE_OPT --region $BUCKET_LOCATION --query 'Grants[?Grantee.URI==`http://acs.amazonaws.com/groups/global/AllUsers`]' --output text 2>&1)
|
||||
if [[ $(echo "$CLOUDTRAILBUCKET_HASALLPERMISIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "Trail $trail in $TRAIL_REGION Access Denied getting bucket acl for $CLOUDTRAILBUCKET"
|
||||
continue
|
||||
fi
|
||||
|
||||
if [[ -z $CLOUDTRAILBUCKET_HASALLPERMISIONS ]]; then
|
||||
textPass "Trail $trail in $TRAIL_REGION S3 logging bucket $CLOUDTRAILBUCKET is not publicly accessible"
|
||||
else
|
||||
textFail "Trail $trail in $TRAIL_REGION S3 logging bucket $CLOUDTRAILBUCKET is publicly accessible"
|
||||
fi
|
||||
|
||||
done
|
||||
fi
|
||||
done
|
||||
if [[ $trail_count == 0 ]]; then
|
||||
textFail "$REGION: No CloudTrail trails were found in the account" "$REGION" "$trail"
|
||||
fi
|
||||
}
|
||||
@@ -1,66 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check24="2.4"
|
||||
CHECK_TITLE_check24="[check24] Ensure CloudTrail trails are integrated with CloudWatch Logs"
|
||||
CHECK_SCORED_check24="SCORED"
|
||||
CHECK_CIS_LEVEL_check24="LEVEL1"
|
||||
CHECK_SEVERITY_check24="Low"
|
||||
CHECK_ASFF_TYPE_check24="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check24="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check204="check24"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check24="ens-op.exp.8.aws.cw.1"
|
||||
CHECK_SERVICENAME_check24="cloudtrail"
|
||||
CHECK_RISK_check24='Sending CloudTrail logs to CloudWatch Logs will facilitate real-time and historic activity logging based on user; API; resource; and IP address; and provides opportunity to establish alarms and notifications for anomalous or sensitivity account activity.'
|
||||
CHECK_REMEDIATION_check24='Validate that the trails in CloudTrail has an arn set in the CloudWatchLogsLogGroupArn property.'
|
||||
CHECK_DOC_check24='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/send-cloudtrail-events-to-cloudwatch-logs.html'
|
||||
CHECK_CAF_EPIC_check24='Logging and Monitoring'
|
||||
|
||||
check24(){
|
||||
trail_count=0
|
||||
# "Ensure CloudTrail trails are integrated with CloudWatch Logs (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
TRAILS_AND_REGIONS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $regx --query 'trailList[*].{Name:TrailARN, HomeRegion:HomeRegion}' --output text 2>&1 | tr " " ',')
|
||||
if [[ $(echo "$TRAILS_AND_REGIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe trails" "$regx" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $TRAILS_AND_REGIONS ]]; then
|
||||
for reg_trail in $TRAILS_AND_REGIONS; do
|
||||
TRAIL_REGION=$(echo $reg_trail | cut -d',' -f1)
|
||||
if [ $TRAIL_REGION != $regx ]; then # Only report trails once in home region
|
||||
continue
|
||||
fi
|
||||
trail=$(echo $reg_trail | cut -d',' -f2)
|
||||
trail_count=$((trail_count + 1))
|
||||
|
||||
LATESTDELIVERY_TIMESTAMP=$($AWSCLI cloudtrail get-trail-status --name $trail $PROFILE_OPT --region $TRAIL_REGION --query 'LatestCloudWatchLogsDeliveryTime' --output text|grep -v None)
|
||||
if [[ ! $LATESTDELIVERY_TIMESTAMP ]];then
|
||||
textFail "$TRAIL_REGION: $trail trail is not logging in the last 24h or not configured (it is in $TRAIL_REGION)" "$TRAIL_REGION" "$trail"
|
||||
else
|
||||
LATESTDELIVERY_DATE=$(timestamp_to_date $LATESTDELIVERY_TIMESTAMP)
|
||||
HOWOLDER=$(how_older_from_today $LATESTDELIVERY_DATE)
|
||||
if [ $HOWOLDER -gt "1" ];then
|
||||
textFail "$TRAIL_REGION: $trail trail is not logging in the last 24h or not configured" "$TRAIL_REGION" "$trail"
|
||||
else
|
||||
textPass "$TRAIL_REGION: $trail trail has been logging during the last 24h" "$TRAIL_REGION" "$trail"
|
||||
fi
|
||||
fi
|
||||
|
||||
done
|
||||
fi
|
||||
done
|
||||
if [[ $trail_count == 0 ]]; then
|
||||
textFail "$REGION: No CloudTrail trails were found in the account" "$REGION" "$trail"
|
||||
fi
|
||||
}
|
||||
@@ -1,47 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check25="2.5"
|
||||
CHECK_TITLE_check25="[check25] Ensure AWS Config is enabled in all regions"
|
||||
CHECK_SCORED_check25="SCORED"
|
||||
CHECK_CIS_LEVEL_check25="LEVEL1"
|
||||
CHECK_SEVERITY_check25="Medium"
|
||||
CHECK_ASFF_TYPE_check25="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ALTERNATE_check205="check25"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check25="ens-op.exp.1.aws.cfg.1"
|
||||
CHECK_SERVICENAME_check25="configservice"
|
||||
CHECK_RISK_check25='The AWS configuration item history captured by AWS Config enables security analysis; resource change tracking; and compliance auditing.'
|
||||
CHECK_REMEDIATION_check25='It is recommended to enable AWS Config be enabled in all regions.'
|
||||
CHECK_DOC_check25='https://aws.amazon.com/blogs/mt/aws-config-best-practices/'
|
||||
CHECK_CAF_EPIC_check25='Logging and Monitoring'
|
||||
|
||||
check25(){
|
||||
# "Ensure AWS Config is enabled in all regions (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
CHECK_AWSCONFIG_RECORDING=$($AWSCLI configservice describe-configuration-recorder-status $PROFILE_OPT --region $regx --query 'ConfigurationRecordersStatus[*].recording' --output text 2>&1)
|
||||
CHECK_AWSCONFIG_STATUS=$($AWSCLI configservice describe-configuration-recorder-status $PROFILE_OPT --region $regx --query 'ConfigurationRecordersStatus[*].lastStatus' --output text 2>&1)
|
||||
if [[ $(echo "$CHECK_AWSCONFIG_STATUS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe configuration recorder status" "$regx" "recorder"
|
||||
continue
|
||||
fi
|
||||
if [[ $CHECK_AWSCONFIG_RECORDING == "True" ]]; then
|
||||
if [[ $CHECK_AWSCONFIG_STATUS == "SUCCESS" ]]; then
|
||||
textPass "$regx: AWS Config recorder enabled" "$regx" "recorder"
|
||||
else
|
||||
textFail "$regx: AWS Config recorder in failure state" "$regx" "recorder"
|
||||
fi
|
||||
else
|
||||
textFail "$regx: AWS Config recorder disabled" "$regx" "recorder"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,93 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check26="2.6"
|
||||
CHECK_TITLE_check26="[check26] Ensure S3 bucket access logging is enabled on the CloudTrail S3 bucket"
|
||||
CHECK_SCORED_check26="SCORED"
|
||||
CHECK_CIS_LEVEL_check26="LEVEL1"
|
||||
CHECK_SEVERITY_check26="Medium"
|
||||
CHECK_ASFF_TYPE_check26="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check26="AwsS3Bucket"
|
||||
CHECK_ALTERNATE_check206="check26"
|
||||
CHECK_SERVICENAME_check26="s3"
|
||||
CHECK_RISK_check26='Server access logs can assist you in security and access audits; help you learn about your customer base; and understand your Amazon S3 bill.'
|
||||
CHECK_REMEDIATION_check26='Ensure that S3 buckets have Logging enabled. CloudTrail data events can be used in place of S3 bucket logging. If that is the case; this finding can be considered a false positive.'
|
||||
CHECK_DOC_check26='https://docs.aws.amazon.com/AmazonS3/latest/dev/security-best-practices.html'
|
||||
CHECK_CAF_EPIC_check26='Logging and Monitoring'
|
||||
|
||||
check26(){
|
||||
trail_count=0
|
||||
# "Ensure S3 bucket access logging is enabled on the CloudTrail S3 bucket (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
TRAILS_AND_REGIONS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $regx --query 'trailList[*].{Name:TrailARN, HomeRegion:HomeRegion}' --output text 2>&1 | tr " " ',')
|
||||
if [[ $(echo "$TRAILS_AND_REGIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe trails" "$regx" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $TRAILS_AND_REGIONS ]]; then
|
||||
for reg_trail in $TRAILS_AND_REGIONS; do
|
||||
TRAIL_REGION=$(echo $reg_trail | cut -d',' -f1)
|
||||
if [ $TRAIL_REGION != $regx ]; then # Only report trails once in home region
|
||||
continue
|
||||
fi
|
||||
trail=$(echo $reg_trail | cut -d',' -f2)
|
||||
trail_count=$((trail_count + 1))
|
||||
|
||||
CLOUDTRAILBUCKET=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $TRAIL_REGION --query 'trailList[*].[S3BucketName]' --output text --trail-name-list $trail)
|
||||
if [[ -z $CLOUDTRAILBUCKET ]]; then
|
||||
textFail "$regx: Trail $trail does not publish to S3" "$TRAIL_REGION" "$trail"
|
||||
continue
|
||||
fi
|
||||
|
||||
CLOUDTRAIL_ACCOUNT_ID=$(echo $trail | awk -F: '{ print $5 }')
|
||||
if [ "$CLOUDTRAIL_ACCOUNT_ID" != "$ACCOUNT_NUM" ]; then
|
||||
textInfo "$regx: Trail $trail S3 logging bucket $CLOUDTRAILBUCKET is not in current account" "$TRAIL_REGION" "$trail"
|
||||
continue
|
||||
fi
|
||||
|
||||
#
|
||||
# LOCATION - requests referencing buckets created after March 20, 2019
|
||||
# must be made to S3 endpoints in the same region as the bucket was
|
||||
# created.
|
||||
#
|
||||
BUCKET_LOCATION=$($AWSCLI s3api get-bucket-location $PROFILE_OPT --region $regx --bucket $CLOUDTRAILBUCKET --output text 2>&1)
|
||||
if [[ $(echo "$BUCKET_LOCATION" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Trail $trail Access Denied getting bucket location for $CLOUDTRAILBUCKET" "$TRAIL_REGION" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $BUCKET_LOCATION == "None" ]]; then
|
||||
BUCKET_LOCATION="us-east-1"
|
||||
fi
|
||||
if [[ $BUCKET_LOCATION == "EU" ]]; then
|
||||
BUCKET_LOCATION="eu-west-1"
|
||||
fi
|
||||
|
||||
CLOUDTRAILBUCKET_LOGENABLED=$($AWSCLI s3api get-bucket-logging --bucket $CLOUDTRAILBUCKET $PROFILE_OPT --region $BUCKET_LOCATION --query 'LoggingEnabled.TargetBucket' --output text 2>&1)
|
||||
if [[ $(echo "$CLOUDTRAILBUCKET_LOGENABLED" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Trail $trail Access Denied getting bucket logging for $CLOUDTRAILBUCKET" "$TRAIL_REGION" "$trail"
|
||||
continue
|
||||
fi
|
||||
|
||||
if [[ $CLOUDTRAILBUCKET_LOGENABLED != "None" ]]; then
|
||||
textPass "$regx: Trail $trail S3 bucket access logging is enabled for $CLOUDTRAILBUCKET" "$TRAIL_REGION" "$trail"
|
||||
else
|
||||
textFail "$regx: Trail $trail S3 bucket access logging is not enabled for $CLOUDTRAILBUCKET" "$TRAIL_REGION" "$trail"
|
||||
fi
|
||||
|
||||
done
|
||||
fi
|
||||
done
|
||||
if [[ $trail_count == 0 ]]; then
|
||||
textFail "$REGION: No CloudTrail trails were found in the account" "$REGION" "$trail"
|
||||
fi
|
||||
}
|
||||
@@ -1,59 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check27="2.7"
|
||||
CHECK_TITLE_check27="[check27] Ensure CloudTrail logs are encrypted at rest using KMS CMKs"
|
||||
CHECK_SCORED_check27="SCORED"
|
||||
CHECK_CIS_LEVEL_check27="LEVEL2"
|
||||
CHECK_SEVERITY_check27="Medium"
|
||||
CHECK_ASFF_TYPE_check27="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check27="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check207="check27"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check27="ens-op.exp.10.aws.trail.5"
|
||||
CHECK_SERVICENAME_check27="cloudtrail"
|
||||
CHECK_RISK_check27='By default; the log files delivered by CloudTrail to your bucket are encrypted by Amazon server-side encryption with Amazon S3-managed encryption keys (SSE-S3). To provide a security layer that is directly manageable; you can instead use server-side encryption with AWS KMS–managed keys (SSE-KMS) for your CloudTrail log files.'
|
||||
CHECK_REMEDIATION_check27='This approach has the following advantages: You can create and manage the CMK encryption keys yourself. You can use a single CMK to encrypt and decrypt log files for multiple accounts across all regions. You have control over who can use your key for encrypting and decrypting CloudTrail log files. You can assign permissions for the key to the users. You have enhanced security.'
|
||||
CHECK_DOC_check27='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/encrypting-cloudtrail-log-files-with-aws-kms.html'
|
||||
CHECK_CAF_EPIC_check27='Logging and Monitoring'
|
||||
|
||||
check27(){
|
||||
trail_count=0
|
||||
# "Ensure CloudTrail logs are encrypted at rest using KMS CMKs (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
TRAILS_AND_REGIONS=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $regx --query 'trailList[*].{Name:TrailARN, HomeRegion:HomeRegion}' --output text 2>&1 | tr " " ',')
|
||||
if [[ $(echo "$TRAILS_AND_REGIONS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe trails" "$regx" "$trail"
|
||||
continue
|
||||
fi
|
||||
if [[ $TRAILS_AND_REGIONS ]]; then
|
||||
for reg_trail in $TRAILS_AND_REGIONS; do
|
||||
TRAIL_REGION=$(echo $reg_trail | cut -d',' -f1)
|
||||
if [ $TRAIL_REGION != $regx ]; then # Only report trails once in home region
|
||||
continue
|
||||
fi
|
||||
trail=$(echo $reg_trail | cut -d',' -f2)
|
||||
trail_count=$((trail_count + 1))
|
||||
|
||||
KMSKEYID=$($AWSCLI cloudtrail describe-trails $PROFILE_OPT --region $TRAIL_REGION --query 'trailList[*].KmsKeyId' --output text --trail-name-list $trail)
|
||||
if [[ "$KMSKEYID" ]];then
|
||||
textPass "$regx: Trail $trail has encryption enabled" "$regx" "$trail"
|
||||
else
|
||||
textFail "$regx: Trail $trail has encryption disabled" "$regx" "$trail"
|
||||
fi
|
||||
done
|
||||
fi
|
||||
done
|
||||
if [[ $trail_count == 0 ]]; then
|
||||
textFail "$REGION: No CloudTrail trails were found in the account" "$REGION" "$trail"
|
||||
fi
|
||||
}
|
||||
@@ -1,80 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check28="2.8"
|
||||
CHECK_TITLE_check28="[check28] Ensure rotation for customer created KMS CMKs is enabled"
|
||||
CHECK_SCORED_check28="SCORED"
|
||||
CHECK_CIS_LEVEL_check28="LEVEL2"
|
||||
CHECK_SEVERITY_check28="Medium"
|
||||
CHECK_ASFF_TYPE_check28="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check28="AwsKmsKey"
|
||||
CHECK_ALTERNATE_check208="check28"
|
||||
CHECK_SERVICENAME_check28="kms"
|
||||
CHECK_RISK_check28='Cryptographic best practices discourage extensive reuse of encryption keys. Consequently; Customer Master Keys (CMKs) should be rotated to prevent usage of compromised keys.'
|
||||
CHECK_REMEDIATION_check28='For every KMS Customer Master Keys (CMKs); ensure that Rotate this key every year is enabled.'
|
||||
CHECK_DOC_check28='https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html'
|
||||
CHECK_CAF_EPIC_check28='Data Protection'
|
||||
|
||||
check28(){
|
||||
# "Ensure rotation for customer created CMKs is enabled (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
CHECK_KMS_KEYLIST=$($AWSCLI kms list-keys $PROFILE_OPT --region $regx --output text --query 'Keys[*].KeyId' --output text 2>&1)
|
||||
if [[ $(echo "$CHECK_KMS_KEYLIST" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied trying to list keys" "$regx" "$key"
|
||||
continue
|
||||
fi
|
||||
if [[ $CHECK_KMS_KEYLIST ]]; then
|
||||
cmk_count=0
|
||||
for key in $CHECK_KMS_KEYLIST; do
|
||||
KMSDETAILS=$($AWSCLI kms describe-key --key-id $key $PROFILE_OPT --region $regx --query 'KeyMetadata.{key:KeyId,man:KeyManager,origin:Origin,spec:CustomerMasterKeySpec,state:KeyState}' --output text 2>&1 | grep SYMMETRIC)
|
||||
if [[ $(echo "$KMSDETAILS" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied describing key $key" "$regx" "$key"
|
||||
continue
|
||||
fi
|
||||
|
||||
KEYID=$(echo $KMSDETAILS | awk '{print $1}')
|
||||
KEYMANAGER=$(echo $KMSDETAILS | awk '{print $2}')
|
||||
KEYORIGIN=$(echo $KMSDETAILS | awk '{print $3}')
|
||||
KEYSTATE=$(echo $KMSDETAILS | awk '{print $5}')
|
||||
|
||||
if [[ "$KEYMANAGER" == "AWS" ]]; then
|
||||
continue
|
||||
fi
|
||||
if [[ "$KEYSTATE" != "Enabled" ]]; then
|
||||
continue
|
||||
fi
|
||||
cmk_count=$((cmk_count + 1))
|
||||
|
||||
if [[ "$KEYORIGIN" == "EXTERNAL" ]]; then
|
||||
textPass "$regx: Key $key uses imported key material" "$regx" "$key"
|
||||
else
|
||||
CHECK_KMS_KEY_ROTATION=$($AWSCLI kms get-key-rotation-status --key-id $key $PROFILE_OPT --region $regx --output text 2>&1)
|
||||
if [[ $(echo "$CHECK_KMS_KEY_ROTATION" | grep AccessDenied) ]]; then
|
||||
textInfo "$regx: Access Denied getting key rotation status for $key " "$regx" "$key"
|
||||
continue
|
||||
fi
|
||||
if [[ "$CHECK_KMS_KEY_ROTATION" == "True" ]];then
|
||||
textPass "$regx: Key $key automatic rotation of the key material is enabled" "$regx" "$key"
|
||||
else
|
||||
textFail "$regx: Key $key automatic rotation of the key material is disabled" "$regx" "$key"
|
||||
fi
|
||||
fi
|
||||
done
|
||||
if [[ $cmk_count == 0 ]]; then
|
||||
textInfo "$regx: This region has no customer managed keys" "$regx" "$key"
|
||||
fi
|
||||
else
|
||||
textInfo "$regx: This region has no KMS keys" "$regx" "$key"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,52 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check29="2.9"
|
||||
CHECK_TITLE_check29="[check29] Ensure VPC Flow Logging is Enabled in all VPCs"
|
||||
CHECK_SCORED_check29="SCORED"
|
||||
CHECK_CIS_LEVEL_check29="LEVEL2"
|
||||
CHECK_SEVERITY_check29="Medium"
|
||||
CHECK_ASFF_TYPE_check29="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check29="AwsEc2Vpc"
|
||||
CHECK_ALTERNATE_check209="check29"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check29="ens-op.mon.1.aws.flow.1"
|
||||
CHECK_SERVICENAME_check29="vpc"
|
||||
CHECK_RISK_check29='VPC Flow Logs provide visibility into network traffic that traverses the VPC and can be used to detect anomalous traffic or insight during security workflows.'
|
||||
CHECK_REMEDIATION_check29='It is recommended that VPC Flow Logs be enabled for packet "Rejects" for VPCs. '
|
||||
CHECK_DOC_check29='http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/flow-logs.html '
|
||||
CHECK_CAF_EPIC_check29='Logging and Monitoring'
|
||||
|
||||
check29(){
|
||||
# "Ensure VPC Flow Logging is Enabled in all VPCs (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
AVAILABLE_VPC=$($AWSCLI ec2 describe-vpcs $PROFILE_OPT --region $regx --query 'Vpcs[?State==`available`].VpcId' --output text 2>&1)
|
||||
if [[ $(echo "$AVAILABLE_VPC" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe VPCs" "$regx" "$vpcx"
|
||||
continue
|
||||
fi
|
||||
for vpcx in $AVAILABLE_VPC; do
|
||||
CHECK_FL=$($AWSCLI ec2 describe-flow-logs $PROFILE_OPT --region $regx --filter Name="resource-id",Values="${vpcx}" --query 'FlowLogs[?FlowLogStatus==`ACTIVE`].FlowLogId' --output text 2>&1)
|
||||
if [[ $(echo "$CHECK_FL" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe flow logs in VPC $vpcx" "$regx" "$vpcx"
|
||||
continue
|
||||
fi
|
||||
if [[ $CHECK_FL ]]; then
|
||||
for FL in $CHECK_FL; do
|
||||
textPass "$regx: VPC $vpcx VPCFlowLog is enabled for LogGroupName: $FL" "$regx" "$vpcx"
|
||||
done
|
||||
else
|
||||
textFail "$regx: VPC $vpcx VPCFlowLog is disabled" "$regx" "$vpcx"
|
||||
fi
|
||||
done
|
||||
done
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/MyCloudTrailLG \
|
||||
# --filter-name AWSAuthorizationFailures \
|
||||
# --filter-pattern '{ $.errorCode = "*UnauthorizedOperation" || $.errorCode = "AccessDenied*" }' \
|
||||
# --metric-transformations metricName=AuthorizationFailureCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name "Authorization Failures" \
|
||||
# --alarm-description "Alarm triggered when unauthorized API calls are made" \
|
||||
# --metric-name AuthorizationFailureCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check31="3.1"
|
||||
CHECK_TITLE_check31="[check31] Ensure a log metric filter and alarm exist for unauthorized API calls"
|
||||
CHECK_SCORED_check31="SCORED"
|
||||
CHECK_CIS_LEVEL_check31="LEVEL1"
|
||||
CHECK_SEVERITY_check31="Medium"
|
||||
CHECK_ASFF_TYPE_check31="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check31="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check301="check31"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check31="ens-op.exp.8.aws.trail.2"
|
||||
CHECK_SERVICENAME_check31="iam"
|
||||
CHECK_RISK_check31='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check31='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check31='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check31='Logging and Monitoring'
|
||||
|
||||
check31(){
|
||||
check3x '\$\.errorCode\s*=\s*"\*UnauthorizedOperation".+\$\.errorCode\s*=\s*"AccessDenied\*"'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name SecurityGroupConfigChanges \
|
||||
# --filter-pattern '{ ($.eventName = AuthorizeSecurityGroupIngress) || ($.eventName = AuthorizeSecurityGroupEgress) || ($.eventName = RevokeSecurityGroupIngress) || ($.eventName = RevokeSecurityGroupEgress) || ($.eventName = CreateSecurityGroup) || ($.eventName = DeleteSecurityGroup) }' \
|
||||
# --metric-transformations metricName=SecurityGroupEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name SecurityGroupConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS security group(s) config changes." \
|
||||
# --metric-name SecurityGroupEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check310="3.10"
|
||||
CHECK_TITLE_check310="[check310] Ensure a log metric filter and alarm exist for security group changes"
|
||||
CHECK_SCORED_check310="SCORED"
|
||||
CHECK_CIS_LEVEL_check310="LEVEL2"
|
||||
CHECK_SEVERITY_check310="Medium"
|
||||
CHECK_ASFF_TYPE_check310="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check310="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check310="check310"
|
||||
CHECK_SERVICENAME_check310="ec2"
|
||||
CHECK_RISK_check310='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check310='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check310='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check310='Logging and Monitoring'
|
||||
|
||||
check310(){
|
||||
check3x '\$\.eventName\s*=\s*AuthorizeSecurityGroupIngress.+\$\.eventName\s*=\s*AuthorizeSecurityGroupEgress.+\$\.eventName\s*=\s*RevokeSecurityGroupIngress.+\$\.eventName\s*=\s*RevokeSecurityGroupEgress.+\$\.eventName\s*=\s*CreateSecurityGroup.+\$\.eventName\s*=\s*DeleteSecurityGroup'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name NetworkACLConfigChanges \
|
||||
# --filter-pattern '{ ($.eventName = CreateNetworkAcl) || ($.eventName = CreateNetworkAclEntry) || ($.eventName = DeleteNetworkAcl) || ($.eventName = DeleteNetworkAclEntry) || ($.eventName = ReplaceNetworkAclEntry) || ($.eventName = ReplaceNetworkAclAssociation) }' \
|
||||
# --metric-transformations metricName=NetworkAclEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name NetworkACLConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS Network ACL(s) config changes." \
|
||||
# --metric-name NetworkAclEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check311="3.11"
|
||||
CHECK_TITLE_check311="[check311] Ensure a log metric filter and alarm exist for changes to Network Access Control Lists (NACL)"
|
||||
CHECK_SCORED_check311="SCORED"
|
||||
CHECK_CIS_LEVEL_check311="LEVEL2"
|
||||
CHECK_SEVERITY_check311="Medium"
|
||||
CHECK_ASFF_TYPE_check311="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check311="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check311="check311"
|
||||
CHECK_SERVICENAME_check311="vpc"
|
||||
CHECK_RISK_check311='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check311='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check311='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check311='Logging and Monitoring'
|
||||
|
||||
check311(){
|
||||
check3x '\$\.eventName\s*=\s*CreateNetworkAcl.+\$\.eventName\s*=\s*CreateNetworkAclEntry.+\$\.eventName\s*=\s*DeleteNetworkAcl.+\$\.eventName\s*=\s*DeleteNetworkAclEntry.+\$\.eventName\s*=\s*ReplaceNetworkAclEntry.+\$\.eventName\s*=\s*ReplaceNetworkAclAssociation'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name VPCGatewayConfigChanges \
|
||||
# --filter-pattern '{ ($.eventName = CreateCustomerGateway) || ($.eventName = DeleteCustomerGateway) || ($.eventName = AttachInternetGateway) || ($.eventName = CreateInternetGateway) || ($.eventName = DeleteInternetGateway) || ($.eventName = DetachInternetGateway) }' \
|
||||
# --metric-transformations metricName=GatewayEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name VPCGatewayConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by VPC Customer/Internet Gateway changes." \
|
||||
# --metric-name GatewayEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check312="3.12"
|
||||
CHECK_TITLE_check312="[check312] Ensure a log metric filter and alarm exist for changes to network gateways"
|
||||
CHECK_SCORED_check312="SCORED"
|
||||
CHECK_CIS_LEVEL_check312="LEVEL1"
|
||||
CHECK_SEVERITY_check312="Medium"
|
||||
CHECK_ASFF_TYPE_check312="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check312="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check312="check312"
|
||||
CHECK_SERVICENAME_check312="vpc"
|
||||
CHECK_RISK_check312='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check312='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check312='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check312='Logging and Monitoring'
|
||||
|
||||
check312(){
|
||||
check3x '\$\.eventName\s*=\s*CreateCustomerGateway.+\$\.eventName\s*=\s*DeleteCustomerGateway.+\$\.eventName\s*=\s*AttachInternetGateway.+\$\.eventName\s*=\s*CreateInternetGateway.+\$\.eventName\s*=\s*DeleteInternetGateway.+\$\.eventName\s*=\s*DetachInternetGateway'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name RouteTableConfigChanges \
|
||||
# --filter-pattern '{ ($.eventName = CreateRoute) || ($.eventName = CreateRouteTable) || ($.eventName = ReplaceRoute) || ($.eventName = ReplaceRouteTableAssociation) || ($.eventName = DeleteRouteTable) || ($.eventName = DeleteRoute) || ($.eventName = DisassociateRouteTable) }' \
|
||||
# --metric-transformations metricName=RouteTableEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name RouteTableConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS Route Table config changes." \
|
||||
# --metric-name RouteTableEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check313="3.13"
|
||||
CHECK_TITLE_check313="[check313] Ensure a log metric filter and alarm exist for route table changes"
|
||||
CHECK_SCORED_check313="SCORED"
|
||||
CHECK_CIS_LEVEL_check313="LEVEL1"
|
||||
CHECK_SEVERITY_check313="Medium"
|
||||
CHECK_ASFF_TYPE_check313="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check313="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check313="check313"
|
||||
CHECK_SERVICENAME_check313="vpc"
|
||||
CHECK_RISK_check313='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check313='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check313='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check313='Logging and Monitoring'
|
||||
|
||||
check313(){
|
||||
check3x '\$\.eventName\s*=\s*CreateRoute.+\$\.eventName\s*=\s*CreateRouteTable.+\$\.eventName\s*=\s*ReplaceRoute.+\$\.eventName\s*=\s*ReplaceRouteTableAssociation.+\$\.eventName\s*=\s*DeleteRouteTable.+\$\.eventName\s*=\s*DeleteRoute.+\$\.eventName\s*=\s*DisassociateRouteTable'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name VPCNetworkConfigChanges \
|
||||
# --filter-pattern '{ ($.eventName = CreateVpc) || ($.eventName = DeleteVpc) || ($.eventName = ModifyVpcAttribute) || ($.eventName = AcceptVpcPeeringConnection) || ($.eventName = CreateVpcPeeringConnection) || ($.eventName = DeleteVpcPeeringConnection) || ($.eventName = RejectVpcPeeringConnection) || ($.eventName = AttachClassicLinkVpc) || ($.eventName = DetachClassicLinkVpc) || ($.eventName = DisableVpcClassicLink) || ($.eventName = EnableVpcClassicLink) }' \
|
||||
# --metric-transformations metricName=VpcEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name VPCNetworkConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS VPC(s) environment config changes." \
|
||||
# --metric-name VpcEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check314="3.14"
|
||||
CHECK_TITLE_check314="[check314] Ensure a log metric filter and alarm exist for VPC changes"
|
||||
CHECK_SCORED_check314="SCORED"
|
||||
CHECK_CIS_LEVEL_check314="LEVEL1"
|
||||
CHECK_SEVERITY_check314="Medium"
|
||||
CHECK_ASFF_TYPE_check314="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check314="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check314="check314"
|
||||
CHECK_SERVICENAME_check314="vpc"
|
||||
CHECK_RISK_check314='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check314='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check314='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check314='Logging and Monitoring'
|
||||
|
||||
check314(){
|
||||
check3x '\$\.eventName\s*=\s*CreateVpc.+\$\.eventName\s*=\s*DeleteVpc.+\$\.eventName\s*=\s*ModifyVpcAttribute.+\$\.eventName\s*=\s*AcceptVpcPeeringConnection.+\$\.eventName\s*=\s*CreateVpcPeeringConnection.+\$\.eventName\s*=\s*DeleteVpcPeeringConnection.+\$\.eventName\s*=\s*RejectVpcPeeringConnection.+\$\.eventName\s*=\s*AttachClassicLinkVpc.+\$\.eventName\s*=\s*DetachClassicLinkVpc.+\$\.eventName\s*=\s*DisableVpcClassicLink.+\$\.eventName\s*=\s*EnableVpcClassicLink'
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name ConsoleSignInWithoutMfaCount \
|
||||
# --filter-pattern '{ $.eventName = "ConsoleLogin" && $.additionalEventData.MFAUsed != "Yes" }' \
|
||||
# --metric-transformations metricName=ConsoleSignInWithoutMfaCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name ConsoleSignInWithoutMfaAlarm \
|
||||
# --alarm-description "Triggered by sign-in requests made without MFA." \
|
||||
# --metric-name ConsoleSignInWithoutMfaCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check32="3.2"
|
||||
CHECK_TITLE_check32="[check32] Ensure a log metric filter and alarm exist for Management Console sign-in without MFA"
|
||||
CHECK_SCORED_check32="SCORED"
|
||||
CHECK_CIS_LEVEL_check32="LEVEL1"
|
||||
CHECK_SEVERITY_check32="Medium"
|
||||
CHECK_ASFF_TYPE_check32="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check32="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check302="check32"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check32="ens-op.exp.8.aws.trail.4"
|
||||
CHECK_SERVICENAME_check32="iam"
|
||||
CHECK_RISK_check32='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check32='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check32='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check32='Logging and Monitoring'
|
||||
|
||||
check32(){
|
||||
check3x '\$\.eventName\s*=\s*"ConsoleLogin".+\$\.additionalEventData\.MFAUsed\s*!=\s*"Yes"'
|
||||
}
|
||||
@@ -1,60 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name RootAccountUsage \
|
||||
# --filter-pattern '{ $.userIdentity.type = "Root" && $.userIdentity.invokedBy NOT EXISTS && $.eventType != "AwsServiceEvent" }' \
|
||||
# --metric-transformations metricName=RootAccountUsageEventCount,metricNamespace=CloudTrailMetrics,metricValue=1 \
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name RootAccountUsageAlarm \
|
||||
# --alarm-description "Triggered by AWS Root Account usage." \
|
||||
# --metric-name RootAccountUsageEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check33="3.3"
|
||||
CHECK_TITLE_check33="[check33] Ensure a log metric filter and alarm exist for usage of root account"
|
||||
CHECK_SCORED_check33="SCORED"
|
||||
CHECK_CIS_LEVEL_check33="LEVEL1"
|
||||
CHECK_SEVERITY_check33="Medium"
|
||||
CHECK_ASFF_TYPE_check33="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check33="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check303="check33"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check33="ens-op.exp.8.aws.trail.5"
|
||||
CHECK_SERVICENAME_check33="iam"
|
||||
CHECK_RISK_check33='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check33='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check33='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check33='Logging and Monitoring'
|
||||
|
||||
check33(){
|
||||
if [[ "${REGION}" == "us-gov-west-1" || "${REGION}" == "us-gov-east-1" ]]; then
|
||||
textInfo "${REGION}: This is an AWS GovCloud account and there is no root account to perform checks."
|
||||
else
|
||||
check3x '\$\.userIdentity\.type\s*=\s*"Root".+\$\.userIdentity\.invokedBy NOT EXISTS.+\$\.eventType\s*!=\s*"AwsServiceEvent"'
|
||||
fi
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name IAMAuthConfigChanges \
|
||||
# --filter-pattern '{ ($.eventName = DeleteGroupPolicy) || ($.eventName = DeleteRolePolicy) || ($.eventName = DeleteUserPolicy) || ($.eventName = PutGroupPolicy) || ($.eventName = PutRolePolicy) || ($.eventName = PutUserPolicy) || ($.eventName = CreatePolicy) || ($.eventName = DeletePolicy) || ($.eventName = CreatePolicyVersion) || ($.eventName = DeletePolicyVersion) || ($.eventName = AttachRolePolicy) || ($.eventName = DetachRolePolicy) || ($.eventName = AttachUserPolicy) || ($.eventName = DetachUserPolicy) || ($.eventName = AttachGroupPolicy) || ($.eventName = DetachGroupPolicy) }' \
|
||||
# --metric-transformations metricName=IAMPolicyEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name IAMAuthorizationActivityAlarm \
|
||||
# --alarm-description "Triggered by AWS IAM authorization config changes." \
|
||||
# --metric-name IAMPolicyEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check34="3.4"
|
||||
CHECK_TITLE_check34="[check34] Ensure a log metric filter and alarm exist for IAM policy changes"
|
||||
CHECK_SCORED_check34="SCORED"
|
||||
CHECK_CIS_LEVEL_check34="LEVEL1"
|
||||
CHECK_SEVERITY_check34="Medium"
|
||||
CHECK_ASFF_TYPE_check34="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check34="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check304="check34"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check34="ens-op.exp.8.aws.trail.6"
|
||||
CHECK_SERVICENAME_check34="iam"
|
||||
CHECK_RISK_check34='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check34='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check34='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check34='IAM'
|
||||
|
||||
check34(){
|
||||
check3x '\$\.eventName\s*=\s*DeleteGroupPolicy.+\$\.eventName\s*=\s*DeleteRolePolicy.+\$\.eventName\s*=\s*DeleteUserPolicy.+\$\.eventName\s*=\s*PutGroupPolicy.+\$\.eventName\s*=\s*PutRolePolicy.+\$\.eventName\s*=\s*PutUserPolicy.+\$\.eventName\s*=\s*CreatePolicy.+\$\.eventName\s*=\s*DeletePolicy.+\$\.eventName\s*=\s*CreatePolicyVersion.+\$\.eventName\s*=\s*DeletePolicyVersion.+\$\.eventName\s*=\s*AttachRolePolicy.+\$\.eventName\s*=\s*DetachRolePolicy.+\$\.eventName\s*=\s*AttachUserPolicy.+\$\.eventName\s*=\s*DetachUserPolicy.+\$\.eventName\s*=\s*AttachGroupPolicy.+\$\.eventName\s*=\s*DetachGroupPolicy'
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/MyCloudTrailLG \
|
||||
# --filter-name AWSCloudTrailChanges \
|
||||
# --filter-pattern '{ ($.eventName = CreateTrail) || ($.eventName = UpdateTrail) || ($.eventName = DeleteTrail) || ($.eventName = StartLogging) || ($.eventName = StopLogging) }' \
|
||||
# --metric-transformations metricName=CloudTrailEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name "CloudTrail Changes" \
|
||||
# --alarm-description "Triggered by AWS CloudTrail configuration changes." \
|
||||
# --metric-name CloudTrailEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check35="3.5"
|
||||
CHECK_TITLE_check35="[check35] Ensure a log metric filter and alarm exist for CloudTrail configuration changes"
|
||||
CHECK_SCORED_check35="SCORED"
|
||||
CHECK_CIS_LEVEL_check35="LEVEL1"
|
||||
CHECK_SEVERITY_check35="Medium"
|
||||
CHECK_ASFF_TYPE_check35="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check35="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check305="check35"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check35="ens-op.exp.8.aws.trail.1"
|
||||
CHECK_SERVICENAME_check35="cloudtrail"
|
||||
CHECK_RISK_check35='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check35='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check35='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check35='Logging and Monitoring'
|
||||
|
||||
check35(){
|
||||
check3x '\$\.eventName\s*=\s*CreateTrail.+\$\.eventName\s*=\s*UpdateTrail.+\$\.eventName\s*=\s*DeleteTrail.+\$\.eventName\s*=\s*StartLogging.+\$\.eventName\s*=\s*StopLogging'
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/MyCloudTrailLG \
|
||||
# --filter-name AWSConsoleSignInFailures \
|
||||
# --filter-pattern '{ ($.eventName = ConsoleLogin) && ($.errorMessage = "Failed authentication") }' \
|
||||
# --metric-transformations metricName=ConsoleSigninFailureCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name "Console Sign-in Failures" \
|
||||
# --alarm-description "AWS Management Console Sign-in Failure Alarm." \
|
||||
# --metric-name ConsoleSigninFailureCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 3 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check36="3.6"
|
||||
CHECK_TITLE_check36="[check36] Ensure a log metric filter and alarm exist for AWS Management Console authentication failures"
|
||||
CHECK_SCORED_check36="SCORED"
|
||||
CHECK_CIS_LEVEL_check36="LEVEL2"
|
||||
CHECK_SEVERITY_check36="Medium"
|
||||
CHECK_ASFF_TYPE_check36="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check36="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check306="check36"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check36="ens-op.exp.8.aws.trail.3"
|
||||
CHECK_SERVICENAME_check36="iam"
|
||||
CHECK_RISK_check36='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check36='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check36='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check36='Logging and Monitoring'
|
||||
|
||||
check36(){
|
||||
check3x '\$\.eventName\s*=\s*ConsoleLogin.+\$\.errorMessage\s*=\s*"Failed authentication"'
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name AWSCMKChanges \
|
||||
# --filter-pattern '{ ($.eventSource = kms.amazonaws.com) && (($.eventName = DisableKey) || ($.eventName = ScheduleKeyDeletion)) }' \
|
||||
# --metric-transformations metricName=CMKEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name AWSCMKChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS CMK changes." \
|
||||
# --metric-name CMKEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check37="3.7"
|
||||
CHECK_TITLE_check37="[check37] Ensure a log metric filter and alarm exist for disabling or scheduled deletion of customer created KMS CMKs"
|
||||
CHECK_SCORED_check37="SCORED"
|
||||
CHECK_CIS_LEVEL_check37="LEVEL2"
|
||||
CHECK_SEVERITY_check37="Medium"
|
||||
CHECK_ASFF_TYPE_check37="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check37="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check307="check37"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check37="ens-op.exp.11.aws.kms.1"
|
||||
CHECK_SERVICENAME_check37="kms"
|
||||
CHECK_RISK_check37='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check37='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check37='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check37='Logging and Monitoring'
|
||||
|
||||
check37(){
|
||||
check3x '\$\.eventSource\s*=\s*kms.amazonaws.com.+\$\.eventName\s*=\s*DisableKey.+\$\.eventName\s*=\s*ScheduleKeyDeletion'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name S3BucketConfigChanges \
|
||||
# --filter-pattern '{ ($.eventSource = s3.amazonaws.com) && (($.eventName = PutBucketAcl) || ($.eventName = PutBucketPolicy) || ($.eventName = PutBucketCors) || ($.eventName = PutBucketLifecycle) || ($.eventName = PutBucketReplication) || ($.eventName = DeleteBucketPolicy) || ($.eventName = DeleteBucketCors) || ($.eventName = DeleteBucketLifecycle) || ($.eventName = DeleteBucketReplication)) }' \
|
||||
# --metric-transformations metricName=S3BucketEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name S3BucketConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS S3 Bucket config changes." \
|
||||
# --metric-name S3BucketEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check38="3.8"
|
||||
CHECK_TITLE_check38="[check38] Ensure a log metric filter and alarm exist for S3 bucket policy changes"
|
||||
CHECK_SCORED_check38="SCORED"
|
||||
CHECK_CIS_LEVEL_check38="LEVEL1"
|
||||
CHECK_SEVERITY_check38="Medium"
|
||||
CHECK_ASFF_TYPE_check38="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check38="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check308="check38"
|
||||
CHECK_SERVICENAME_check38="s3"
|
||||
CHECK_RISK_check38='Monitoring unauthorized API calls will help reveal application errors and may reduce time to detect malicious activity.'
|
||||
CHECK_REMEDIATION_check38='It is recommended that a metric filter and alarm be established for unauthorized requests.'
|
||||
CHECK_DOC_check38='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check38='Logging and Monitoring'
|
||||
|
||||
check38(){
|
||||
check3x '\$\.eventSource\s*=\s*s3.amazonaws.com.+\$\.eventName\s*=\s*PutBucketAcl.+\$\.eventName\s*=\s*PutBucketPolicy.+\$\.eventName\s*=\s*PutBucketCors.+\$\.eventName\s*=\s*PutBucketLifecycle.+\$\.eventName\s*=\s*PutBucketReplication.+\$\.eventName\s*=\s*DeleteBucketPolicy.+\$\.eventName\s*=\s*DeleteBucketCors.+\$\.eventName\s*=\s*DeleteBucketLifecycle.+\$\.eventName\s*=\s*DeleteBucketReplication'
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
#
|
||||
# Remediation:
|
||||
#
|
||||
# https://d1.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf
|
||||
#
|
||||
# aws logs put-metric-filter \
|
||||
# --region us-east-1 \
|
||||
# --log-group-name CloudTrail/CloudWatchLogGroup \
|
||||
# --filter-name AWSConfigChanges \
|
||||
# --filter-pattern '{ ($.eventSource = config.amazonaws.com) && (($.eventName = StopConfigurationRecorder)||($.eventName = DeleteDeliveryChannel)||($.eventName = PutDeliveryChannel)||($.eventName = PutConfigurationRecorder)) }' \
|
||||
# --metric-transformations metricName=ConfigEventCount,metricNamespace=CloudTrailMetrics,metricValue=1
|
||||
#
|
||||
# aws cloudwatch put-metric-alarm \
|
||||
# --region us-east-1 \
|
||||
# --alarm-name AWSConfigChangesAlarm \
|
||||
# --alarm-description "Triggered by AWS Config changes." \
|
||||
# --metric-name ConfigEventCount \
|
||||
# --namespace CloudTrailMetrics \
|
||||
# --statistic Sum \
|
||||
# --comparison-operator GreaterThanOrEqualToThreshold \
|
||||
# --evaluation-periods 1 \
|
||||
# --period 300 \
|
||||
# --threshold 1 \
|
||||
# --actions-enabled \
|
||||
# --alarm-actions arn:aws:sns:us-east-1:123456789012:CloudWatchAlarmTopic
|
||||
|
||||
CHECK_ID_check39="3.9"
|
||||
CHECK_TITLE_check39="[check39] Ensure a log metric filter and alarm exist for AWS Config configuration changes"
|
||||
CHECK_SCORED_check39="SCORED"
|
||||
CHECK_CIS_LEVEL_check39="LEVEL2"
|
||||
CHECK_SEVERITY_check39="Medium"
|
||||
CHECK_ASFF_TYPE_check39="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check39="AwsCloudTrailTrail"
|
||||
CHECK_ALTERNATE_check309="check39"
|
||||
CHECK_SERVICENAME_check39="configservice"
|
||||
CHECK_RISK_check39='If not enabled important changes to accounts could go unnoticed or difficult to find.'
|
||||
CHECK_REMEDIATION_check39='Use this service as a complement to implement detective controls that cannot be prevented. (e.g. a Security Group is modified to open to internet without restrictions or route changed to avoid going thru the network firewall). Ensure AWS Config is enabled in all regions in order to detect any not intended action. On the other hand if sufficient preventive controls to make changes in critical services are in place; the rating on this finding can be lowered or discarded depending on residual risk.'
|
||||
CHECK_DOC_check39='https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudwatch-alarms-for-cloudtrail.html'
|
||||
CHECK_CAF_EPIC_check39='Logging and Monitoring'
|
||||
|
||||
check39(){
|
||||
check3x '\$\.eventSource\s*=\s*config.amazonaws.com.+\$\.eventName\s*=\s*StopConfigurationRecorder.+\$\.eventName\s*=\s*DeleteDeliveryChannel.+\$\.eventName\s*=\s*PutDeliveryChannel.+\$\.eventName\s*=\s*PutConfigurationRecorder'
|
||||
}
|
||||
@@ -1,45 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check41="4.1"
|
||||
CHECK_TITLE_check41="[check41] Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to port 22"
|
||||
CHECK_SCORED_check41="SCORED"
|
||||
CHECK_CIS_LEVEL_check41="LEVEL2"
|
||||
CHECK_SEVERITY_check41="High"
|
||||
CHECK_ASFF_TYPE_check41="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check41="AwsEc2SecurityGroup"
|
||||
CHECK_ALTERNATE_check401="check41"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check41="ens-mp.com.4.aws.sg.4"
|
||||
CHECK_SERVICENAME_check41="ec2"
|
||||
CHECK_RISK_check41='Even having a perimeter firewall; having security groups open allows any user or malware with vpc access to scan for well known and sensitive ports and gain access to instance.'
|
||||
CHECK_REMEDIATION_check41='Apply Zero Trust approach. Implement a process to scan and remediate unrestricted or overly permissive security groups. Recommended best practices is to narrow the definition for the minimum ports required.'
|
||||
CHECK_DOC_check41='https://docs.aws.amazon.com/eks/latest/userguide/sec-group-reqs.html'
|
||||
CHECK_CAF_EPIC_check41='Infrastructure Security'
|
||||
|
||||
check41(){
|
||||
# "Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to port 22 (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
SG_LIST=$("${AWSCLI}" ec2 describe-security-groups --query 'SecurityGroups[?length(IpPermissions[?((FromPort==null && ToPort==null) || (FromPort<=`22` && ToPort>=`22`)) && (contains(IpRanges[].CidrIp, `0.0.0.0/0`) || contains(Ipv6Ranges[].CidrIpv6, `::/0`)) && (IpProtocol==`tcp`)]) > `0`].{GroupId:GroupId}' $PROFILE_OPT --region "${regx}" --output text 2>&1)
|
||||
if [[ $(echo "$SG_LIST" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe security groups" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $SG_LIST ]];then
|
||||
for SG in $SG_LIST;do
|
||||
textFail "$regx: Found Security Group: $SG open to 0.0.0.0/0" "$regx" "$SG"
|
||||
done
|
||||
else
|
||||
textPass "$regx: No Security Groups found with port 22 TCP open to 0.0.0.0/0" "$regx" "$SG"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,45 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check42="4.2"
|
||||
CHECK_TITLE_check42="[check42] Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to port 3389"
|
||||
CHECK_SCORED_check42="SCORED"
|
||||
CHECK_CIS_LEVEL_check42="LEVEL2"
|
||||
CHECK_SEVERITY_check42="High"
|
||||
CHECK_ASFF_TYPE_check42="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check42="AwsEc2SecurityGroup"
|
||||
CHECK_ALTERNATE_check402="check42"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check42="ens-mp.com.4.aws.sg.5"
|
||||
CHECK_SERVICENAME_check42="ec2"
|
||||
CHECK_RISK_check42='Even having a perimeter firewall; having security groups open allows any user or malware with vpc access to scan for well known and sensitive ports and gain access to instance.'
|
||||
CHECK_REMEDIATION_check42='Apply Zero Trust approach. Implement a process to scan and remediate unrestricted or overly permissive security groups. Recommended best practices is to narrow the definition for the minimum ports required.'
|
||||
CHECK_DOC_check42='https://docs.aws.amazon.com/eks/latest/userguide/sec-group-reqs.html'
|
||||
CHECK_CAF_EPIC_check42='Infrastructure Security'
|
||||
|
||||
check42(){
|
||||
# "Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to port 3389 (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
SG_LIST=$("${AWSCLI}" ec2 describe-security-groups --query 'SecurityGroups[?length(IpPermissions[?((FromPort==null && ToPort==null) || (FromPort<=`3389` && ToPort>=`3389`)) && (contains(IpRanges[].CidrIp, `0.0.0.0/0`) || contains(Ipv6Ranges[].CidrIpv6, `::/0`)) && (IpProtocol==`tcp`) ]) > `0`].{GroupId:GroupId}' $PROFILE_OPT --region "${regx}" --output text 2>&1)
|
||||
if [[ $(echo "$SG_LIST" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe security groups" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $SG_LIST ]];then
|
||||
for SG in $SG_LIST;do
|
||||
textFail "$regx: Found Security Group: $SG open to 0.0.0.0/0" "$regx" "$SG"
|
||||
done
|
||||
else
|
||||
textPass "$regx: No Security Groups found with port 3389 TCP open to 0.0.0.0/0" "$regx" "$SG"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,46 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check43="4.3"
|
||||
CHECK_TITLE_check43="[check43] Ensure the default security group of every VPC restricts all traffic"
|
||||
CHECK_SCORED_check43="SCORED"
|
||||
CHECK_CIS_LEVEL_check43="LEVEL2"
|
||||
CHECK_SEVERITY_check43="High"
|
||||
CHECK_ASFF_TYPE_check43="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check43="AwsEc2SecurityGroup"
|
||||
CHECK_ALTERNATE_check403="check43"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_check43="ens-mp.com.4.aws.sg.1"
|
||||
CHECK_SERVICENAME_check43="ec2"
|
||||
CHECK_RISK_check43='Even having a perimeter firewall; having security groups open allows any user or malware with vpc access to scan for well known and sensitive ports and gain access to instance.'
|
||||
CHECK_REMEDIATION_check43='Apply Zero Trust approach. Implement a process to scan and remediate unrestricted or overly permissive security groups. Recommended best practices is to narrow the definition for the minimum ports required.'
|
||||
CHECK_DOC_check43='https://docs.aws.amazon.com/eks/latest/userguide/sec-group-reqs.html'
|
||||
CHECK_CAF_EPIC_check43='Infrastructure Security'
|
||||
|
||||
check43(){
|
||||
# "Ensure the default security group of every VPC restricts all traffic (Scored)"
|
||||
for regx in $REGIONS; do
|
||||
CHECK_SGDEFAULT_IDS=$($AWSCLI ec2 describe-security-groups $PROFILE_OPT --region $regx --filters Name=group-name,Values='default' --query 'SecurityGroups[*].GroupId[]' --output text 2>&1)
|
||||
if [[ $(echo "$CHECK_SGDEFAULT_IDS" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe security groups" "$regx"
|
||||
continue
|
||||
fi
|
||||
for CHECK_SGDEFAULT_ID in $CHECK_SGDEFAULT_IDS; do
|
||||
CHECK_SGDEFAULT_ID_OPEN=$($AWSCLI ec2 describe-security-groups $PROFILE_OPT --region $regx --group-ids $CHECK_SGDEFAULT_ID --query 'SecurityGroups[*].{IpPermissions:IpPermissions,IpPermissionsEgress:IpPermissionsEgress,GroupId:GroupId}' --output text |egrep '\s0.0.0.0|\:\:\/0')
|
||||
if [[ $CHECK_SGDEFAULT_ID_OPEN ]];then
|
||||
textFail "$regx: Default Security Groups ($CHECK_SGDEFAULT_ID) found that allow 0.0.0.0 IN or OUT traffic" "$regx" "$CHECK_SGDEFAULT_ID"
|
||||
else
|
||||
textPass "$regx: No Default Security Groups ($CHECK_SGDEFAULT_ID) open to 0.0.0.0 found" "$regx" "$CHECK_SGDEFAULT_ID"
|
||||
fi
|
||||
done
|
||||
done
|
||||
}
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check44="4.4"
|
||||
CHECK_TITLE_check44="[check44] Ensure routing tables for VPC peering are \"least access\""
|
||||
CHECK_SCORED_check44="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_check44="LEVEL2"
|
||||
CHECK_SEVERITY_check44="Medium"
|
||||
CHECK_ASFF_TYPE_check44="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check44="AwsEc2Vpc"
|
||||
CHECK_ALTERNATE_check404="check44"
|
||||
CHECK_SERVICENAME_check44="vpc"
|
||||
CHECK_RISK_check44='Being highly selective in peering routing tables is a very effective way of minimizing the impact of breach as resources outside of these routes are inaccessible to the peered VPC.'
|
||||
CHECK_REMEDIATION_check44='Review routing tables of peered VPCs for whether they route all subnets of each VPC and whether that is necessary to accomplish the intended purposes for peering the VPCs.'
|
||||
CHECK_DOC_check44='https://docs.aws.amazon.com/vpc/latest/peering/peering-configurations-partial-access.html'
|
||||
CHECK_CAF_EPIC_check44='Infrastructure Security'
|
||||
|
||||
check44(){
|
||||
# "Ensure routing tables for VPC peering are \"least access\" (Not Scored)"
|
||||
for regx in $REGIONS; do
|
||||
LIST_OF_VPCS_PEERING_CONNECTIONS=$($AWSCLI ec2 describe-vpc-peering-connections --output text $PROFILE_OPT --region $regx --query 'VpcPeeringConnections[*].VpcPeeringConnectionId' 2>&1| sort | paste -s -d" " - )
|
||||
if [[ $(echo "$LIST_OF_VPCS_PEERING_CONNECTIONS" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe vpc peering connections" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_OF_VPCS_PEERING_CONNECTIONS ]];then
|
||||
textInfo "$regx: $LIST_OF_VPCS_PEERING_CONNECTIONS - review routing tables" "$regx" "$LIST_OF_VPCS_PEERING_CONNECTIONS"
|
||||
#LIST_OF_VPCS=$($AWSCLI ec2 describe-vpcs $PROFILE_OPT --region $regx --query 'Vpcs[*].VpcId' --output text)
|
||||
#aws ec2 describe-route-tables --filter "Name=vpc-id,Values=vpc-0213e864" --query "RouteTables[*].{RouteTableId:RouteTableId, VpcId:VpcId, Routes:Routes, AssociatedSubnets:Associations[*].SubnetId}" $PROFILE_OPT --region $regx
|
||||
# for vpc in $LIST_OF_VPCS; do
|
||||
# VPCS_WITH_PEERING=$($AWSCLI ec2 describe-route-tables --filter "Name=vpc-id,Values=$vpc" $PROFILE_OPT --region $regx --query "RouteTables[*].{RouteTableId:RouteTableId, VpcId:VpcId, Routes:Routes, AssociatedSubnets:Associations[*].SubnetId}" |grep GatewayId|grep pcx-)
|
||||
# done
|
||||
#echo $VPCS_WITH_PEERING
|
||||
else
|
||||
textPass "$regx: No VPC peering found" "$regx" "$LIST_OF_VPCS_PEERING_CONNECTIONS"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,43 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check45="4.5"
|
||||
CHECK_TITLE_check45="[check45] Ensure no Network ACLs allow ingress from 0.0.0.0/0 to SSH port 22"
|
||||
CHECK_SCORED_check45="SCORED"
|
||||
CHECK_CIS_LEVEL_check45="LEVEL2"
|
||||
CHECK_SEVERITY_check45="High"
|
||||
CHECK_ASFF_TYPE_check45="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check45="AwsEc2NetworkAcl"
|
||||
CHECK_ALTERNATE_check401="check45"
|
||||
CHECK_SERVICENAME_check45="ec2"
|
||||
CHECK_RISK_check45='Even having a perimeter firewall; having network acls open allows any user or malware with vpc access to scan for well known and sensitive ports and gain access to instance.'
|
||||
CHECK_REMEDIATION_check45='Apply Zero Trust approach. Implement a process to scan and remediate unrestricted or overly permissive network acls. Recommended best practices is to narrow the definition for the minimum ports required.'
|
||||
CHECK_DOC_check45='https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html'
|
||||
CHECK_CAF_EPIC_check45='Infrastructure Security'
|
||||
|
||||
check45(){
|
||||
for regx in $REGIONS; do
|
||||
NACL_LIST=$($AWSCLI ec2 describe-network-acls --query 'NetworkAcls[?Entries[?(((!PortRange) || (PortRange.From<=`22` && PortRange.To>=`22`)) && ((CidrBlock == `0.0.0.0/0`) && (Egress == `false`) && (RuleAction == `allow`)))]].{NetworkAclId:NetworkAclId}' $PROFILE_OPT --region $regx --output text 2>&1)
|
||||
if [[ $(echo "$NACL_LIST" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe vpc network acls" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $NACL_LIST ]];then
|
||||
for NACL in $NACL_LIST;do
|
||||
textInfo "$regx: Found Network ACL: $NACL open to 0.0.0.0/0 for SSH port 22" "$regx" "$NACL"
|
||||
done
|
||||
else
|
||||
textPass "$regx: No Network ACL found with SSH port 22 open to 0.0.0.0/0" "$regx" "$NACL"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,43 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_check46="4.6"
|
||||
CHECK_TITLE_check46="[check46] Ensure no Network ACLs allow ingress from 0.0.0.0/0 to Microsoft RDP port 3389"
|
||||
CHECK_SCORED_check46="SCORED"
|
||||
CHECK_CIS_LEVEL_check46="LEVEL2"
|
||||
CHECK_SEVERITY_check46="High"
|
||||
CHECK_ASFF_TYPE_check46="Software and Configuration Checks/Industry and Regulatory Standards/CIS AWS Foundations Benchmark"
|
||||
CHECK_ASFF_RESOURCE_TYPE_check46="AwsEc2NetworkAcl"
|
||||
CHECK_ALTERNATE_check401="check46"
|
||||
CHECK_SERVICENAME_check46="ec2"
|
||||
CHECK_RISK_check46='Even having a perimeter firewall; having network acls open allows any user or malware with vpc access to scan for well known and sensitive ports and gain access to instance.'
|
||||
CHECK_REMEDIATION_check46='Apply Zero Trust approach. Implement a process to scan and remediate unrestricted or overly permissive network acls. Recommended best practices is to narrow the definition for the minimum ports required.'
|
||||
CHECK_DOC_check46='https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html'
|
||||
CHECK_CAF_EPIC_check46='Infrastructure Security'
|
||||
|
||||
check46(){
|
||||
for regx in $REGIONS; do
|
||||
NACL_LIST=$($AWSCLI ec2 describe-network-acls --query 'NetworkAcls[?Entries[?(((!PortRange) || (PortRange.From<=`3389` && PortRange.To>=`3389`)) && ((CidrBlock == `0.0.0.0/0`) && (Egress == `false`) && (RuleAction == `allow`)))]].{NetworkAclId:NetworkAclId}' $PROFILE_OPT --region $regx --output text 2>&1)
|
||||
if [[ $(echo "$NACL_LIST" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe vpc network acls" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $NACL_LIST ]];then
|
||||
for NACL in $NACL_LIST;do
|
||||
textInfo "$regx: Found Network ACL: $NACL open to 0.0.0.0/0 for Microsoft RDP port 3389" "$regx" "$NACL"
|
||||
done
|
||||
else
|
||||
textPass "$regx: No Network ACL found with Microsoft RDP port 3389 open to 0.0.0.0/0" "$regx" "$NACL"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,56 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra71="7.1"
|
||||
CHECK_TITLE_extra71="[extra71] Ensure users of groups with AdministratorAccess policy have MFA tokens enabled"
|
||||
CHECK_SCORED_extra71="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra71="EXTRA"
|
||||
CHECK_SEVERITY_extra71="High"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra71="AwsIamUser"
|
||||
CHECK_ALTERNATE_extra701="extra71"
|
||||
CHECK_ALTERNATE_check71="extra71"
|
||||
CHECK_ALTERNATE_check701="extra71"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_extra71="ens-op.exp.10.aws.trail.2"
|
||||
CHECK_SERVICENAME_extra71="iam"
|
||||
CHECK_RISK_extra71='Policy "may" allow Anonymous users to perform actions.'
|
||||
CHECK_REMEDIATION_extra71='Ensure this repository and its contents should be publicly accessible.'
|
||||
CHECK_DOC_extra71='https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_mfa_enable_virtual.html'
|
||||
CHECK_CAF_EPIC_extra71='Infrastructure Security'
|
||||
|
||||
extra71(){
|
||||
# "Ensure users of groups with AdministratorAccess policy have MFA tokens enabled "
|
||||
ADMIN_GROUPS=''
|
||||
AWS_GROUPS=$($AWSCLI $PROFILE_OPT iam list-groups --output text --region $REGION --query 'Groups[].GroupName')
|
||||
for grp in $AWS_GROUPS; do
|
||||
# aws --profile onlinetraining iam list-attached-group-policies --group-name Administrators --query 'AttachedPolicies[].PolicyArn' | grep 'arn:aws:iam::aws:policy/AdministratorAccess'
|
||||
# list-attached-group-policies
|
||||
CHECK_ADMIN_GROUP=$($AWSCLI $PROFILE_OPT --region $REGION iam list-attached-group-policies --group-name $grp --output json --query 'AttachedPolicies[].PolicyArn' | grep "arn:${AWS_PARTITION}:iam::aws:policy/AdministratorAccess")
|
||||
if [[ $CHECK_ADMIN_GROUP ]]; then
|
||||
ADMIN_GROUPS="$ADMIN_GROUPS $grp"
|
||||
textInfo "$REGION: $grp group provides administrative access" "$REGION" "$grp"
|
||||
ADMIN_USERS=$($AWSCLI $PROFILE_OPT iam get-group --region $REGION --group-name $grp --output json --query 'Users[].UserName' | grep '"' | cut -d'"' -f2 )
|
||||
for auser in $ADMIN_USERS; do
|
||||
# users in group are Administrators
|
||||
# users
|
||||
# check for user MFA device in credential report
|
||||
USER_MFA_ENABLED=$( cat $TEMP_REPORT_FILE | grep "^$auser," | cut -d',' -f8)
|
||||
if [[ "true" == $USER_MFA_ENABLED ]]; then
|
||||
textPass "$REGION: $auser / MFA Enabled / admin via group $grp" "$REGION" "$grp"
|
||||
else
|
||||
textFail "$REGION: $auser / MFA DISABLED / admin via group $grp" "$REGION" "$grp"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$REGION: $grp group provides non-administrative access" "$REGION" "$grp"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,45 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra710="7.10"
|
||||
CHECK_TITLE_extra710="[extra710] Check for internet facing EC2 Instances"
|
||||
CHECK_SCORED_extra710="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra710="EXTRA"
|
||||
CHECK_SEVERITY_extra710="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra710="AwsEc2Instance"
|
||||
CHECK_ALTERNATE_check710="extra710"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_extra710="ens-mp.com.4.aws.vpc.1"
|
||||
CHECK_SERVICENAME_extra710="ec2"
|
||||
CHECK_RISK_extra710='Exposing an EC2 directly to internet increases the attack surface and therefore the risk of compromise.'
|
||||
CHECK_REMEDIATION_extra710='Use an ALB and apply WAF ACL.'
|
||||
CHECK_DOC_extra710='https://aws.amazon.com/blogs/aws/aws-web-application-firewall-waf-for-application-load-balancers/'
|
||||
CHECK_CAF_EPIC_extra710='Infrastructure Security'
|
||||
|
||||
extra710(){
|
||||
# "Check for internet facing EC2 Instances "
|
||||
for regx in $REGIONS; do
|
||||
LIST_OF_PUBLIC_INSTANCES=$($AWSCLI ec2 describe-instances $PROFILE_OPT --region $regx --query 'Reservations[*].Instances[?PublicIpAddress].[InstanceId,PublicIpAddress]' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_OF_PUBLIC_INSTANCES" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe instances" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_OF_PUBLIC_INSTANCES ]];then
|
||||
while read -r instance;do
|
||||
INSTANCE_ID=$(echo $instance | awk '{ print $1; }')
|
||||
PUBLIC_IP=$(echo $instance | awk '{ print $2; }')
|
||||
textFail "$regx: Instance: $INSTANCE_ID at IP: $PUBLIC_IP is internet-facing!" "$regx" "$INSTANCE_ID"
|
||||
done <<< "$LIST_OF_PUBLIC_INSTANCES"
|
||||
else
|
||||
textPass "$regx: no Internet Facing EC2 Instances found" "$regx" "$INSTANCE_ID"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,82 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2019) by Toni de la Fuente
|
||||
#
|
||||
# This check was contributed by Nick Malcolm (github.com/nickmalcolm), building
|
||||
# on the hard work of others.
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7100="7.100"
|
||||
CHECK_TITLE_extra7100="[extra7100] Ensure that no custom IAM policies exist which allow permissive role assumption (e.g. sts:AssumeRole on *)"
|
||||
CHECK_SCORED_extra7100="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7100="EXTRA"
|
||||
CHECK_SEVERITY_extra7100="Critical"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7100="AwsIamPolicy"
|
||||
CHECK_ALTERNATE_check7100="extra7100"
|
||||
CHECK_ASFF_COMPLIANCE_TYPE_extra7100="ens-op.acc.2.aws.iam.1"
|
||||
CHECK_SERVICENAME_extra7100="iam"
|
||||
CHECK_RISK_extra7100='If not restricted unintended access could happen.'
|
||||
CHECK_REMEDIATION_extra7100='Use the least privilege principle when granting permissions.'
|
||||
CHECK_DOC_extra7100='https://docs.aws.amazon.com/STS/latest/APIReference/API_AssumeRole.html'
|
||||
CHECK_CAF_EPIC_extra7100='IAM'
|
||||
|
||||
extra7100(){
|
||||
# "Ensure that no custom policies exist which permit assuming any role (e.g. sts:AssumeRole on *)"
|
||||
#
|
||||
# A permissive STS Role assumption policy is one where the Resource (ARN) is not explicitly defined
|
||||
# This is most often seen as sts:assumeRole on *, but can take other forms.
|
||||
#
|
||||
# Learn more: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_permissions-to-switch.html#roles-usingrole-createpolicy
|
||||
LIST_CUSTOM_POLICIES=$($AWSCLI iam list-policies --output text $PROFILE_OPT --region $REGION --scope Local --query 'Policies[*].[Arn,DefaultVersionId]' | grep -v -e '^None$' | awk -F '\t' '{print $1","$2"\n"}')
|
||||
if [[ $LIST_CUSTOM_POLICIES ]]; then
|
||||
for policy in $LIST_CUSTOM_POLICIES; do
|
||||
POLICY_ARN=$(echo $policy | awk -F ',' '{print $1}')
|
||||
POLICY_VERSION=$(echo $policy | awk -F ',' '{print $2}')
|
||||
|
||||
POLICY_STATEMENTS_WITH_ALLOW=$($AWSCLI iam get-policy-version \
|
||||
--output json \
|
||||
--policy-arn $POLICY_ARN \
|
||||
--version-id $POLICY_VERSION \
|
||||
--query "[PolicyVersion.Document.Statement] | [] | [?Effect == 'Allow']" \
|
||||
$PROFILE_OPT \
|
||||
--region $REGION
|
||||
)
|
||||
|
||||
# Identify permissive policies by:
|
||||
# 1 & 2) Casting all the Resource and Action keys to Arrays (sometimes they're a single string)
|
||||
# 3) Iterate over the policy statements
|
||||
# 4) Narrow the scope to Actions which are sts:* or sts:assumeRole(WithSAML|WithWebIdentity)
|
||||
# 5) Narrow the scope to Resources (IAM Roles) which include a wildcard
|
||||
POLICY_WITH_PERMISSIVE_STS=$(echo $POLICY_STATEMENTS_WITH_ALLOW \
|
||||
| jq 'map( .Resource |= (if type=="array" then . else [.] end) )' \
|
||||
| jq 'map( .Action |= (if type=="array" then . else [.] end) )' \
|
||||
| jq '.[]' \
|
||||
| jq 'select(.Action[] | contains("sts:AssumeRole") or contains("sts:*"))' \
|
||||
| jq 'select(.Resource[] | contains("*"))')
|
||||
|
||||
if [[ $POLICY_WITH_PERMISSIVE_STS ]]; then
|
||||
PERMISSIVE_POLICIES_LIST="$PERMISSIVE_POLICIES_LIST $POLICY_ARN"
|
||||
fi
|
||||
|
||||
done
|
||||
if [[ $PERMISSIVE_POLICIES_LIST ]]; then
|
||||
textInfo "STS AssumeRole Policies should only include the complete ARNs for the Roles that the user needs"
|
||||
textInfo "Learn more: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_permissions-to-switch.html#roles-usingrole-createpolicy"
|
||||
for policy in $PERMISSIVE_POLICIES_LIST; do
|
||||
textFail "$REGION: Policy $policy allows permissive STS Role assumption" "$REGION" "$policy"
|
||||
done
|
||||
else
|
||||
textPass "$REGION: No custom policies found that allow permissive STS Role assumption" "$REGION"
|
||||
fi
|
||||
else
|
||||
textPass "$REGION: No custom policies found" "$REGION"
|
||||
fi
|
||||
}
|
||||
@@ -1,51 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7101="7.101"
|
||||
CHECK_TITLE_extra7101="[extra7101] Check if Amazon Elasticsearch Service (ES) domains have audit logging enabled"
|
||||
CHECK_SCORED_extra7101="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7101="EXTRA"
|
||||
CHECK_SEVERITY_extra7101="Low"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7101="AwsElasticsearchDomain"
|
||||
CHECK_ALTERNATE_check7101="extra7101"
|
||||
CHECK_SERVICENAME_extra7101="es"
|
||||
CHECK_RISK_extra7101='If logs are not enabled; monitoring of service use and threat analysis is not possible.'
|
||||
CHECK_REMEDIATION_extra7101='Make sure you are logging information about Amazon Elasticsearch Service operations.'
|
||||
CHECK_DOC_extra7101='https://docs.aws.amazon.com/elasticsearch-service/latest/developerguide/audit-logs.html'
|
||||
CHECK_CAF_EPIC_extra7101='Logging and Monitoring'
|
||||
|
||||
extra7101(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_OF_DOMAINS=$("${AWSCLI}" es list-domain-names ${PROFILE_OPT} --region "${regx}" --query 'DomainNames[].DomainName' --output text 2>&1)
|
||||
if [[ $(echo "${LIST_OF_DOMAINS}" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "${regx}: Access Denied trying to list domain names" "${regx}"
|
||||
continue
|
||||
fi
|
||||
if [[ "${LIST_OF_DOMAINS}" ]]; then
|
||||
for domain in ${LIST_OF_DOMAINS}; do
|
||||
AUDIT_LOGS_ENABLED=$("${AWSCLI}" es describe-elasticsearch-domain-config --domain-name "${domain}" ${PROFILE_OPT} --region "${regx}" --query 'DomainConfig.LogPublishingOptions.Options.AUDIT_LOGS.Enabled' --output text 2>&1)
|
||||
if [[ $(echo "${AUDIT_LOGS_ENABLED}" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "${regx}: Access Denied trying to get ES domain config for ${domain}" "${regx}"
|
||||
continue
|
||||
fi
|
||||
if [[ $(tr '[:upper:]' '[:lower:]' <<< "${AUDIT_LOGS_ENABLED}") == "true" ]]; then
|
||||
textPass "${regx}: Amazon ES domain ${domain} AUDIT_LOGS enabled" "${regx}" "${domain}"
|
||||
else
|
||||
textFail "${regx}: Amazon ES domain ${domain} AUDIT_LOGS disabled!" "${regx}" "${domain}"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Amazon ES domain found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,62 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra7102="7.102"
|
||||
CHECK_TITLE_extra7102="[extra7102] Check if any of the Elastic or Public IP are in Shodan (requires Shodan API KEY)"
|
||||
CHECK_SCORED_extra7102="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7102="EXTRA"
|
||||
CHECK_SEVERITY_extra7102="High"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7102="AwsEc2Eip"
|
||||
CHECK_ALTERNATE_check7102="extra7102"
|
||||
CHECK_SERVICENAME_extra7102="ec2"
|
||||
CHECK_RISK_extra7102='Sites like Shodan index exposed systems and further expose them to wider audiences as a quick way to find exploitable systems.'
|
||||
CHECK_REMEDIATION_extra7102='Check Identified IPs; consider changing them to private ones and delete them from Shodan.'
|
||||
CHECK_DOC_extra7102='https://www.shodan.io/'
|
||||
CHECK_CAF_EPIC_extra7102='Infrastructure Security'
|
||||
|
||||
# Watch out, always use Shodan API key, if you use `curl https://www.shodan.io/host/{ip}` massively
|
||||
# your IP will be banned by Shodan
|
||||
|
||||
# This is the right way to do so
|
||||
# curl -ks https://api.shodan.io/shodan/host/{ip}?key={YOUR_API_KEY}
|
||||
|
||||
# Each finding will be saved in prowler/output folder for further review.
|
||||
|
||||
extra7102(){
|
||||
if [[ ! $SHODAN_API_KEY ]]; then
|
||||
textInfo "[extra7102] Requires a Shodan API key to work. Use -N <shodan_api_key>"
|
||||
else
|
||||
for regx in $REGIONS; do
|
||||
LIST_OF_EIP=$($AWSCLI $PROFILE_OPT --region $regx ec2 describe-network-interfaces --query 'NetworkInterfaces[*].Association.PublicIp' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_OF_EIP" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe network interfaces" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_OF_EIP ]]; then
|
||||
for ip in $LIST_OF_EIP;do
|
||||
SHODAN_QUERY=$(curl -ks https://api.shodan.io/shodan/host/$ip?key=$SHODAN_API_KEY)
|
||||
# Shodan has a request rate limit of 1 request/second.
|
||||
sleep 1
|
||||
if [[ $SHODAN_QUERY == *"No information available for that IP"* ]]; then
|
||||
textPass "$regx: IP $ip is not listed in Shodan" "$regx"
|
||||
else
|
||||
echo $SHODAN_QUERY > $OUTPUT_DIR/shodan-output-$ip.json
|
||||
IP_SHODAN_INFO=$(cat $OUTPUT_DIR/shodan-output-$ip.json | jq -r '. | { ports: .ports, org: .org, country: .country_name }| @text' | tr -d \"\{\}\}\]\[ | tr , '\ ' )
|
||||
textFail "$regx: IP $ip is listed in Shodan with data $IP_SHODAN_INFO. More info https://www.shodan.io/host/$ip and $OUTPUT_DIR/shodan-output-$ip.json" "$regx" "$ip"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: No Public or Elastic IPs found" "$regx"
|
||||
fi
|
||||
done
|
||||
fi
|
||||
}
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7103="7.103"
|
||||
CHECK_TITLE_extra7103="[extra7103] Check if Amazon SageMaker Notebook instances have root access disabled"
|
||||
CHECK_SCORED_extra7103="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7103="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7103="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7103="extra7103"
|
||||
CHECK_SEVERITY_extra7103="Medium"
|
||||
CHECK_SERVICENAME_extra7103="sagemaker"
|
||||
CHECK_RISK_extra7103='Users with root access have administrator privileges; users can access and edit all files on a notebook instance with root access enabled.'
|
||||
CHECK_REMEDIATION_extra7103='set the RootAccess field to Disabled. You can also disable root access for users when you create or update a notebook instance in the Amazon SageMaker console.'
|
||||
CHECK_DOC_extra7103='https://docs.aws.amazon.com/sagemaker/latest/dg/nbi-root-access.html'
|
||||
CHECK_CAF_EPIC_extra7103='IAM'
|
||||
|
||||
extra7103(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_INSTANCES=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-notebook-instances --query 'NotebookInstances[*].NotebookInstanceName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_INSTANCES" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list notebook instances" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_INSTANCES ]];then
|
||||
for nb_instance in $LIST_SM_NB_INSTANCES; do
|
||||
SM_NB_ROOTACCESS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-notebook-instance --notebook-instance-name $nb_instance --query 'RootAccess' --output text)
|
||||
if [[ "${SM_NB_ROOTACCESS}" == "Enabled" ]]; then
|
||||
textFail "${regx}: Sagemaker Notebook instance $nb_instance has root access enabled" "${regx}" "$nb_instance"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Notebook instance $nb_instance has root access disabled" "${regx}" "$nb_instance"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Notebook instances found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
@@ -1,47 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7104="7.104"
|
||||
CHECK_TITLE_extra7104="[extra7104] Check if Amazon SageMaker Notebook instances have VPC settings configured"
|
||||
CHECK_SCORED_extra7104="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7104="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7104="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7104="extra7104"
|
||||
CHECK_SEVERITY_extra7104="Medium"
|
||||
CHECK_SERVICENAME_extra7104="sagemaker"
|
||||
CHECK_RISK_extra7104='This could provide an avenue for unauthorized access to your data.'
|
||||
CHECK_REMEDIATION_extra7104='Restrict which traffic can access by launching Studio in a Virtual Private Cloud (VPC) of your choosing.'
|
||||
CHECK_DOC_extra7104='https://docs.aws.amazon.com/sagemaker/latest/dg/studio-notebooks-and-internet-access.html'
|
||||
CHECK_CAF_EPIC_extra7104='Infrastructure Security'
|
||||
|
||||
extra7104(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_INSTANCES=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-notebook-instances --query 'NotebookInstances[*].NotebookInstanceName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_INSTANCES" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list notebook instances" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_INSTANCES ]];then
|
||||
for nb_instance in $LIST_SM_NB_INSTANCES; do
|
||||
SM_NB_SUBNETID=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-notebook-instance --notebook-instance-name $nb_instance --query 'SubnetId' --output text)
|
||||
if [[ "${SM_NB_SUBNETID}" == "None" ]]; then
|
||||
textFail "${regx}: Sagemaker Notebook instance $nb_instance has VPC settings disabled" "${regx}" "$nb_instance"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Notebook instance $nb_instance is in a VPC" "${regx}" "$nb_instance"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Notebook instances found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7105="7.105"
|
||||
CHECK_TITLE_extra7105="[extra7105] Check if Amazon SageMaker Models have network isolation enabled"
|
||||
CHECK_SCORED_extra7105="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7105="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7105="AwsSageMakerModel"
|
||||
CHECK_ALTERNATE_check7105="extra7105"
|
||||
CHECK_SEVERITY_extra7105="Medium"
|
||||
CHECK_SERVICENAME_extra7105="sagemaker"
|
||||
CHECK_RISK_extra7105='This could provide an avenue for unauthorized access to your data.'
|
||||
CHECK_REMEDIATION_extra7105='Restrict which traffic can access by launching Studio in a Virtual Private Cloud (VPC) of your choosing.'
|
||||
CHECK_DOC_extra7105='https://docs.aws.amazon.com/sagemaker/latest/dg/studio-notebooks-and-internet-access.html'
|
||||
CHECK_CAF_EPIC_extra7105='Infrastructure Security'
|
||||
|
||||
extra7105(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_MODELS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-models --query 'Models[*].ModelName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_MODELS" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list models" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_MODELS ]];then
|
||||
for nb_model_name in $LIST_SM_NB_MODELS; do
|
||||
SM_NB_NETWORKISOLATION=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-model --model-name $nb_model_name --query 'EnableNetworkIsolation' --output text)
|
||||
if [[ $SM_NB_NETWORKISOLATION == False ]]; then
|
||||
textFail "${regx}: SageMaker Model $nb_model_name has network isolation disabled" "${regx}" "$nb_model_name"
|
||||
else
|
||||
textPass "${regx}: SageMaker Model $nb_model_name has network isolation enabled" "${regx}" "$nb_model_name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Models found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7106="7.106"
|
||||
CHECK_TITLE_extra7106="[extra7106] Check if Amazon SageMaker Models have VPC settings configured"
|
||||
CHECK_SCORED_extra7106="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7106="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7106="AwsSageMakerModel"
|
||||
CHECK_ALTERNATE_check7106="extra7106"
|
||||
CHECK_SEVERITY_extra7106="Medium"
|
||||
CHECK_SERVICENAME_extra7106="sagemaker"
|
||||
CHECK_RISK_extra7106='This could provide an avenue for unauthorized access to your data.'
|
||||
CHECK_REMEDIATION_extra7106='Restrict which traffic can access by launching Studio in a Virtual Private Cloud (VPC) of your choosing.'
|
||||
CHECK_DOC_extra7106='https://docs.aws.amazon.com/sagemaker/latest/dg/studio-notebooks-and-internet-access.html'
|
||||
CHECK_CAF_EPIC_extra7106='Infrastructure Security'
|
||||
|
||||
extra7106(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_MODELS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-models --query 'Models[*].ModelName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_MODELS" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list models" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_MODELS ]];then
|
||||
for nb_model_name in $LIST_SM_NB_MODELS; do
|
||||
SM_NB_VPCCONFIG=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-model --model-name $nb_model_name --query 'VpcConfig.Subnets' --output text)
|
||||
if [[ $SM_NB_VPCCONFIG == "None" ]]; then
|
||||
textFail "${regx}: Amazon SageMaker Model $nb_model_name has VPC settings disabled" "${regx}" "$nb_model_name"
|
||||
else
|
||||
textPass "${regx}: Amazon SageMaker Model $nb_model_name has VPC settings enabled" "${regx}" "$nb_model_name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Models found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7107="7.107"
|
||||
CHECK_TITLE_extra7107="[extra7107] Check if Amazon SageMaker Training jobs have intercontainer encryption enabled"
|
||||
CHECK_SCORED_extra7107="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7107="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7107="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7107="extra7107"
|
||||
CHECK_SEVERITY_extra7107="Medium"
|
||||
CHECK_SERVICENAME_extra7107="sagemaker"
|
||||
CHECK_RISK_extra7107='If not restricted unintended access could happen.'
|
||||
CHECK_REMEDIATION_extra7107='Internetwork communications support TLS 1.2 encryption between all components and clients.'
|
||||
CHECK_DOC_extra7107='https://docs.aws.amazon.com/sagemaker/latest/dg/interface-vpc-endpoint.html'
|
||||
CHECK_CAF_EPIC_extra7107='Data Protection'
|
||||
|
||||
extra7107(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_JOBS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-training-jobs --query 'TrainingJobSummaries[*].TrainingJobName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_JOBS" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list training jobs" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_JOBS ]];then
|
||||
for nb_job_name in $LIST_SM_NB_JOBS; do
|
||||
SM_NB_INTERCONTAINERENCRYPTION=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-training-job --training-job-name $nb_job_name --query 'EnableInterContainerTrafficEncryption' --output text)
|
||||
if [[ $SM_NB_INTERCONTAINERENCRYPTION == "False" ]]; then
|
||||
textFail "${regx}: SageMaker Training job $nb_job_name has intercontainer encryption disabled" "${regx}" "$nb_job_name"
|
||||
else
|
||||
textPass "${regx}: SageMaker Training jobs $nb_job_name has intercontainer encryption enabled" "${regx}" "$nb_job_name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Training found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
@@ -1,47 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7108="7.108"
|
||||
CHECK_TITLE_extra7108="[extra7108] Check if Amazon SageMaker Training jobs have volume and output with KMS encryption enabled"
|
||||
CHECK_SCORED_extra7108="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7108="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7108="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7108="extra7108"
|
||||
CHECK_SEVERITY_extra7108="Medium"
|
||||
CHECK_SERVICENAME_extra7108="sagemaker"
|
||||
CHECK_RISK_extra7108='Data exfiltration could happen if information is not protected. KMS keys provide additional security level to IAM policies.'
|
||||
CHECK_REMEDIATION_extra7108='Specify AWS KMS keys to use for input and output from S3 and EBS.'
|
||||
CHECK_DOC_extra7108='https://docs.aws.amazon.com/sagemaker/latest/dg/key-management.html'
|
||||
CHECK_CAF_EPIC_extra7108='Data Protection'
|
||||
|
||||
extra7108(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_JOBS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-training-jobs --query 'TrainingJobSummaries[*].TrainingJobName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_JOBS" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list training jobs" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_JOBS ]];then
|
||||
for nb_job_name in $LIST_SM_NB_JOBS; do
|
||||
SM_JOB_KMSENCRYPTION=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-training-job --training-job-name $nb_job_name --query 'ResourceConfig.VolumeKmsKeyId' --output text)
|
||||
if [[ "${SM_JOB_KMSENCRYPTION}" == "None" ]];then
|
||||
textFail "${regx}: Sagemaker Trainings job $nb_job_name has KMS encryption disabled" "${regx}" "$nb_job_name"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Trainings job $nb_job_name has KSM encryption enabled" "${regx}" "$nb_job_name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Trainings jobs found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7109="7.109"
|
||||
CHECK_TITLE_extra7109="[extra7109] Check if Amazon SageMaker Training jobs have network isolation enabled"
|
||||
CHECK_SCORED_extra7109="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7109="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7109="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7109="extra7109"
|
||||
CHECK_SEVERITY_extra7109="Medium"
|
||||
CHECK_SERVICENAME_extra7109="sagemaker"
|
||||
CHECK_RISK_extra7109='This could provide an avenue for unauthorized access to your data.'
|
||||
CHECK_REMEDIATION_extra7109='Restrict which traffic can access by launching Studio in a Virtual Private Cloud (VPC) of your choosing.'
|
||||
CHECK_DOC_extra7109='https://docs.aws.amazon.com/sagemaker/latest/dg/interface-vpc-endpoint.html'
|
||||
CHECK_CAF_EPIC_extra7109='Infrastructure Security'
|
||||
|
||||
extra7109(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_JOBS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-training-jobs --query 'TrainingJobSummaries[*].TrainingJobName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_JOBS" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list training jobs" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_JOBS ]];then
|
||||
for nb_job_name in $LIST_SM_NB_JOBS; do
|
||||
SM_NB_NETWORKISOLATION=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-training-job --training-job-name $nb_job_name --query 'EnableNetworkIsolation' --output text)
|
||||
if [[ $SM_NB_NETWORKISOLATION == False ]]; then
|
||||
textFail "${regx}: Sagemaker Training job $nb_job_name has network isolation disabled" "${regx}" "$nb_job_name"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Training job $nb_job_name has network isolation enabled" "${regx}" "$nb_job_name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Trainings jobs found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
@@ -1,44 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra711="7.11"
|
||||
CHECK_TITLE_extra711="[extra711] Check for Publicly Accessible Redshift Clusters"
|
||||
CHECK_SCORED_extra711="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra711="EXTRA"
|
||||
CHECK_SEVERITY_extra711="High"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra711="AwsRedshiftCluster"
|
||||
CHECK_ALTERNATE_check711="extra711"
|
||||
CHECK_SERVICENAME_extra711="redshift"
|
||||
CHECK_RISK_extra711='Publicly accessible services could expose sensitive data to bad actors.'
|
||||
CHECK_REMEDIATION_extra711='List all shared Redshift clusters and make sure there is a business reason for them.'
|
||||
CHECK_DOC_extra711='https://docs.aws.amazon.com/redshift/latest/mgmt/managing-clusters-vpc.html'
|
||||
CHECK_CAF_EPIC_extra711='Data Protection'
|
||||
|
||||
extra711(){
|
||||
# "Check for Publicly Accessible Redshift Clusters "
|
||||
for regx in $REGIONS; do
|
||||
LIST_OF_PUBLIC_REDSHIFT_CLUSTERS=$($AWSCLI redshift describe-clusters $PROFILE_OPT --region $regx --query 'Clusters[?PubliclyAccessible == `true`].[ClusterIdentifier,Endpoint.Address]' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_OF_PUBLIC_REDSHIFT_CLUSTERS" | grep -E 'AccessDenied|UnauthorizedOperation') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe clusters" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_OF_PUBLIC_REDSHIFT_CLUSTERS ]];then
|
||||
while read -r cluster;do
|
||||
CLUSTER_ID=$(echo $cluster | awk '{ print $1; }')
|
||||
CLUSTER_ENDPOINT=$(echo $cluster | awk '{ print $2; }')
|
||||
textFail "$regx: Cluster: $CLUSTER_ID at Endpoint: $CLUSTER_ENDPOINT is publicly accessible!" "$regx" "$CLUSTER_ID"
|
||||
done <<< "$LIST_OF_PUBLIC_REDSHIFT_CLUSTERS"
|
||||
else
|
||||
textPass "$regx: no Publicly Accessible Redshift Clusters found" "$regx" "$CLUSTER_ID"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,48 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7110="7.110"
|
||||
CHECK_TITLE_extra7110="[extra7110] Check if Amazon SageMaker Training job have VPC settings configured."
|
||||
CHECK_SCORED_extra7110="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7110="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7110="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7110="extra7110"
|
||||
CHECK_SEVERITY_extra7110="Medium"
|
||||
CHECK_SERVICENAME_extra7110="sagemaker"
|
||||
CHECK_RISK_extra7110='This could provide an avenue for unauthorized access to your data.'
|
||||
CHECK_REMEDIATION_extra7110='Restrict which traffic can access by launching Studio in a Virtual Private Cloud (VPC) of your choosing.'
|
||||
CHECK_DOC_extra7110='https://docs.aws.amazon.com/sagemaker/latest/dg/interface-vpc-endpoint.html'
|
||||
CHECK_CAF_EPIC_extra7110='Infrastructure Security'
|
||||
|
||||
extra7110(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_JOBS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-training-jobs --query 'TrainingJobSummaries[*].TrainingJobName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_JOBS" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list training jobs" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_JOBS ]];then
|
||||
for nb_job_name in $LIST_SM_NB_JOBS; do
|
||||
SM_NB_SUBNETS=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-training-job --training-job-name $nb_job_name --query 'VpcConfig.Subnets' --output text)
|
||||
if [[ $SM_NB_SUBNETS == "None" ]]; then
|
||||
textFail "${regx}: Sagemaker Training job $nb_job_name has VPC settings for the training job volume and output disabled" "${regx}" "$nb_job_name"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Training job $nb_job_name has VPC settings for the training job volume and output enabled" "${regx}" "$nb_job_name"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Trainings jobs found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
@@ -1,47 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7111="7.111"
|
||||
CHECK_TITLE_extra7111="[extra7111] Check if Amazon SageMaker Notebook instances have direct internet access"
|
||||
CHECK_SCORED_extra7111="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7111="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7111="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7111="extra7111"
|
||||
CHECK_SEVERITY_extra7111="Medium"
|
||||
CHECK_SERVICENAME_extra7111="sagemaker"
|
||||
CHECK_RISK_extra7111='This could provide an avenue for unauthorized access to your data.'
|
||||
CHECK_REMEDIATION_extra7111='Restrict which traffic can access by launching Studio in a Virtual Private Cloud (VPC) of your choosing.'
|
||||
CHECK_DOC_extra7111='https://docs.aws.amazon.com/sagemaker/latest/dg/interface-vpc-endpoint.html'
|
||||
CHECK_CAF_EPIC_extra7111='Infrastructure Security'
|
||||
|
||||
extra7111(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_INSTANCES=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-notebook-instances --query 'NotebookInstances[*].NotebookInstanceName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_INSTANCES" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list notebook instances" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_INSTANCES ]];then
|
||||
for nb_instance in $LIST_SM_NB_INSTANCES; do
|
||||
SM_NB_DIRECTINET=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-notebook-instance --notebook-instance-name $nb_instance --query 'DirectInternetAccess' --output text)
|
||||
if [[ "${SM_NB_DIRECTINET}" == "Enabled" ]]; then
|
||||
textFail "${regx}: Sagemaker Notebook instance $nb_instance has direct internet access enabled" "${regx}" "$nb_instance"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Notebook instance $nb_instance has direct internet access disabled" "${regx}" "$nb_instance"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Notebook instances found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,47 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2020) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7112="7.112"
|
||||
CHECK_TITLE_extra7112="[extra7112] Check if Amazon SageMaker Notebook instances have data encryption enabled"
|
||||
CHECK_SCORED_extra7112="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7112="EXTRA"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7112="AwsSageMakerNotebookInstance"
|
||||
CHECK_ALTERNATE_check7112="extra7112"
|
||||
CHECK_SEVERITY_extra7112="Medium"
|
||||
CHECK_SERVICENAME_extra7112="sagemaker"
|
||||
CHECK_RISK_extra7112='Data exfiltration could happen if information is not protected. KMS keys provide additional security level to IAM policies.'
|
||||
CHECK_REMEDIATION_extra7112='Specify AWS KMS keys to use for input and output from S3 and EBS.'
|
||||
CHECK_DOC_extra7112='https://docs.aws.amazon.com/sagemaker/latest/dg/key-management.html'
|
||||
CHECK_CAF_EPIC_extra7112='Data Protection'
|
||||
|
||||
extra7112(){
|
||||
for regx in ${REGIONS}; do
|
||||
LIST_SM_NB_INSTANCES=$($AWSCLI $PROFILE_OPT --region $regx sagemaker list-notebook-instances --query 'NotebookInstances[*].NotebookInstanceName' --output text 2>&1)
|
||||
if [[ $(echo "$LIST_SM_NB_INSTANCES" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to list notebook instances" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_SM_NB_INSTANCES ]];then
|
||||
for nb_instance in $LIST_SM_NB_INSTANCES; do
|
||||
SM_NB_KMSKEY=$($AWSCLI $PROFILE_OPT --region $regx sagemaker describe-notebook-instance --notebook-instance-name $nb_instance --query 'KmsKeyId' --output text)
|
||||
if [[ "${SM_NB_KMSKEY}" == "None" ]]; then
|
||||
textFail "${regx}: Sagemaker Notebook instance $nb_instance has data encryption disabled" "${regx}" "$nb_instance"
|
||||
else
|
||||
textPass "${regx}: Sagemaker Notebook instance $nb_instance has data encryption enabled" "${regx}" "$nb_instance"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "${regx}: No Sagemaker Notebook instances found" "${regx}"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,58 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
# Remediation:
|
||||
#
|
||||
# https://www.cloudconformity.com/knowledge-base/aws/RDS/instance-deletion-protection.html
|
||||
# https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/Overview.DBInstance.Modifying.html
|
||||
#
|
||||
# aws rds modify-db-instance \
|
||||
# --region us-east-1 \
|
||||
# --db-instance-identifier test-db \
|
||||
# --deletion-protection \
|
||||
# [--apply-immediately | --no-apply-immediately]
|
||||
|
||||
CHECK_ID_extra7113="7.113"
|
||||
CHECK_TITLE_extra7113="[extra7113] Check if RDS instances have deletion protection enabled "
|
||||
CHECK_SCORED_extra7113="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7113="EXTRA"
|
||||
CHECK_SEVERITY_extra7113="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7113="AwsRdsDbInstance"
|
||||
CHECK_ALTERNATE_check7113="extra7113"
|
||||
CHECK_SERVICENAME_extra7113="rds"
|
||||
CHECK_RISK_extra7113='You can only delete instances that do not have deletion protection enabled.'
|
||||
CHECK_REMEDIATION_extra7113='Enable deletion protection using the AWS Management Console for production DB instances.'
|
||||
CHECK_DOC_extra7113='https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/USER_DeleteInstance.html'
|
||||
CHECK_CAF_EPIC_extra7113='Data Protection'
|
||||
|
||||
extra7113(){
|
||||
for regx in $REGIONS; do
|
||||
LIST_OF_RDS_INSTANCES=$($AWSCLI rds describe-db-instances $PROFILE_OPT --region $regx --query "DBInstances[?Engine != 'docdb'].DBInstanceIdentifier" --output text 2>&1)
|
||||
if [[ $(echo "$LIST_OF_RDS_INSTANCES" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to describe DB instances" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_OF_RDS_INSTANCES ]];then
|
||||
for rdsinstance in $LIST_OF_RDS_INSTANCES; do
|
||||
IS_DELETIONPROTECTION=$($AWSCLI rds describe-db-instances $PROFILE_OPT --region $regx --db-instance-identifier $rdsinstance --query 'DBInstances[*].DeletionProtection' --output text)
|
||||
if [[ $IS_DELETIONPROTECTION == "False" ]]; then
|
||||
textFail "$regx: RDS instance $rdsinstance deletion protection is not enabled!" "$regx" "$rdsinstance"
|
||||
else
|
||||
textPass "$regx: RDS instance $rdsinstance deletion protection is enabled" "$regx" "$rdsinstance"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: No RDS instances found" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,55 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7114="7.114"
|
||||
CHECK_TITLE_extra7114="[extra7114] Check if Glue development endpoints have S3 encryption enabled."
|
||||
CHECK_SCORED_extra7114="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7114="EXTRA"
|
||||
CHECK_SEVERITY_extra7114="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7114="AwsGlue"
|
||||
CHECK_ALTERNATE_check7114="extra7114"
|
||||
CHECK_SERVICENAME_extra7114="glue"
|
||||
CHECK_RISK_extra7114='Data exfiltration could happen if information is not protected. KMS keys provide additional security level to IAM policies.'
|
||||
CHECK_REMEDIATION_extra7114='Specify AWS KMS keys to use for input and output from S3 and EBS.'
|
||||
CHECK_DOC_extra7114='https://docs.aws.amazon.com/glue/latest/dg/encryption-security-configuration.html'
|
||||
CHECK_CAF_EPIC_extra7114='Data Protection'
|
||||
|
||||
extra7114(){
|
||||
for regx in $REGIONS; do
|
||||
LIST_EP_SC=$($AWSCLI glue get-dev-endpoints $PROFILE_OPT --region $regx --query 'DevEndpoints[*].{Name:EndpointName,Security:SecurityConfiguration}' --output json 2>&1)
|
||||
if [[ $(echo "$LIST_EP_SC" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to get dev endpoints" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_EP_SC != '[]' ]]; then
|
||||
for ep in $(echo "${LIST_EP_SC}"| jq -r '.[] | @base64');do
|
||||
ENDPOINT_NAME=$(echo $ep | base64 --decode | jq -r '.Name')
|
||||
ENDPOINT_SC=$(echo $ep | base64 --decode | jq -r '.Security // empty')
|
||||
if [[ ! -z "$ENDPOINT_SC" ]]; then
|
||||
ENDPOINT_SC_ENCRYPTION=$($AWSCLI glue get-security-configuration --name "${ENDPOINT_SC}" $PROFILE_OPT --region $regx --query 'SecurityConfiguration.EncryptionConfiguration.S3Encryption[0].S3EncryptionMode' --output text)
|
||||
if [[ "$ENDPOINT_SC_ENCRYPTION" == "DISABLED" ]]; then
|
||||
textFail "$regx: Glue development endpoint $ENDPOINT_NAME does not have S3 encryption enabled!" "$regx" "$ENDPOINT_NAME"
|
||||
else
|
||||
textPass "$regx: Glue development endpoint $ENDPOINT_NAME has S3 encryption enabled" "$regx" "$ENDPOINT_NAME"
|
||||
fi
|
||||
else
|
||||
textFail "$regx: Glue development endpoint $ENDPOINT_NAME does not have security configuration" "$regx" "$ENDPOINT_NAME"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: There are no Glue development endpoints" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
|
||||
|
||||
@@ -1,47 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra7115="7.115"
|
||||
CHECK_TITLE_extra7115="[extra7115] Check if Glue database connection has SSL connection enabled."
|
||||
CHECK_SCORED_extra7115="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7115="EXTRA"
|
||||
CHECK_SEVERITY_extra7115="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7115="AwsGlue"
|
||||
CHECK_ALTERNATE_check7115="extra7115"
|
||||
CHECK_SERVICENAME_extra7115="glue"
|
||||
CHECK_RISK_extra7115='Data exfiltration could happen if information is not protected in transit.'
|
||||
CHECK_REMEDIATION_extra7115='Configure encryption settings for crawlers; ETL jobs; and development endpoints using security configurations in AWS Glue.'
|
||||
CHECK_DOC_extra7115='https://docs.aws.amazon.com/glue/latest/dg/encryption-in-transit.html'
|
||||
CHECK_CAF_EPIC_extra7115='Data Protection'
|
||||
|
||||
extra7115(){
|
||||
for regx in $REGIONS; do
|
||||
CONNECTION_LIST=$($AWSCLI glue get-connections $PROFILE_OPT --region $regx --output json --query 'ConnectionList[*].{Name:Name,SSL:ConnectionProperties.JDBC_ENFORCE_SSL}' 2>&1)
|
||||
if [[ $(echo "$CONNECTION_LIST" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to get connections" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $CONNECTION_LIST != '[]' ]]; then
|
||||
for connection in $(echo "${CONNECTION_LIST}" | jq -r '.[] | @base64'); do
|
||||
CONNECTION_NAME=$(echo $connection | base64 --decode | jq -r '.Name' )
|
||||
CONNECTION_SSL_STATE=$(echo $connection | base64 --decode | jq -r '.SSL')
|
||||
if [[ "$CONNECTION_SSL_STATE" == "false" ]]; then
|
||||
textFail "$regx: Glue connection $CONNECTION_NAME has SSL connection disabled" "$regx" "$CONNECTION_NAME"
|
||||
else
|
||||
textPass "$regx: Glue connection $CONNECTION_NAME has SSL connection enabled" "$regx" "$CONNECTION_NAME"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: There are no Glue connections" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,44 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra7116="7.116"
|
||||
CHECK_TITLE_extra7116="[extra7116] Check if Glue data catalog settings have metadata encryption enabled."
|
||||
CHECK_SCORED_extra7116="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7116="EXTRA"
|
||||
CHECK_SEVERITY_extra7116="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7116="AwsGlue"
|
||||
CHECK_ALTERNATE_check7116="extra7116"
|
||||
CHECK_SERVICENAME_extra7116="glue"
|
||||
CHECK_RISK_extra7116='If not enabled sensitive information at rest is not protected.'
|
||||
CHECK_REMEDIATION_extra7116='Enable Encryption. Use a CMK where possible. It will provide additional management and privacy benefits.'
|
||||
CHECK_DOC_extra7116='https://docs.aws.amazon.com/glue/latest/dg/encrypt-glue-data-catalog.html'
|
||||
CHECK_CAF_EPIC_extra7116='Data Protection'
|
||||
|
||||
extra7116(){
|
||||
for regx in $REGIONS; do
|
||||
TABLE_LIST=$($AWSCLI glue search-tables --max-results 1 $PROFILE_OPT --region $regx --output text --query 'TableList[*]' 2>&1)
|
||||
if [[ $(echo "$TABLE_LIST" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to search tables" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ ! -z $TABLE_LIST ]]; then
|
||||
METADATA_ENCRYPTED=$($AWSCLI glue get-data-catalog-encryption-settings $PROFILE_OPT --region $regx --output text --query "DataCatalogEncryptionSettings.EncryptionAtRest.CatalogEncryptionMode")
|
||||
if [[ "$METADATA_ENCRYPTED" == "DISABLED" ]]; then
|
||||
textFail "$regx: Glue data catalog settings have metadata encryption disabled" "$regx"
|
||||
else
|
||||
textPass "$regx: Glue data catalog settings have metadata encryption enabled" "$regx"
|
||||
fi
|
||||
else
|
||||
textInfo "$regx: Glue data catalog settings metadata encryption does not apply since there are no tables" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,44 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra7117="7.117"
|
||||
CHECK_TITLE_extra7117="[extra7117] Check if Glue data catalog settings have encrypt connection password enabled."
|
||||
CHECK_SCORED_extra7117="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7117="EXTRA"
|
||||
CHECK_SEVERITY_extra7117="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7117="AwsGlue"
|
||||
CHECK_ALTERNATE_check7117="extra7117"
|
||||
CHECK_SERVICENAME_extra7117="glue"
|
||||
CHECK_RISK_extra7117='If not enabled sensitive information at rest is not protected.'
|
||||
CHECK_REMEDIATION_extra7117='On the AWS Glue console; you can enable this option on the Data catalog settings page.'
|
||||
CHECK_DOC_extra7117='https://docs.aws.amazon.com/glue/latest/dg/encrypt-connection-passwords.html'
|
||||
CHECK_CAF_EPIC_extra7117='Data Protection'
|
||||
|
||||
extra7117(){
|
||||
for regx in $REGIONS; do
|
||||
CONNECTION_LIST=$($AWSCLI glue get-connections $PROFILE_OPT --region $regx --output text --query 'ConnectionList[*]' 2>&1)
|
||||
if [[ $(echo "$CONNECTION_LIST" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to get connections" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ ! -z $CONNECTION_LIST ]]; then
|
||||
METADATA_ENCRYPTED=$($AWSCLI glue get-data-catalog-encryption-settings $PROFILE_OPT --region $regx --output text --query "DataCatalogEncryptionSettings.ConnectionPasswordEncryption.ReturnConnectionPasswordEncrypted")
|
||||
if [[ "$METADATA_ENCRYPTED" == "False" ]]; then
|
||||
textFail "$regx: Glue data catalog connection password is not encrypted" "$regx"
|
||||
else
|
||||
textPass "$regx: Glue data catalog connection password is encrypted" "$regx"
|
||||
fi
|
||||
else
|
||||
textInfo "$regx: Glue data catalog connection password encryption does not apply since there are no connections" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,59 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
CHECK_ID_extra7118="7.118"
|
||||
CHECK_TITLE_extra7118="[extra7118] Check if Glue ETL Jobs have S3 encryption enabled."
|
||||
CHECK_SCORED_extra7118="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7118="EXTRA"
|
||||
CHECK_SEVERITY_extra7118="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7118="AwsGlue"
|
||||
CHECK_ALTERNATE_check7118="extra7118"
|
||||
CHECK_SERVICENAME_extra7118="glue"
|
||||
CHECK_RISK_extra7118='If not enabled sensitive information at rest is not protected.'
|
||||
CHECK_REMEDIATION_extra7118='Provide the encryption properties that are used by crawlers; jobs; and development endpoints.'
|
||||
CHECK_DOC_extra7118='https://docs.aws.amazon.com/glue/latest/dg/console-security-configurations.html'
|
||||
CHECK_CAF_EPIC_extra7118='Data Protection'
|
||||
|
||||
extra7118(){
|
||||
for regx in $REGIONS; do
|
||||
JOB_LIST=$($AWSCLI glue get-jobs $PROFILE_OPT --region $regx --output json --query 'Jobs[*].{Name:Name,SecurityConfiguration:SecurityConfiguration,JobEncryption:DefaultArguments."--encryption-type"}' 2>&1)
|
||||
if [[ $(echo "$JOB_LIST" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to get jobs" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $JOB_LIST != '[]' ]]; then
|
||||
for job in $(echo "${JOB_LIST}" | jq -r '.[] | @base64'); do
|
||||
JOB_NAME=$(echo $job | base64 --decode | jq -r '.Name')
|
||||
SECURITY_CONFIGURATION=$(echo $job | base64 --decode | jq -r '.SecurityConfiguration // empty')
|
||||
JOB_ENCRYPTION=$(echo $job | base64 --decode | jq -r '.JobEncryption // empty')
|
||||
if [[ ! -z "$SECURITY_CONFIGURATION" ]]; then
|
||||
S3_ENCRYPTION=$($AWSCLI glue get-security-configuration --name "${SECURITY_CONFIGURATION}" $PROFILE_OPT --region $regx --output text --query 'SecurityConfiguration.EncryptionConfiguration.S3Encryption[0].S3EncryptionMode')
|
||||
if [[ "$S3_ENCRYPTION" == "DISABLED" ]]; then
|
||||
if [[ ! -z "$JOB_ENCRYPTION" ]]; then
|
||||
textPass "$regx: Glue job $JOB_NAME does have $JOB_ENCRYPTION for S3 encryption enabled" "$regx" "$JOB_NAME"
|
||||
else
|
||||
textFail "$regx: Glue job $JOB_NAME does not have S3 encryption enabled" "$regx" "$JOB_NAME"
|
||||
fi
|
||||
else
|
||||
textPass "$regx: Glue job $JOB_NAME does have $S3_ENCRYPTION for S3 encryption enabled" "$regx" "$JOB_NAME"
|
||||
fi
|
||||
elif [[ ! -z "$JOB_ENCRYPTION" ]]; then
|
||||
textPass "$regx: Glue job $JOB_NAME does have $JOB_ENCRYPTION for S3 encryption enabled" "$regx" "$JOB_NAME"
|
||||
else
|
||||
textFail "$regx: Glue job $JOB_NAME does not have S3 encryption enabled" "$regx" "$JOB_NAME"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: There are no Glue jobs" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
@@ -1,53 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# Prowler - the handy cloud security tool (copyright 2018) by Toni de la Fuente
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License"); you may not
|
||||
# use this file except in compliance with the License. You may obtain a copy
|
||||
# of the License at http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software distributed
|
||||
# under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR
|
||||
# CONDITIONS OF ANY KIND, either express or implied. See the License for the
|
||||
# specific language governing permissions and limitations under the License.
|
||||
|
||||
CHECK_ID_extra7119="7.119"
|
||||
CHECK_TITLE_extra7119="[extra7119] Check if Glue development endpoints have CloudWatch logs encryption enabled."
|
||||
CHECK_SCORED_extra7119="NOT_SCORED"
|
||||
CHECK_CIS_LEVEL_extra7119="EXTRA"
|
||||
CHECK_SEVERITY_extra7119="Medium"
|
||||
CHECK_ASFF_RESOURCE_TYPE_extra7119="AwsGlue"
|
||||
CHECK_ALTERNATE_check7119="extra7119"
|
||||
CHECK_SERVICENAME_extra7119="glue"
|
||||
CHECK_RISK_extra7119='If not enabled sensitive information at rest is not protected.'
|
||||
CHECK_REMEDIATION_extra7119='Enable Encryption in the Security configurations.'
|
||||
CHECK_DOC_extra7119='https://docs.aws.amazon.com/glue/latest/dg/console-security-configurations.html'
|
||||
CHECK_CAF_EPIC_extra7119='Logging and Monitoring'
|
||||
|
||||
extra7119(){
|
||||
for regx in $REGIONS; do
|
||||
LIST_EP_SC=$($AWSCLI glue get-dev-endpoints $PROFILE_OPT --region $regx --query 'DevEndpoints[*].{Name:EndpointName,Security:SecurityConfiguration}' --output json 2>&1)
|
||||
if [[ $(echo "$LIST_EP_SC" | grep -E 'AccessDenied|UnauthorizedOperation|AuthorizationError') ]]; then
|
||||
textInfo "$regx: Access Denied trying to get dev endpoints" "$regx"
|
||||
continue
|
||||
fi
|
||||
if [[ $LIST_EP_SC != '[]' ]]; then
|
||||
for ep in $(echo "${LIST_EP_SC}"| jq -r '.[] | @base64');do
|
||||
ENDPOINT_NAME=$(echo $ep | base64 --decode | jq -r '.Name')
|
||||
ENDPOINT_SC=$(echo $ep | base64 --decode | jq -r '.Security // empty')
|
||||
if [[ ! -z "$ENDPOINT_SC" ]]; then
|
||||
ENDPOINT_SC_ENCRYPTION=$($AWSCLI glue get-security-configuration --name "${ENDPOINT_SC}" $PROFILE_OPT --region $regx --query 'SecurityConfiguration.EncryptionConfiguration.CloudWatchEncryption.CloudWatchEncryptionMode' --output text)
|
||||
if [[ $ENDPOINT_SC_ENCRYPTION == "DISABLED" ]]; then
|
||||
textFail "$regx: Glue development endpoint $ENDPOINT_NAME does not have CloudWatch logs encryption enabled!" "$regx" "$ENDPOINT_NAME"
|
||||
else
|
||||
textPass "$regx: Glue development endpoint $ENDPOINT_NAME has CloudWatch logs encryption enabled" "$regx" "$ENDPOINT_NAME"
|
||||
fi
|
||||
else
|
||||
textFail "$regx: Glue development endpoint $ENDPOINT_NAME does not have security configuration" "$regx" "$ENDPOINT_NAME"
|
||||
fi
|
||||
done
|
||||
else
|
||||
textInfo "$regx: There are no Glue development endpoints" "$regx"
|
||||
fi
|
||||
done
|
||||
}
|
||||
Some files were not shown because too many files have changed in this diff Show More
Reference in New Issue
Block a user